BloodHound

BloodHound is a powerful tool used by adversaries to visualize and analyze Active Directory relationships, allowing them to quickly identify and exploit potential attack paths and privilege escalation opportunities within a network. It automates the reconnaissance phase of an attack, helping attackers pinpoint weak points and ultimately compromise Active Directory environments.
Ingestion
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/bloodhound]
└─$ KRB5CCNAME=../l.clark@dc01.infiltrator.htb.ccache bloodhound-python -d INFILTRATOR.HTB -u l.clark -k -no-pass --auth-method kerberos -ns $IP -dc dc01.infiltrator.htb --zip -c ALL
INFO: Found AD domain: infiltrator.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 14 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: ATTACKERSYSTEM2.infiltrator.htb
INFO: Querying computer: dc01.infiltrator.htb
WARNING: Could not resolve: ATTACKERSYSTEM2.infiltrator.htb: The DNS query name does not exist: ATTACKERSYSTEM2.infiltrator.htb.
INFO: Done in 00M 05S
INFO: Compressing output into 20240901005953_bloodhound.zipIngestion Complete using the TGT of the l.clark user
Prep
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/bloodhound]
└─$ neo4j_kickstart
2024-09-01 10:59:58.192+0000 INFO Starting...
2024-09-01 10:59:58.478+0000 INFO This instance is ServerId{823c0986} (823c0986-8860-45ad-af0e-a0f1316bef16)
2024-09-01 10:59:59.265+0000 INFO ======== Neo4j 4.4.36 ========
2024-09-01 11:00:00.004+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2024-09-01 11:00:00.005+0000 INFO Updating the initial password in component 'security-users'
2024-09-01 11:00:00.086+0000 INFO Bolt enabled on localhost:7687.
2024-09-01 11:00:00.673+0000 INFO Remote interface available at http://localhost:7474/
2024-09-01 11:00:00.676+0000 INFO id: F22BE6505A50EE3B6AE80482B39DD2B6A7082E68C916A87DF6F1CD7ECA4DD942
2024-09-01 11:00:00.676+0000 INFO name: system
2024-09-01 11:00:00.677+0000 INFO creationDate: 2024-09-01T10:39:20.089Z
2024-09-01 11:00:00.677+0000 INFO Started.Starting neo4j
 Uploading the ingested data
Uploading the ingested data
Domain



l.clark




 The user is also part of the
The user is also part of the marketing_team group
 The
The l.clark user has the AllExtendedRights and WriteAccountRestrictions privileges over the attackersystem2.infiltrator.htb host
attackersystem2.infiltrator.htb




d.anderson





 The
The d.anderson user is part of both marketing_team and protected users groups
 The user has the GenericAll privilege over the
The user has the GenericAll privilege over the marketing digital OU
Marketing Digital
 The
The marketing digital OU contains the e.rodriguez user
e.rodriguez




 The
The e.rodriguez user is part of the digital_influencers group
 The user also has the AddSelf privilege over the
The user also has the AddSelf privilege over the chiefs marketing group
Chiefs Marketing
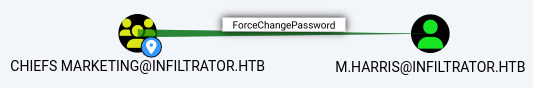 The
The chiefs marketing group has the ForceChangePassword privilege over the m.harris user
m.harris




 The
The m.harris user is part of developers, protected users, and remote management users groups
 Membership to the
Membership to the remote managemenet users group allows the user to PSRemote to the dc01.infiltrator.htb host
winrm_svc




 The
The winrm_svc account has memberships to the service_management and remote management users groups
 Which allows the user to WinRM to the
Which allows the user to WinRM to the dc01.infiltrator.htb host
o.martinez




 The
The o.martinez user is part of both Chiefs Marketing and Remote Desktop Users groups
 Which allows the user to RDP to the
Which allows the user to RDP to the dc01.infiltrator.htb host
lan_managment




 The
The lan_managment account has the ReadGMSAPassword privilege over the infiltrator_svc$ account
infiltrator_svc$





 The
The infiltrator_svc$ account is a managed service account that is part of the Domain Computers group