BloodHound
BloodHound is a powerful tool used by adversaries to visualize and analyze Active Directory relationships, allowing them to quickly identify and exploit potential attack paths and privilege escalation opportunities within a network. It automates the reconnaissance phase of an attack, helping attackers pinpoint weak points and ultimately compromise Active Directory environments.
Python Ingestor
┌──(kali㉿kali)-[~/…/htb/labs/timelapse/bloodhound]
└─$ KRB5CCNAME=../svc_deploy@dc01.timelapse.htb.ccache bloodhound-python -d TIMELAPSE.HTB -u svc_deploy -k -no-pass -dc dc01.timelapse.htb --dns-tcp -ns $IP --zip -c All
INFO: Found AD domain: timelapse.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc01.timelapse.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 4 computers
INFO: Connecting to LDAP server: dc01.timelapse.htb
INFO: Found 11 users
INFO: Found 55 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: dc01.timelapse.htb
INFO: Ignoring host dc01.timelapse.htb since its reported name does not match
INFO: Done in 00M 13S
INFO: Compressing output into 20231025073136_bloodhound.zipUsing the Python implementation of BloodHound ingestor with the TGT of the svc_deploy account, I can pull out all the domain information
Prep
┌──(kali㉿kali)-[~/…/htb/labs/timelapse/bloodhound]
└─$ sudo neo4j console
directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/…/htb/labs/timelapse/bloodhound]
└─$ bloodhoundStarting up neo4j and bloodhound
 Ingested domain data has been uploaded
Ingested domain data has been uploaded
svc_deploy
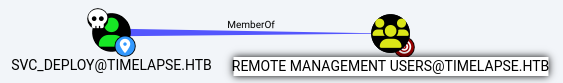 The
The svc_deploy account also has the membership to the Remote Management Users group.
This was already picked up by ldapdomaindump earlier
ReadLAPSPassword
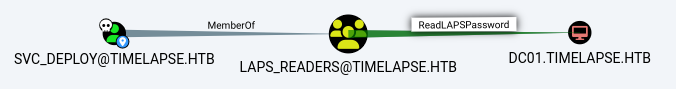 as expected at this point, the
as expected at this point, the svc_deploy account has a transitive readlapspassword privileges to the DC01 host
This appears to be the direct route to compromise the target domain
Domain Admins
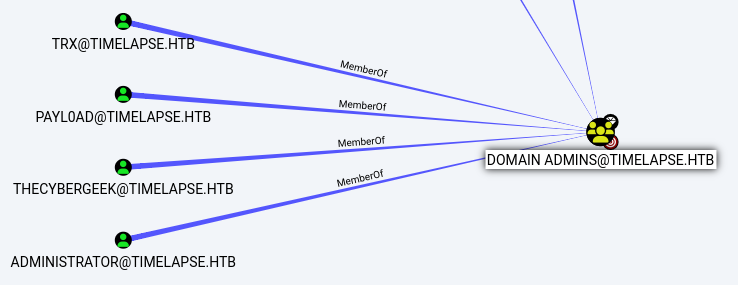 Although there are 3 additional domain users with memberships to the
Although there are 3 additional domain users with memberships to the Domain Admins Group, there appears to be no direct route to them
Domain Computers
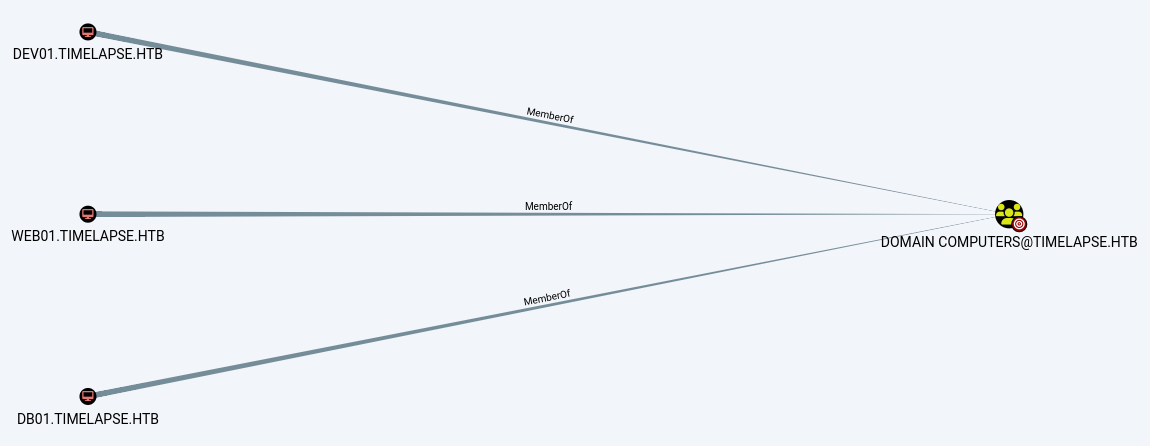 Those 3 additional computer accounts appear to be out of reach
As discovered previously, there aren’t any network address assigned to them
Those 3 additional computer accounts appear to be out of reach
As discovered previously, there aren’t any network address assigned to them