2nd Order SQLi
The /home,php file is apparently vulnerable to SQLi
2nd order SQL injection, also known as “stored” or “persistent” SQL injection, is a type of SQL injection attack that occurs when an attacker is able to inject malicious code into a web application, which is then stored in the database and later executed when the data is retrieved.
In a typical SQL injection attack, an attacker injects malicious code directly into a web application’s input fields (such as a login form) in order to exploit a vulnerability in the application’s SQL code. However, in a 2nd order SQL injection attack, the attacker is able to inject malicious code into a web application’s input fields, which is then STORED in the database and executed later when the data is retrieved by another user or application.
Following the theory above, I will be performing SQLi into the username field of the signup page So that the injected SQL poison will be “stored” in the backend database for later use (login)
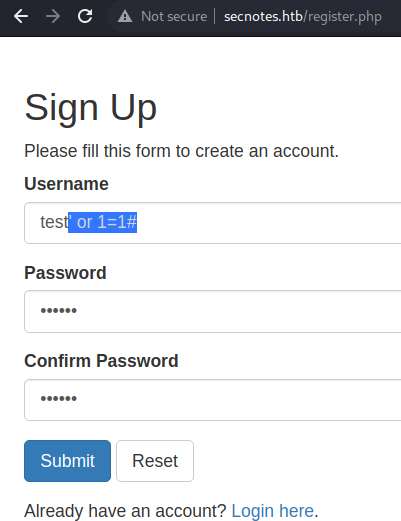 Injecting
Injecting 'or 1=1#, to turn the result of the SQL query in the /login.php file to TRUE
Authentication Bypass
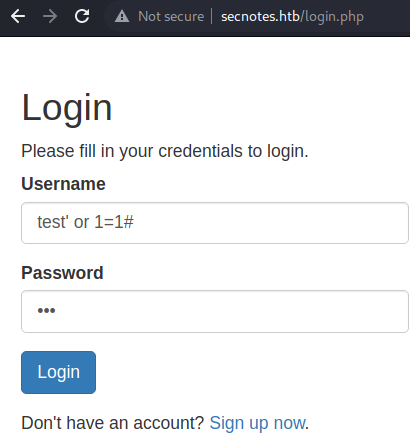 Logging in with the “stored” SQLi
Logging in with the “stored” SQLi
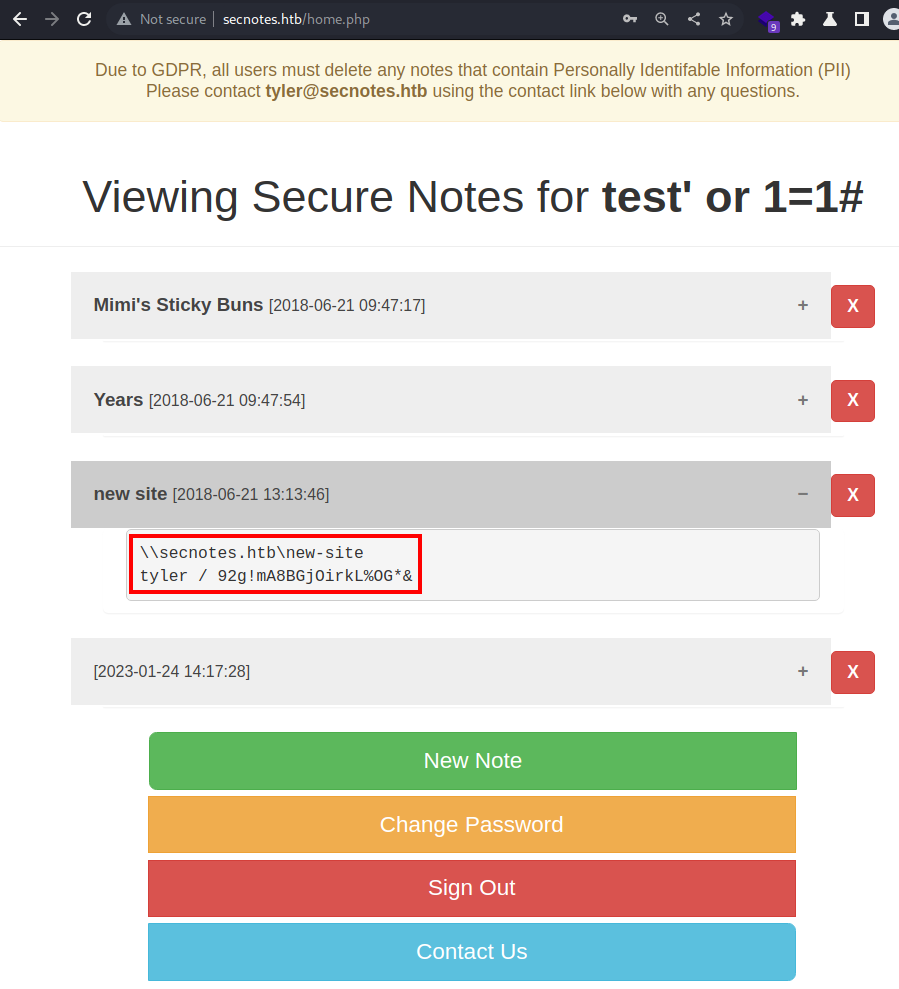 Because the
Because the 'or 1=1# SQLi has set the result of the SQL query in the /login.php file to TRUE, it resulted revealing everyone’s notes.
In the layman’s term, I am logged in as EVERYONE.
There is the SMB credential.