SUID
matt@pandora:~$ find / -perm -04000 -ls -type f 2>/dev/null
[...REDACTED...]
262929 20 -rwsr-x--- 1 root matt 16816 Dec 3 2021 /usr/bin/pandora_backup
[...REDACTED...]
matt@pandora:~$ find / -user root -group matt -ls -type f 2>/dev/null
262929 20 -rwsr-x--- 1 root matt 16816 Dec 3 2021 /usr/bin/pandora_backupThe custom SUID binary located at /usr/bin/pandora_backup was initially discovered earlier, but I was unable to enumerated it due to lack of privileges
Now that I have gain a session as the matt user from the lateral movement, I can proceed forward
matt@pandora:~$ file /usr/bin/pandora_backup
/usr/bin/pandora_backup: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7174c3b04737ad11254839c20c8dab66fce55af8, for GNU/Linux 3.2.0, not stripped
matt@pandora:~$ strings /usr/bin/pandora_backup
command 'strings' not found, but can be installed with:
apt install binutils
Please ask your administrator.
matt@pandora:~$ cat /usr/bin/pandora_backup
elf>�@0:@8
@@@@h���HHmm HH�-�=�=hp�-�=�=����DDP�td� � � <<Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNUqtðG7�%H9�
��f��Z�GNU
�
�e�m\ 4x � %"putssetreuidsystemgetuidgeteuid__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.2.5_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableFu�i P�p�0HH@�?�?�?�? �?
SH�=��&/�DH�=�/H��/H9�tH��.H��t@�����H�=Y/H�5R/H)�H��H��?H��H�H��tH��.H����fD���=/u/UH�=�.H��t�H���PTL��H�
H�=�.�-����h�����.]�����{���UH��SH�������������މ������H�=n����H�=�����H�=��������tH�=��d�����H�=��Q���H�=��E����H�]���f.�AWL�=�+AVI��AUI��ATA��UH�-�+SL)�H������H��t�L��L��D��A��H��H9�u�H�[]A\A]A^A_��H�H��PandoraFMS Backup UtilityNow attempting to backup PandoraFMS clienttar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*Backup failed!
Check your permissions!Backup successful!Terminating program!<(�������������X}�������h���8zRx
8���+zRx
$����`FJ
E�w �?�;*3$"D���$\�����A�C
D����]B�I�E �E(�D0�H8�G@j8A0A(B BB�(���p0F
d������80
�
@x� ������o����o���o����o�=6fvfvh@gcc: (Debian 10.2.1-6) 10.2.1 20210110��08�
�
��d � 8!�=�=�=�?@@@P@���
��!07P@C�=jpv�=������D"����=��=��=�� �@�
` � @@.?P@
dFYl��@@� �H@� �]�X@��+��P@u�
P@ 2"crtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrybackup.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTableputs@GLIBC_2.2.5_edatagetuid@GLIBC_2.2.5system@GLIBC_2.2.5geteuid@GLIBC_2.2.5__libc_start_main@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_initsetreuid@GLIBC_2.2.5__bss_startmain__TMC_END___ITM_registerTMCloneTable__cxa_finalize@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.plt.got.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.plt.data.bss.comment�#��$6�� D��No
V88�^���o��k���o��z�B���� `�����dd � �� � <�8!8������=�-��?��@�@@@P@P�0P0'x0`- �6M%9It is indeed a x64 ELF binary. The target system doesn’t have strings. I will just fire it up and see how it behaves Based on the naming, I would guess that this creates a backup archive for the Pandora FMS instance
matt@pandora:~$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
tar: Removing leading `/' from member names
/var/www/pandora/pandora_console/AUTHORS
tar: Removing leading `/' from hard link targets
[...REDACTED...]
Backup successful!
Terminating program!It claims to be PandoraFMS Backup Utility and seems to be using tar for archiving operation
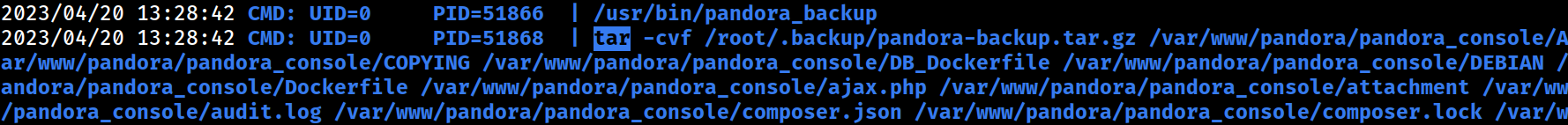 PSPY alco captured the whole operation in the background.
Tar was indeed called by the SUID binary for archiving, however it was called WITHOUT the absolute PATH
PSPY alco captured the whole operation in the background.
Tar was indeed called by the SUID binary for archiving, however it was called WITHOUT the absolute PATH
Path Hijacking is very much possible for privilege escalation