admin.blazorized.htb
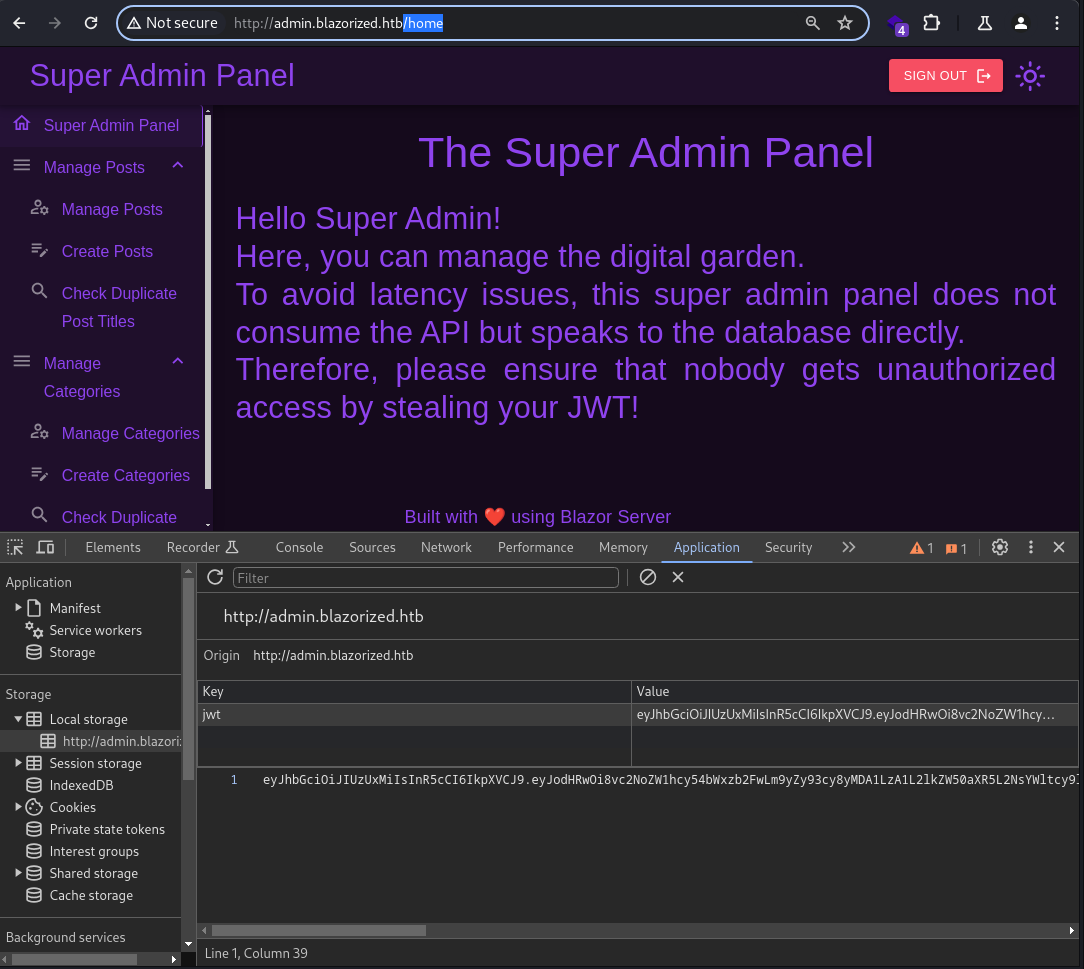 Successfully bypassed the authentication to the admin panel at
Successfully bypassed the authentication to the admin panel at admin.blazorized.htb, with a forged/tampered JWT
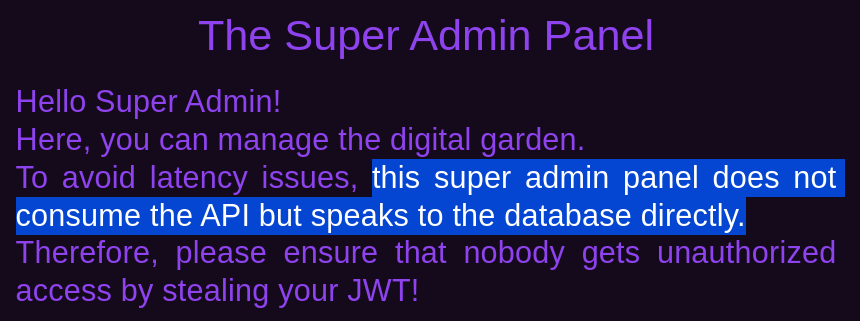 Ironically, the dashboard claims that the admin panel doesn’t use the API endpoint, but rather interact directly with the backend DB for “security purpose”
Ironically, the dashboard claims that the admin panel doesn’t use the API endpoint, but rather interact directly with the backend DB for “security purpose”
Manage Posts & Categories
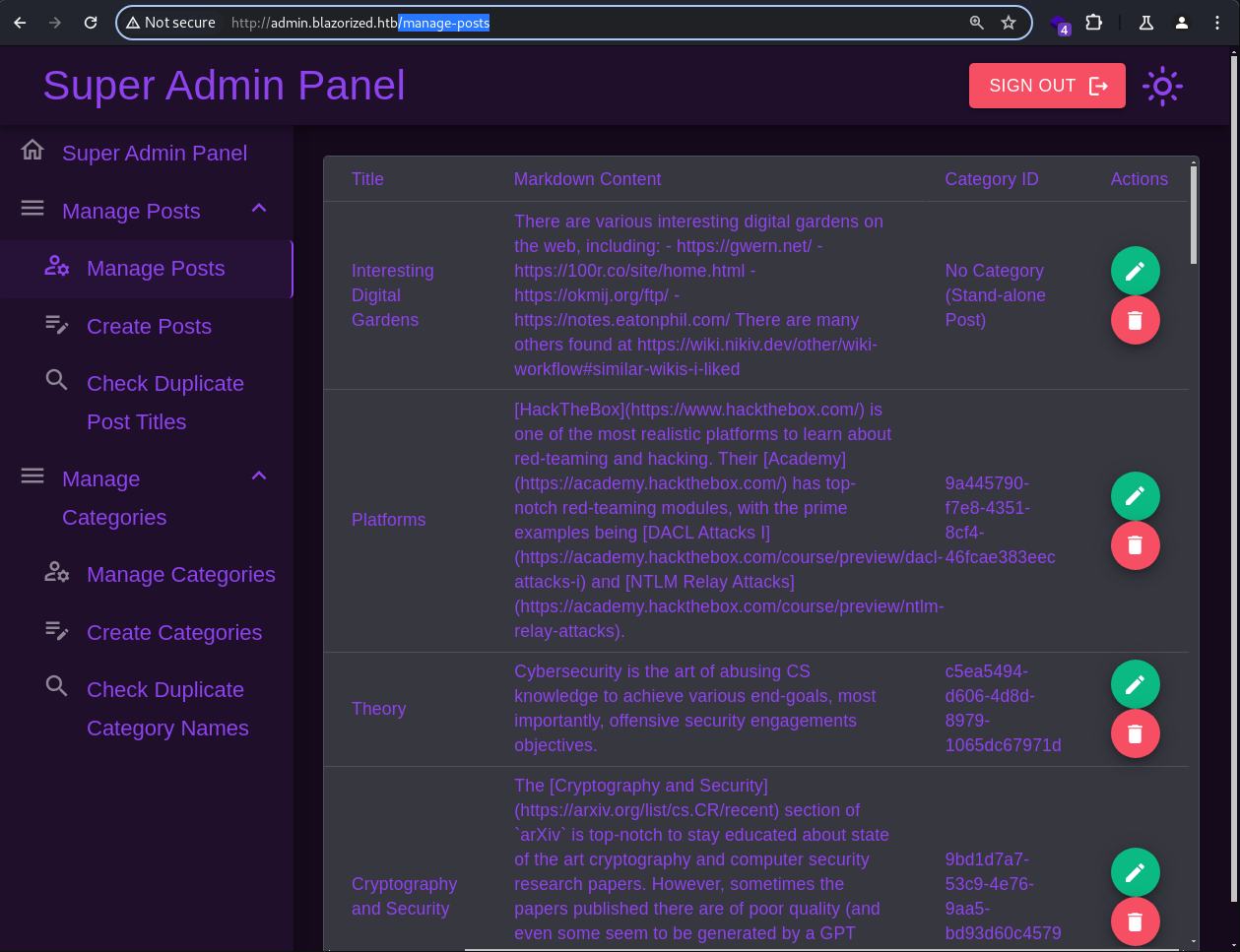
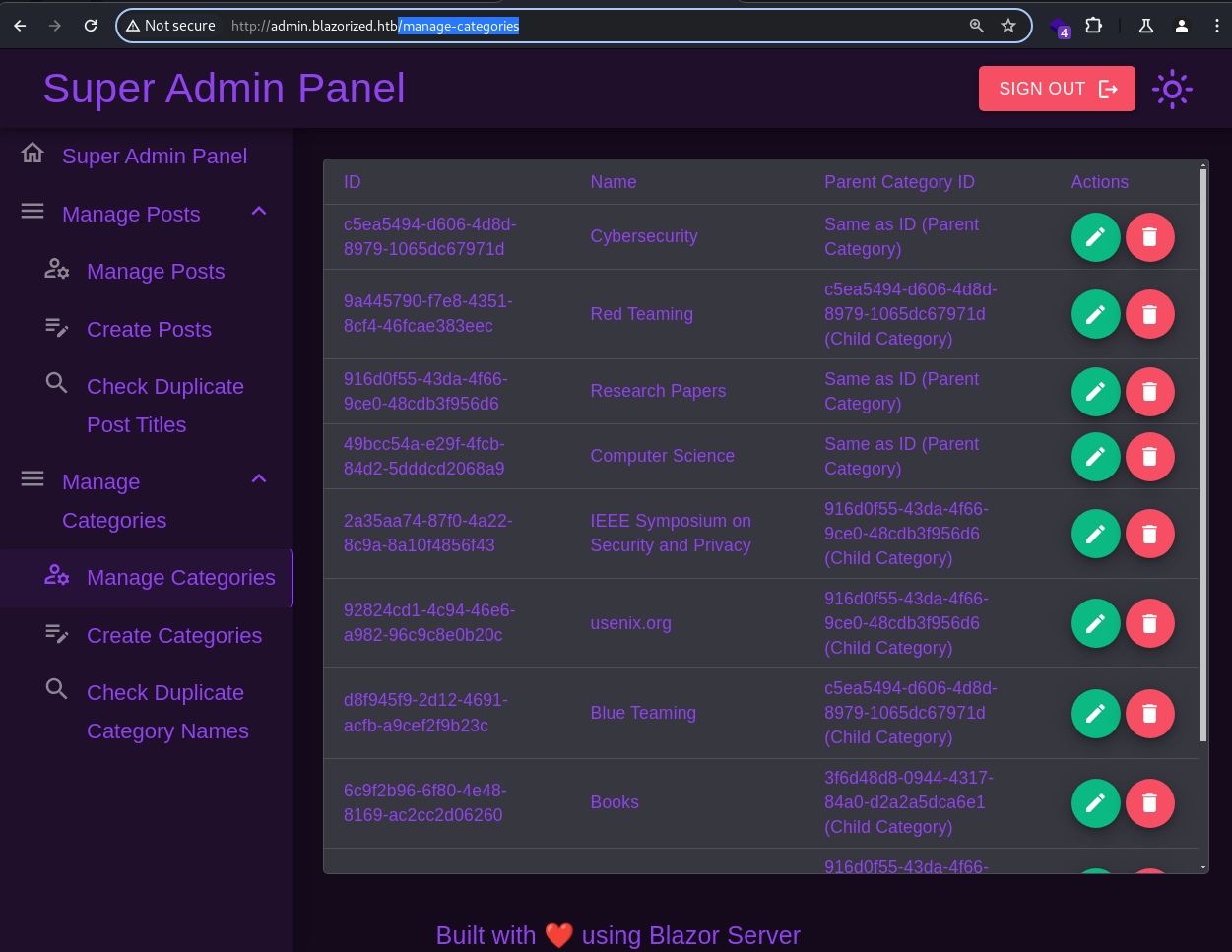 Both
Both /manage-posts and /manage-categories endpoints allow editing and deletion of posts and categories
Create Posts & Categories
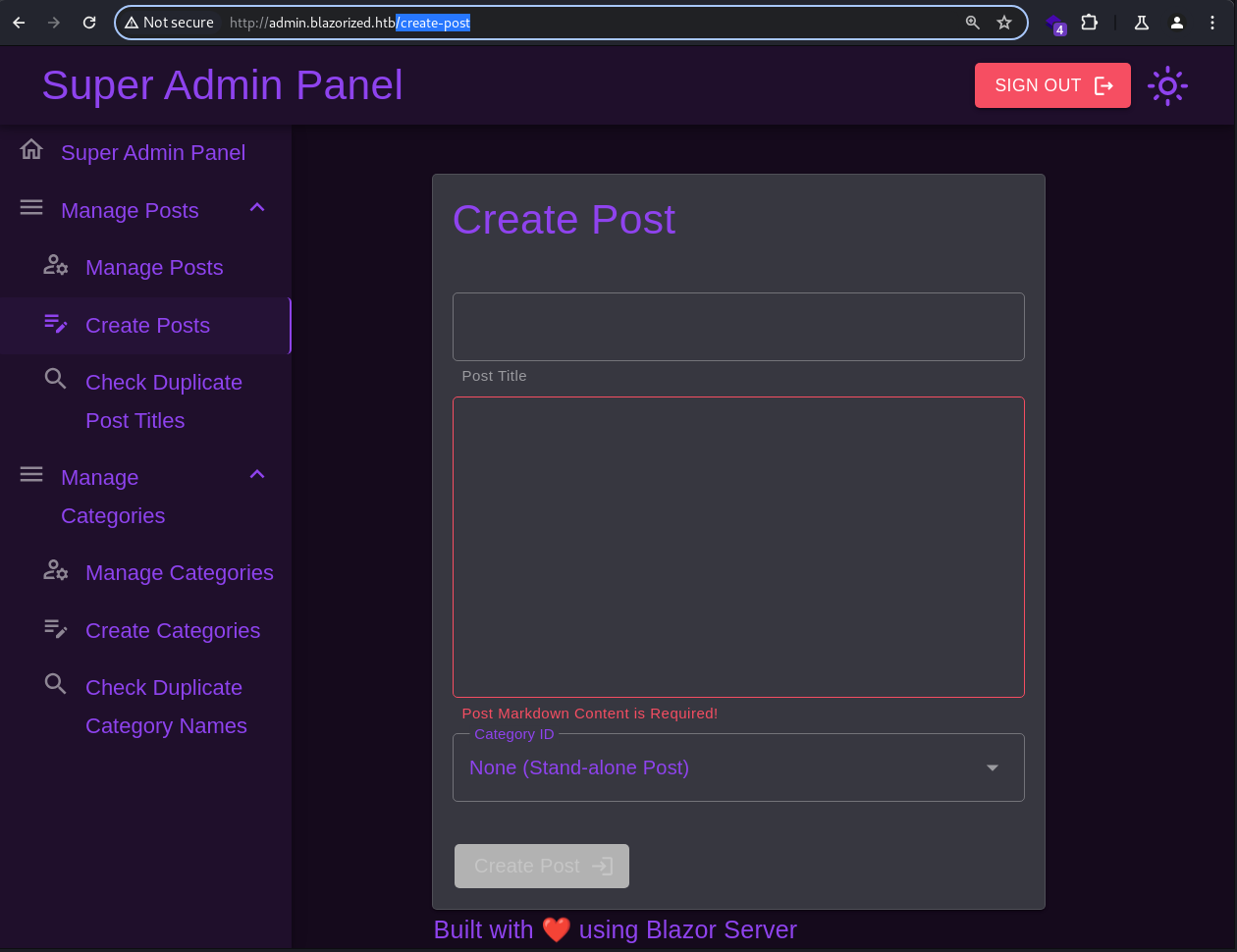
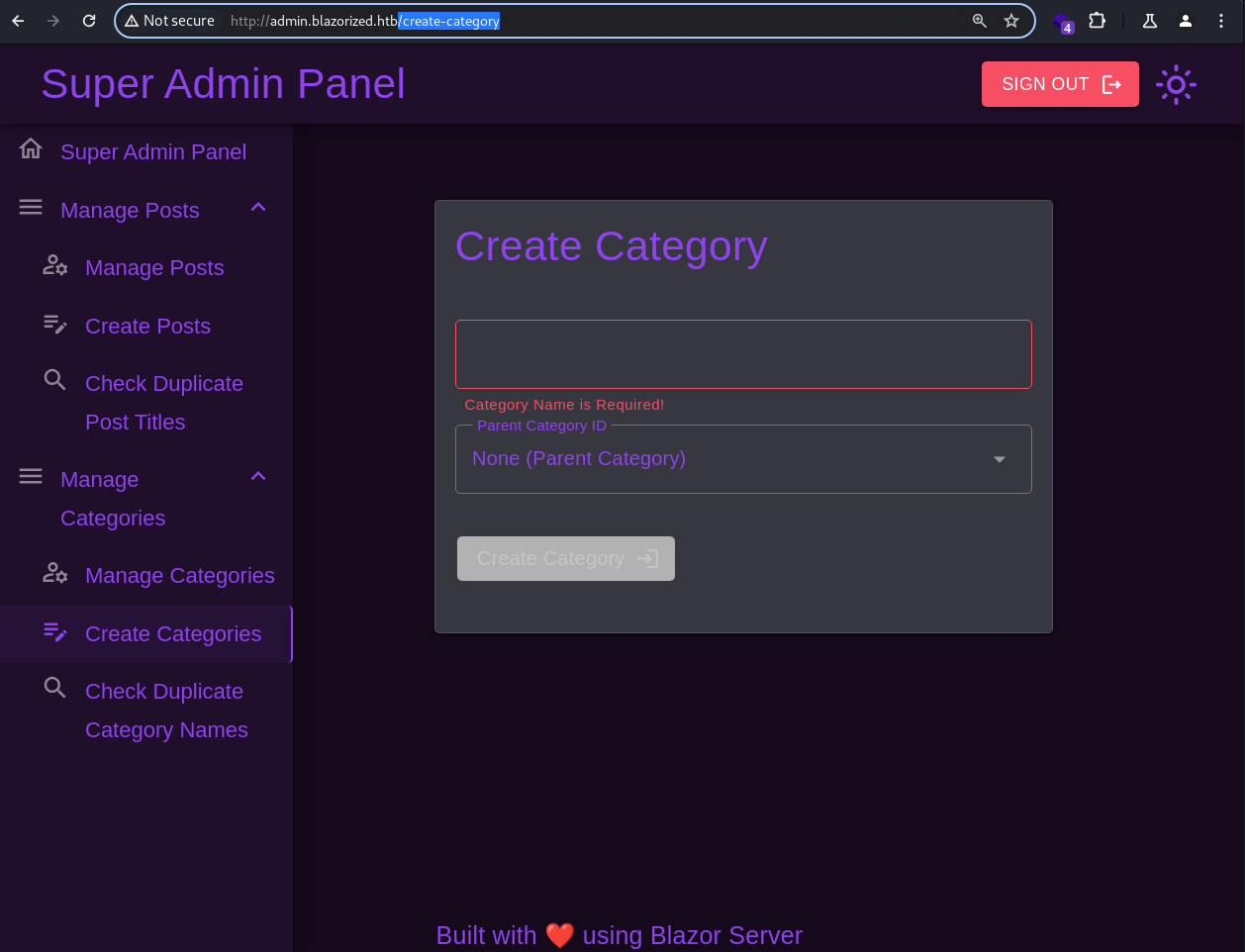 Creating Posts and Categories are possible through the endpoints;
Creating Posts and Categories are possible through the endpoints; /create-posts and /create-category
SQLi?
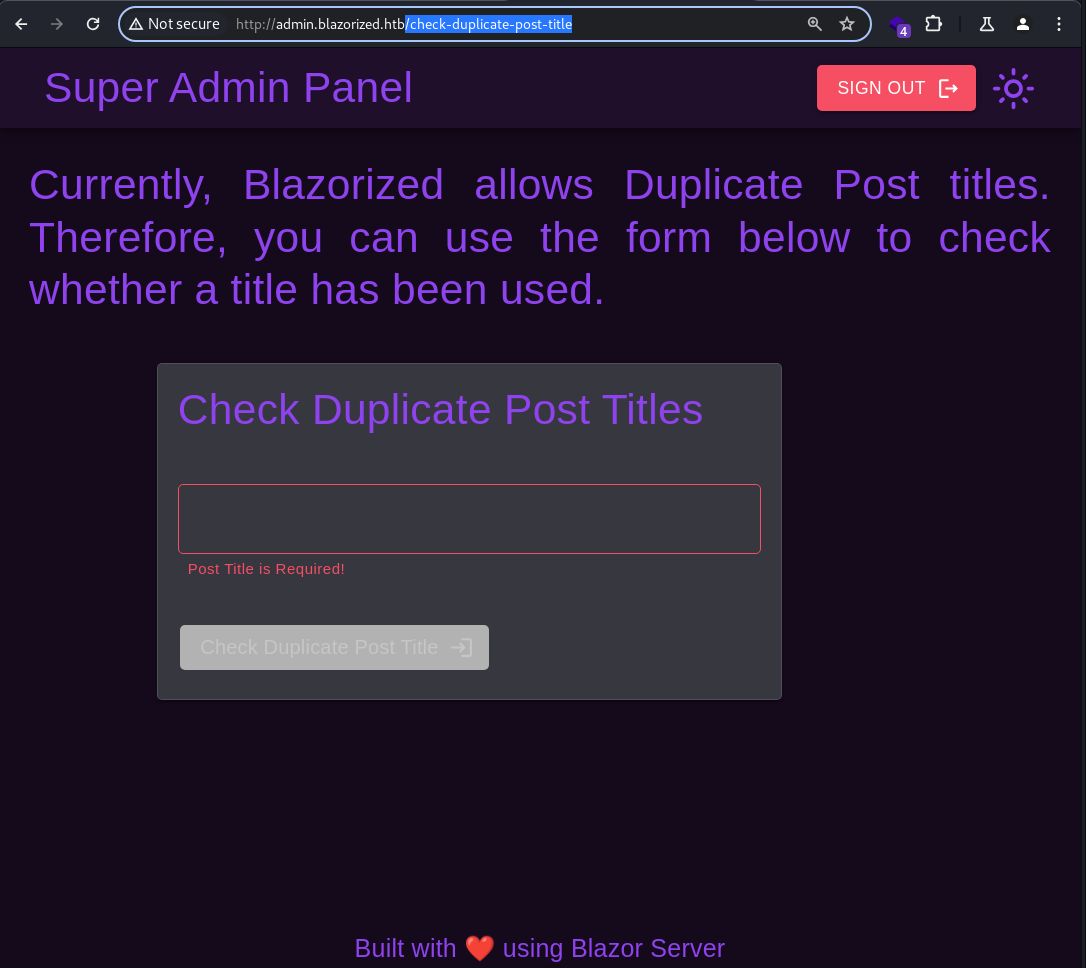 There is an endpoint where it accepts an user input to check for a title.
Since it’s mentioned in the dashboard that the admin panel interacts directly with the backend DB, this seems to suggest that there might be an SQL injection vulnerability here
There is an endpoint where it accepts an user input to check for a title.
Since it’s mentioned in the dashboard that the admin panel interacts directly with the backend DB, this seems to suggest that there might be an SQL injection vulnerability here
The backend DB is MSSQL according to the Nmap scan result earlier.
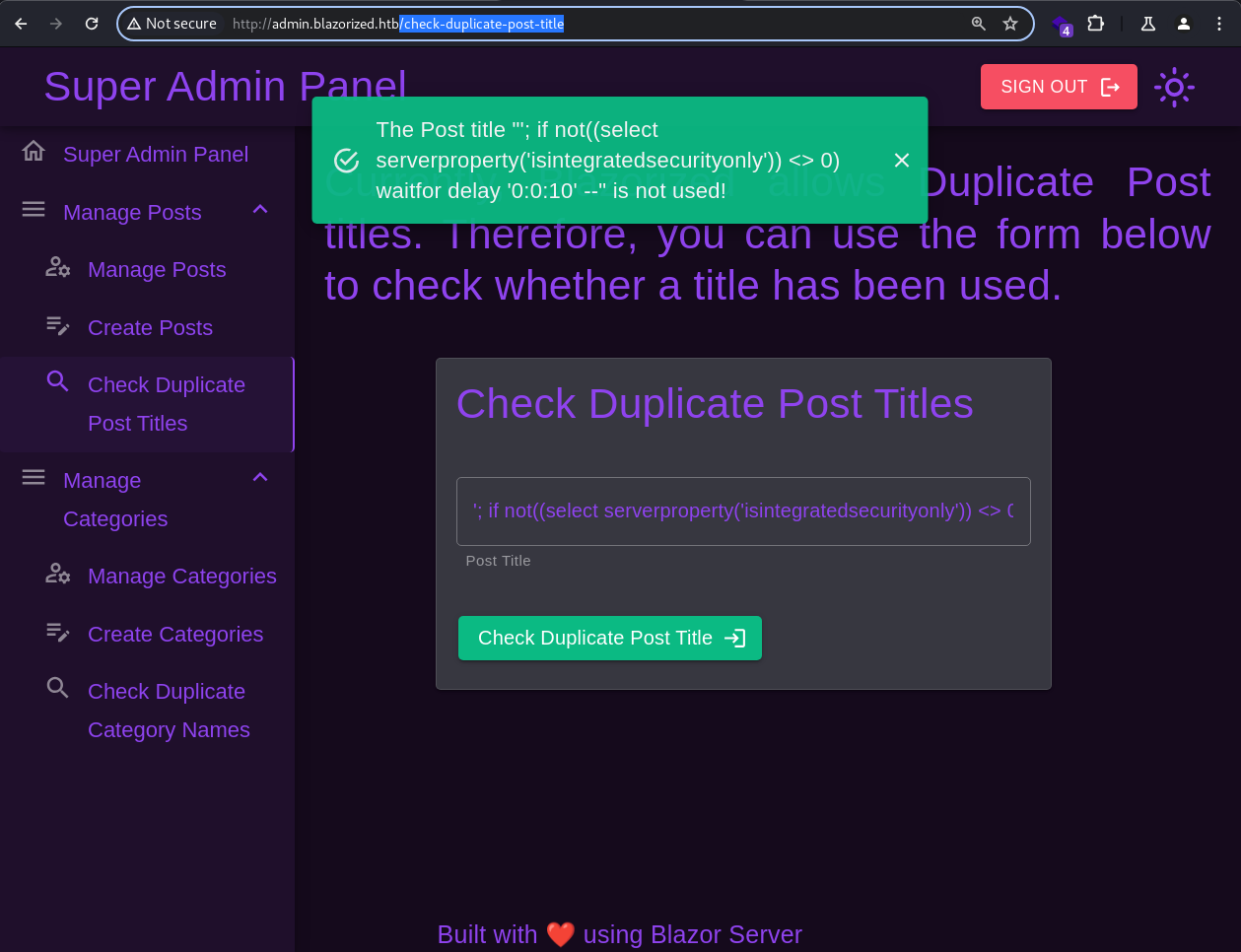 One of the MSSQL testing payloads for blind SQLi worked;
One of the MSSQL testing payloads for blind SQLi worked; '; if not((select serverproperty('isintegratedsecurityonly')) <> 0) waitfor delay '0:0:2' --
The web server took 10 seconds to respond
Moving on to the Exploitation phase