Web
Nmap discovered a Web server on the target port 80
The running service is nginx 1.24.0
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ curl -I http://$IP/
HTTP/1.1 301 Moved Permanently
Server: nginx/1.24.0
Date: Sun, 27 Oct 2024 02:32:17 GMT
Content-Type: text/html
Content-Length: 169
Connection: keep-alive
Location: http://university.htb/301 to http://university.htb/
This was already identified
 The
The /etc/hosts file on Kali has been updated
 Webroot
It appears to be an online learning platform
Webroot
It appears to be an online learning platform
 It’s a Django application
It’s a Django application
 There are many endpoints
There are many endpoints
Contact


 The
The /contact endpoint sends a POST request to itself
There is also the csrftoken header
This feature might be functional
Register
 There are 2 different types of registrations;
There are 2 different types of registrations;
- student
- professor
Student Registration

 It shows that the password is too common.
There appears to be a blacklist to check on common passwords
It shows that the password is too common.
There appears to be a blacklist to check on common passwords
 Using a stronger password and the web app return 302 to a login page at
Using a stronger password and the web app return 302 to a login page at /accounts/login
Professor Registration

 The professor registration appears to be requiring a validating from the staff
It does redirect to the same login page
The professor registration appears to be requiring a validating from the staff
It does redirect to the same login page
Login

 The login page is rather interesting as it supports authentication with a signed-certificate
The login page is rather interesting as it supports authentication with a signed-certificate
Authentication via Signed-Certificate

/accounts/login/SDC/ is the endpoint for authentication with a signed-certificate
It has a file upload feature
I will get back to this.
Using signed-certificate
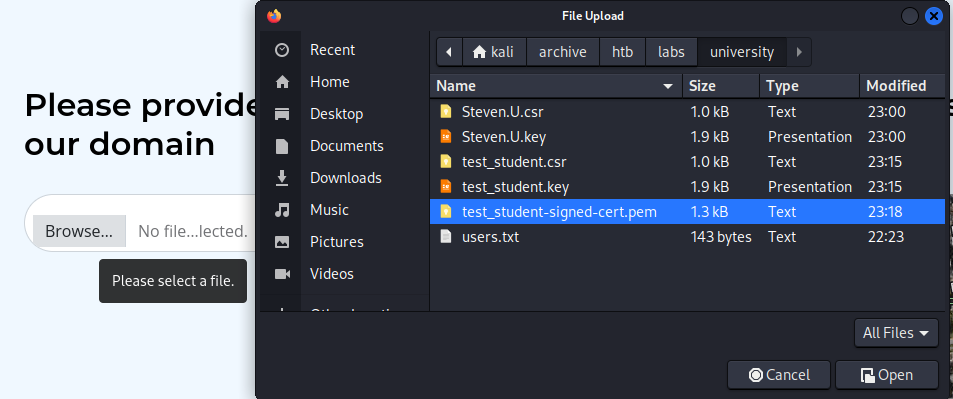 Uploading the signed-certificate file for the testing account
Uploading the signed-certificate file for the testing account
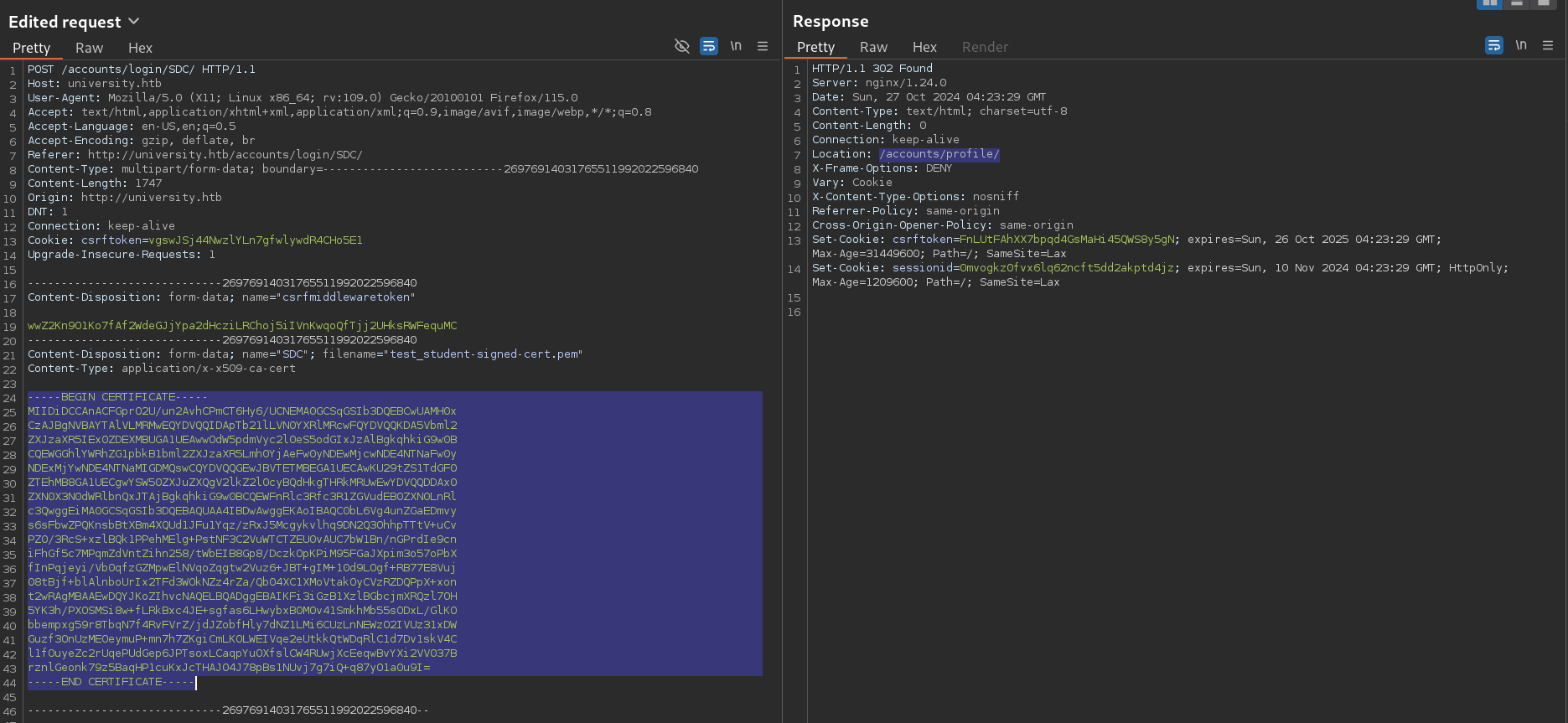
302 to /accounts/profile/
 Authenticated
Authenticated
Auth as test_student
 Authenticated as the testing student account
Authenticated as the testing student account
 It would appear that a signed-certificate can be requested using the following;
It would appear that a signed-certificate can be requested using the following;
$ openssl req -newkey rsa:2048 -keyout PK.key -out My-CSR.csr` It mentions that both
It mentions that both common name and email address attributes must match the username and email.
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ openssl req -newkey rsa:2048 -keyout test_student.key -out test_student.csr
.....+.............+............+...+...........+++++++++++++++++++++++++++++++++++++++*.+...+...+....+.....+..........+.........+..+....+.....+.........+......+.........+....+..+...+............+.+++++++++++++++++++++++++++++++++++++++*..+....................+.+.....+...+............+..........+...+..+......+.........+...............+.........+.+........+...+...+.......+..+.+.....+............+...................+...+..+.+........+....+......+..+....+...+........+............+......+.+......+..+.+......+......+..+.+......+.....+.........+...............+......+.............+...........+.+..................+...+...+.....+..........+......+...........+...+.......+...+.....................+........+..........+...+..+.+.........+..+...+......+.+......+..+.+...........+.........+..........+..+...+....+..+...............++++++
.....+.........+........+++++++++++++++++++++++++++++++++++++++*..+.........+..+...+.......+++++++++++++++++++++++++++++++++++++++*.+..+.......+...+..+...+...+.......+.................+..........+...........+.+......+........+.......+.....+.......+..+.............+.....+......+......+....+......+.....+......+...+......+...............++++++
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:test_student
Email Address []:test_student@test.test
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:Generated a RSA key pair; test_student.key and test_student.csr

 Submitting
Submitting

 The web app returned
The web app returned 200 with a signed-certificate file; signed-cert.pem
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ mv signed-cert.pem test_student-signed-cert.pemChanging the filename; test_student-signed-cert.pem
I should be able to use this file to authenticate
Courses
 Checking the courses reveals many courses, supposedly written by professors
Checking the courses reveals many courses, supposedly written by professors
 Clicking into one of the professors reveals the details about the professors
Possible username disclosure;
Clicking into one of the professors reveals the details about the professors
Possible username disclosure; nya.laracrof
This one is located at /accounts/profile/visit/6/
 There is also george lantern
There is also george lantern
 carol helgen
carol helgen
 nour qasso
nour qasso
 martin rose
martin rose
 steven universe
steven universe

9 is the testing student account

10 is the testing professor account
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ cat users.txt
hana
nya
nya.laracrof
n.laracrof
george
george.lantern
g.lantern
carol
carol.helgen
c.helgen
nour
nour.qasso
n.qasso
martin
martin.rose
m.rose
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ nano users.txt
┌──(kali㉿kali)-[~/archive/htb/labs/university]
└─$ kerbrute userenum --dc dc.university.htb -d UNIVERSITY.HTB ./users.txt -t 200
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 10/26/24 - Ronnie Flathers @ropnop
2024/10/26 22:23:53 > Using KDC(s):
2024/10/26 22:23:53 > dc.university.htb:88
2024/10/26 22:23:53 > [+] VALID USERNAME: hana@UNIVERSITY.HTB
2024/10/26 22:23:53 > Done! Tested 16 usernames (1 valid) in 0.026 secondsNone of those users are valid domain users
Fuzzing

 There is a profile export feature, which leads to
There is a profile export feature, which leads to /accounts/profile/pdf/
 Clicking into it sends a GET request to the endpoint.
Returned data reveals that it uses ReportLab for PDF generation
Clicking into it sends a GET request to the endpoint.
Returned data reveals that it uses ReportLab for PDF generation
 This is the generated PDF file.
Fields are corresponding to that of the profile page
This is the generated PDF file.
Fields are corresponding to that of the profile page
Metadata
 Checking the metadata reveals that it use xhtml2pdf to convert HTML to PDF
Checking the metadata reveals that it use xhtml2pdf to convert HTML to PDF
xhtml2pdf
 xhtml2pdf uses ReportLab for PDF generation
xhtml2pdf uses ReportLab for PDF generation
Vulnerability
 ReportLab is a Python library used for creating PDFs programmatically. It supports complex layouts, graphics, and custom fonts, making it suitable for generating dynamic reports and documents. With tools for drawing shapes, tables, and charts, it’s widely used for automating PDF creation in business and web applications.
ReportLab is a Python library used for creating PDFs programmatically. It supports complex layouts, graphics, and custom fonts, making it suitable for generating dynamic reports and documents. With tools for drawing shapes, tables, and charts, it’s widely used for automating PDF creation in business and web applications.
 Looking it up online for vulnerability reveals CVE-2023-33733
Looking it up online for vulnerability reveals CVE-2023-33733