Web
Nmap discovered a web service on the target port 55555
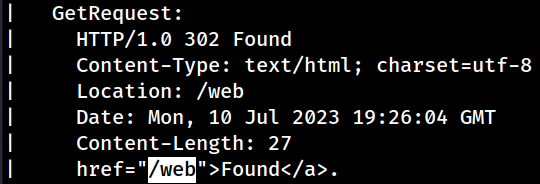 While Nmap was unable to identify the specific web technology, the web server itself is pointing to an endpoint at
While Nmap was unable to identify the specific web technology, the web server itself is pointing to an endpoint at /web
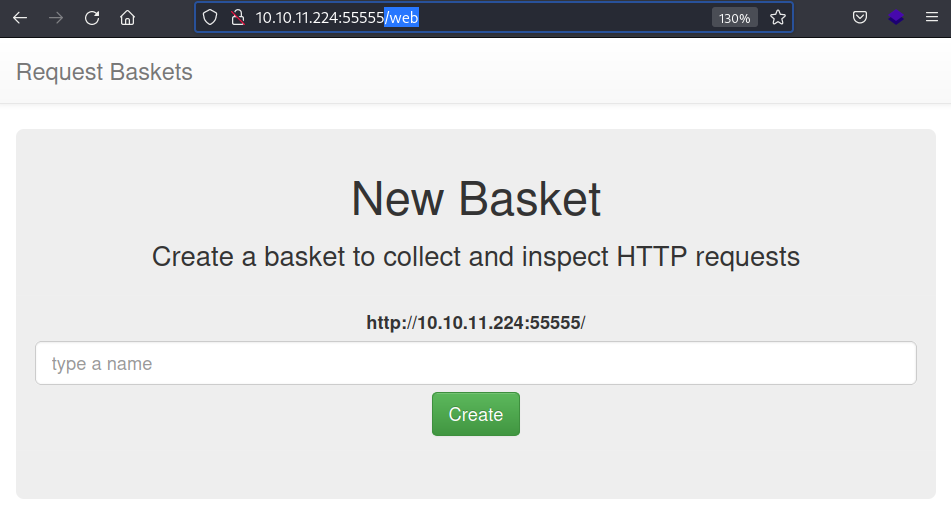 The
The /web page seems to be hosting a service
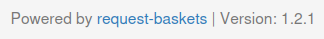 the footer reveals that the application is request-baskets 1.2.1
the footer reveals that the application is request-baskets 1.2.1
 the application is an open source project available via the github page
According to the description, the application is a web service to collect arbitrary HTTP requests and inspect them via RESTful API or simple web UI
the application is an open source project available via the github page
According to the description, the application is a web service to collect arbitrary HTTP requests and inspect them via RESTful API or simple web UI
Features
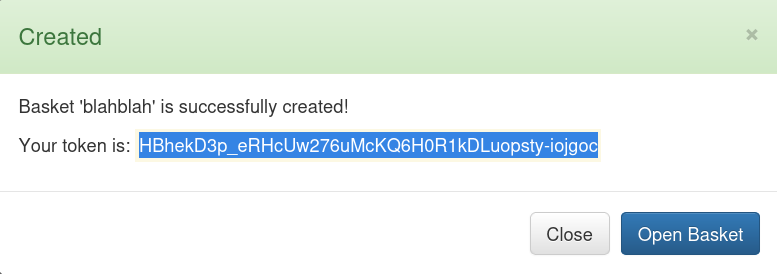 Upon creating a new “basket”, I am given a token
Upon creating a new “basket”, I am given a token
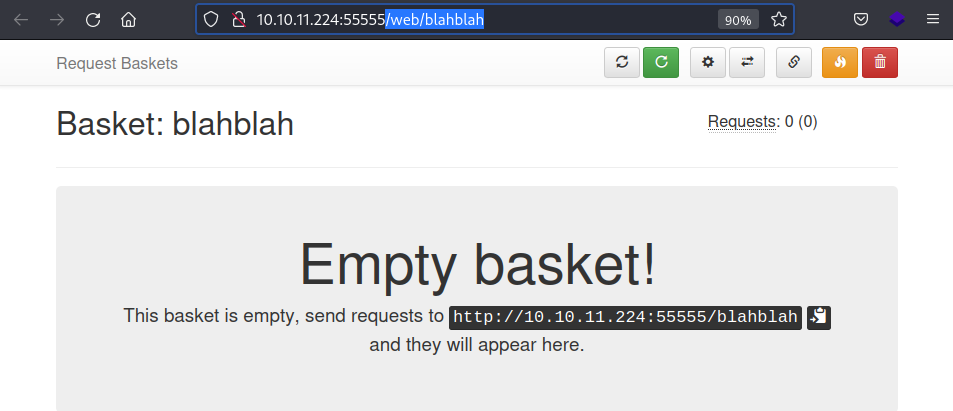 It states that all the request to the created endpoint (
It states that all the request to the created endpoint (/blahblah), will be captured
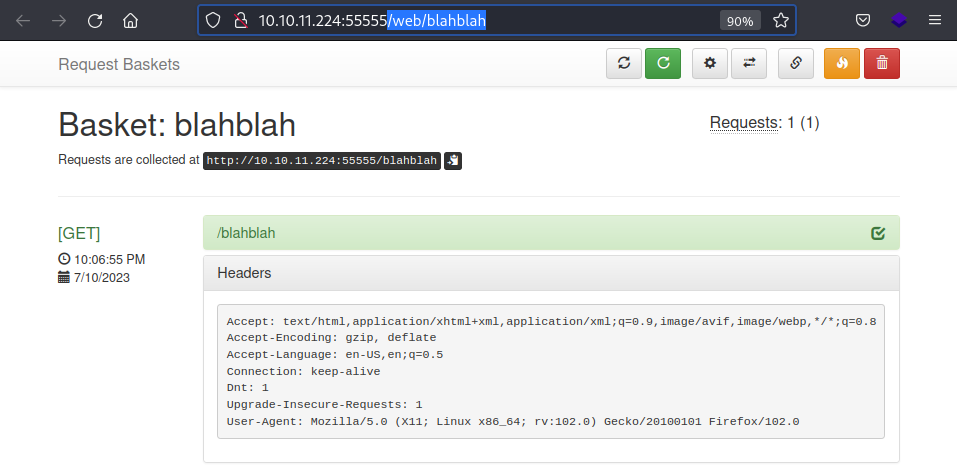 It indeed captured my GET request to the created endpoint and displayed the header information
It indeed captured my GET request to the created endpoint and displayed the header information
response

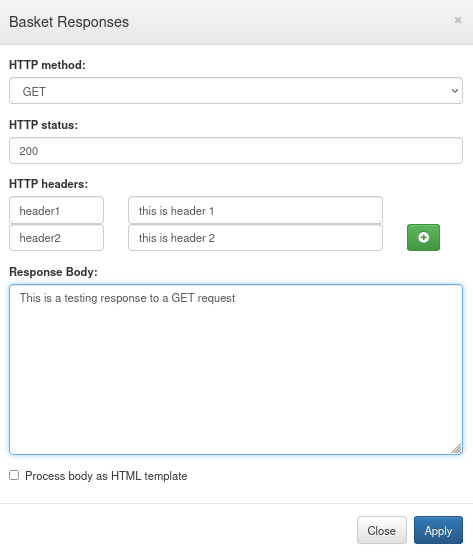
 One of the buttons in the header allows me to configure the response
One of the buttons in the header allows me to configure the response
┌──(kali㉿kali)-[~/archive/htb/labs/sau]
└─$ curl -i http://$IP:55555/blahblah
HTTP/1.1 200 OK
header1: this is header 1
header2: this is header 2
date: Mon, 10 Jul 2023 20:14:49 GMT
content-length: 43
content-type: text/plain; charset=utf-8
This is a testing response to a GET requestIt indeed works
proxy

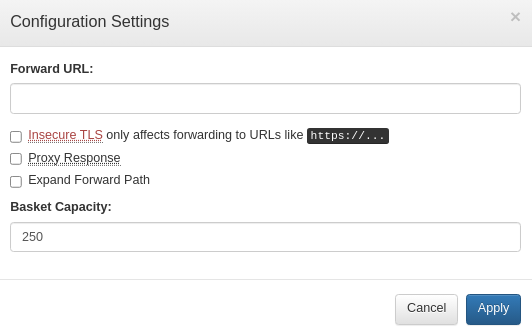 It appear that the web application is capable of functioning as a proxy as it allows me to set the forward URL
The Proxy Sesponse option seem to be setting whether or not if it would return the response as well
It appear that the web application is capable of functioning as a proxy as it allows me to set the forward URL
The Proxy Sesponse option seem to be setting whether or not if it would return the response as well
This could be vulnerable to SSRF I will first test out the proxy feature.
┌──(kali㉿kali)-[~/archive/htb/labs/sau]
└─$ echo 'testing abc abc abc' > test2.txt
┌──(kali㉿kali)-[~/archive/htb/labs/sau]
└─$ simplehttp . 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...I will first create a testing file (test2.txtd) with some content in it and serve it over HTTP on Kali
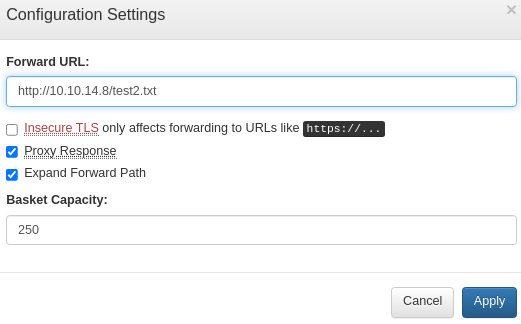 Then I will set the proxy configuration as above
By setting it up this way, requests to the created endpoint (
Then I will set the proxy configuration as above
By setting it up this way, requests to the created endpoint (/test2), will be forwarded to the Kali’s web server, hosting the testing file (test2.txt)
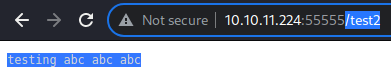 Confirmed.
Confirmed.
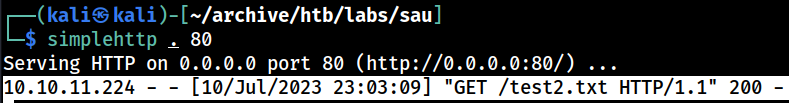 Kali’s web server also logged the GET request made by the target web application
Kali’s web server also logged the GET request made by the target web application
Vulnerability
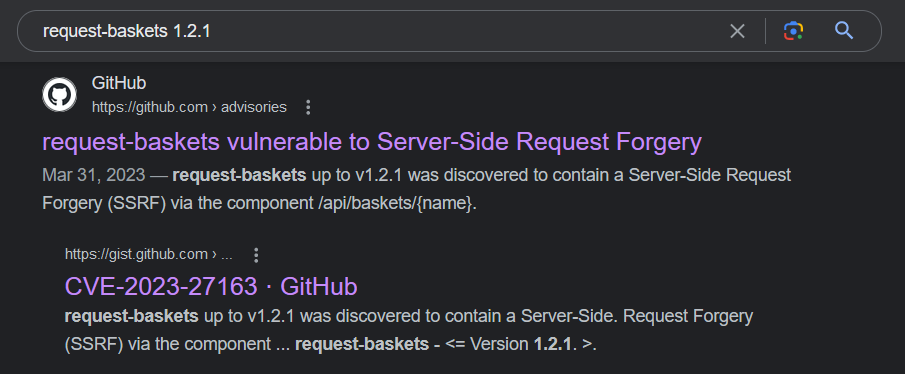 Looking up the target web app instance for vulnerability reveals that it’s indeed suffering from a SSRF vulnerability; [[Sau_CVE-2023-27163#[CVE-2023-27163](https //nvd.nist.gov/vuln/detail/CVE-2023-27163)|CVE-2023-27163]]
Looking up the target web app instance for vulnerability reveals that it’s indeed suffering from a SSRF vulnerability; [[Sau_CVE-2023-27163#[CVE-2023-27163](https //nvd.nist.gov/vuln/detail/CVE-2023-27163)|CVE-2023-27163]]