Virtual Host
After reviewing the result of the SQLi, I was unable to proceed forward as I failed to crack the password hashes
Then, I initially thought of accessing the web server endpoint running on the port 8000 through SQLi, but quickly dismissed it after realizing that it may not be possible with boolean/error based SQLi
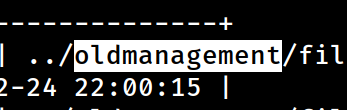 I remember seeing this new path in the avatar field;
I remember seeing this new path in the avatar field; oldmanagement
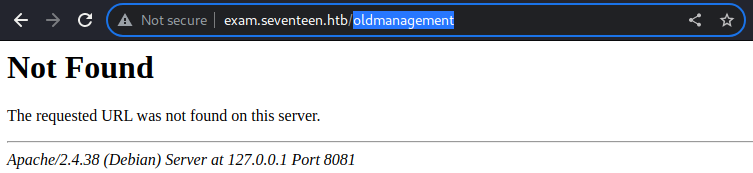
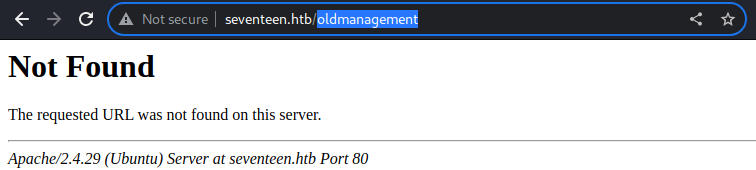 It was not available in the web server on the port
It was not available in the web server on the port 80
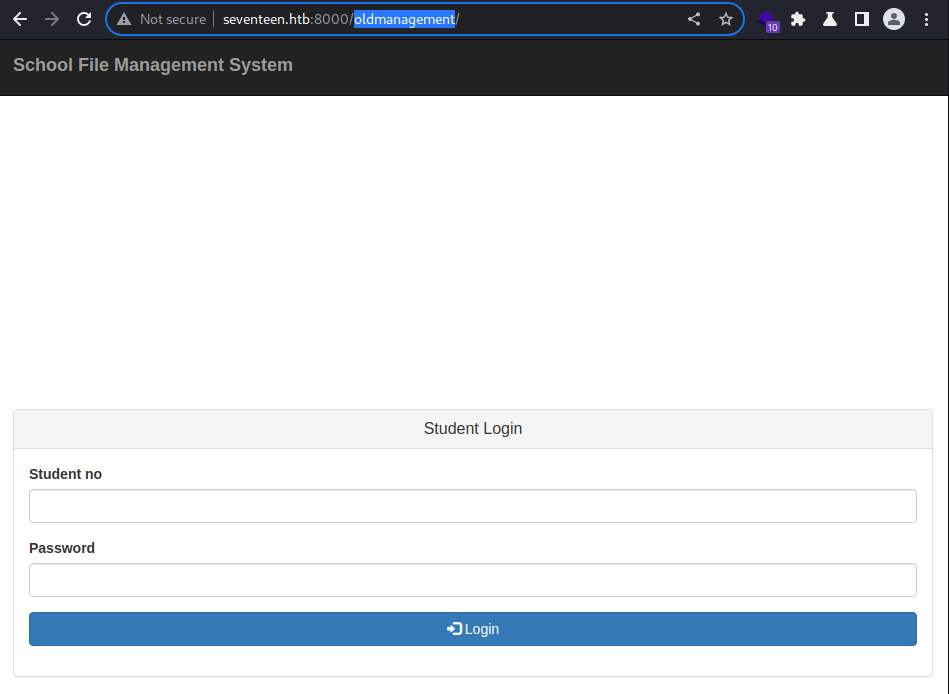 However, the endpoint is present at the web server running on the port
However, the endpoint is present at the web server running on the port 8000
Additionally, that could be a virtual host as web servers in Linux are mostly hosted at /var/www
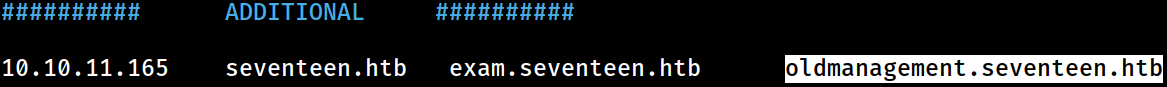 So I appended it to the
So I appended it to the /etc/hosts on Kali for confimation
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ curl -s -i http://oldmanagement.seventeen.htb/
HTTP/1.1 302 Found
date: Mon, 19 Jun 2023 22:14:35 GMT
server: Apache/2.4.29 (Ubuntu)
location: http://oldmanagement.seventeen.htb:8000/oldmanagement/
content-type: text/html; charset=iso-8859-1it indeed does exist, and it’s pointing to the earlier endpoint at http://oldmanagement.seventeen.htb:8000/oldmanagement/
That’s the web server running on the target port 8000
This must be the Student File Management System instance that I enumerated the DB of
oldmanagement
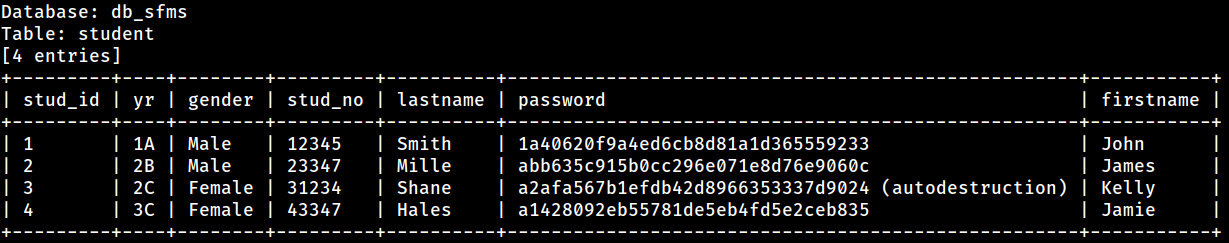
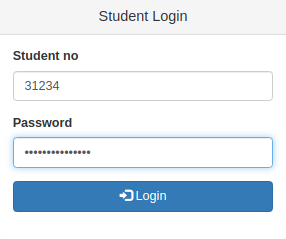 The credential table extracted earlier from the SQLi must be relevant to the login page here
I was able to crack the password hash for one of the user; Kelly Shane or student
The credential table extracted earlier from the SQLi must be relevant to the login page here
I was able to crack the password hash for one of the user; Kelly Shane or student 31234
The password is autodestruction
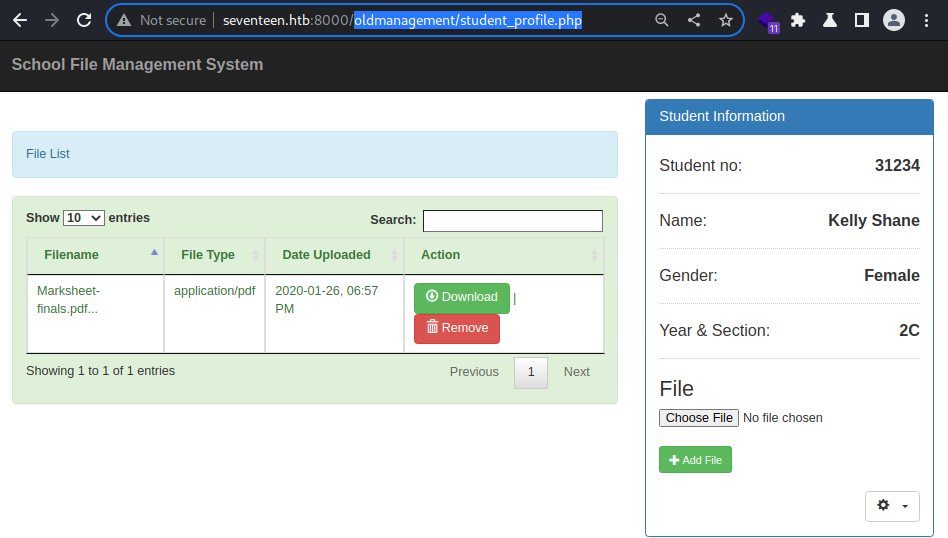 Logged in.
There is the PDF file that I enumerated earlier
I remember thinking about finding a way to extract the content of it through SQLi, which turned out to be extremely difficult if not impossible
However, now that I have logged in as Kelly Shane, I can just access that.
Logged in.
There is the PDF file that I enumerated earlier
I remember thinking about finding a way to extract the content of it through SQLi, which turned out to be extremely difficult if not impossible
However, now that I have logged in as Kelly Shane, I can just access that.
It’s also important to note that file upload seems to be possible.
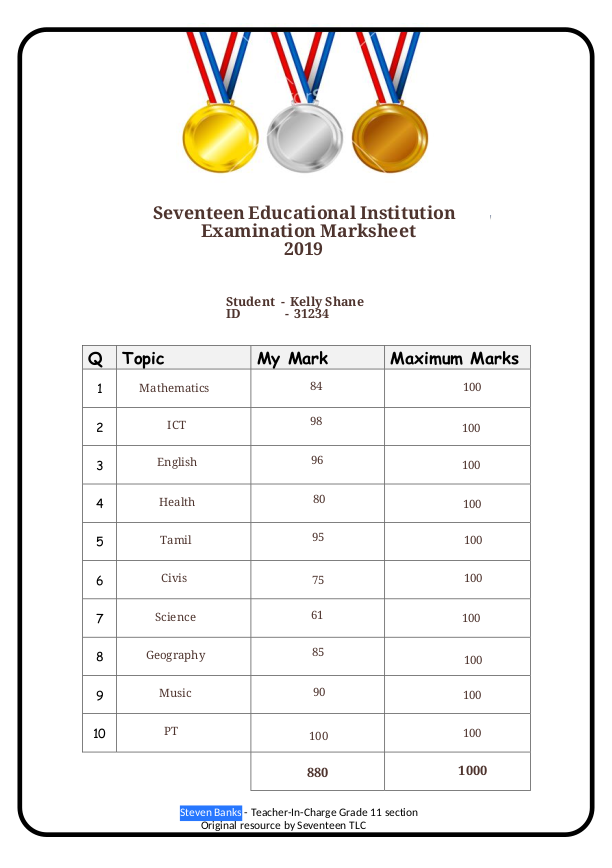 The first page of the PDF file is just a marksheet graded by Steven Banks
The first page of the PDF file is just a marksheet graded by Steven Banks
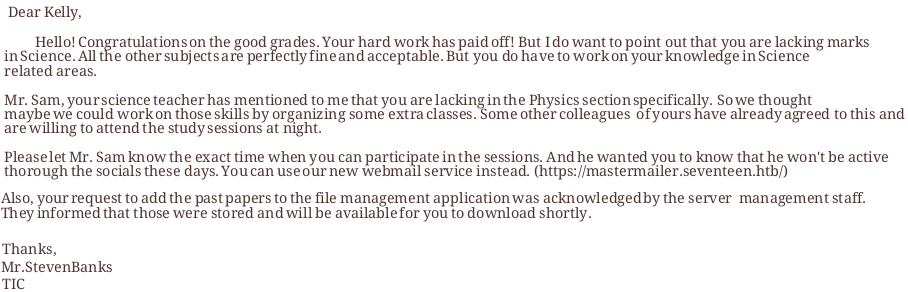 The second page is rather interesting. It’s a letter from the teacher.
the letter points out that the student is lacking marks in science, specifically, the physics section, and suggests to join the extra classes at night by confirming it via the new web mail service available at
The second page is rather interesting. It’s a letter from the teacher.
the letter points out that the student is lacking marks in science, specifically, the physics section, and suggests to join the extra classes at night by confirming it via the new web mail service available at https://mastermailer.seventeen.htb/.
This is likely the roundcube instance that I enumerated earlier
That is indeed a virtual host discovery Interesting part is that it seems to be hosted of HTTPS.
Nevertheless, the newly discovered virtual host needs to be enumerated
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ exiftool Marksheet-finals.pdf
exiftool version number : 12.54
file name : Marksheet-finals.pdf
directory : .
file size : 684 kB
file modification date/time : 2023:06:20 01:13:58+02:00
file access date/time : 2023:06:20 01:14:12+02:00
file inode change date/time : 2023:06:20 01:14:10+02:00
file permissions : -rw-r--r--
file type : PDF
file type extension : pdf
mime type : application/pdf
pdf version : 1.5
linearized : No
page count : 2
language : en-GB
tagged pdf : Yes
has xfa : No
author : Alison Banks
creator : Microsoft® Word 2010
create date : 2016:04:19 15:31:07+01:00
modify date : 2022:03:23 20:10:54+01:00
producer : 2.3.4 (4.2.15)The PDF file was created by Alison Banks. That’s another name.
 the footer reveals that it’s using school file management system 2019
the footer reveals that it’s using school file management system 2019
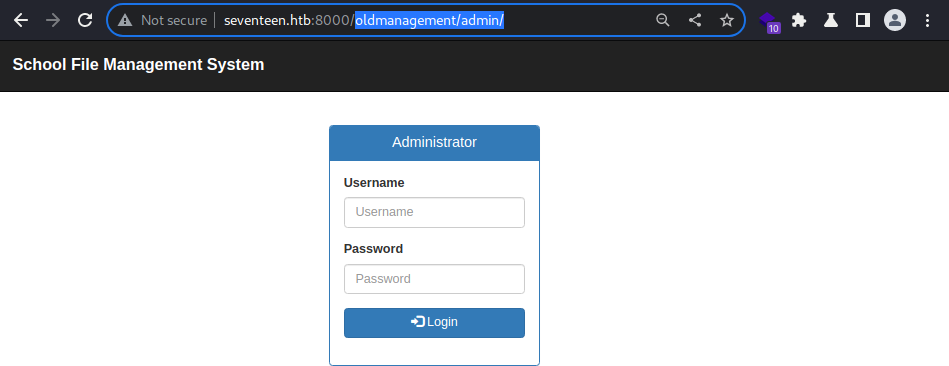 Admin login page is available at
Admin login page is available at /oldmanagement/admin
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ searchsploit school file management system -e
------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------ ---------------------------------
School File Management System 1.0 - 'multiple' Stored Cross-Site Scripting | php/webapps/49559.txt
School File Management System 1.0 - 'username' SQL Injection | php/webapps/48437.txt
------------------------------------------------------------------------------ ---------------------------------
shellcodes: No Results
papers: No Results