Web
Nmap discovered an known service on the target port 8065
While it is unclear what type of service that it is running, the scanned fingerprint shows that it is a web server
 Webroot
this is a login page and it’s hosting a mattermost instance
mattermost is an open-source messaging and collaboration platform designed for teams to communicate and work together in real-time. It offers features such as channels, direct messages, file sharing, and integration with other tools. Mattermost can be self-hosted or cloud-hosted and is highly customizable to meet the specific needs of different organizations.
Webroot
this is a login page and it’s hosting a mattermost instance
mattermost is an open-source messaging and collaboration platform designed for teams to communicate and work together in real-time. It offers features such as channels, direct messages, file sharing, and integration with other tools. Mattermost can be self-hosted or cloud-hosted and is highly customizable to meet the specific needs of different organizations.
 Earlier, it was specifically noted that users with the
Earlier, it was specifically noted that users with the @delivery.htb address is able to access the Mattermost instance.
I initially attempted to create a testing account, test@delivery.htb, through the support center by osTicket and it seemed to have failed as the account required confirmation
I also realized that a temporary email address gets assigned to a ticket.
So I have several email addresses ending with @deivery.htb at disposal. Some are restricted and some aren’t
Sign-up
 Attempting to sign-up with the initial testing account;
Attempting to sign-up with the initial testing account; test@delivery.htb
 Signing-up requires the account confirmation as well
Since I am unable to access the inbox of the
Signing-up requires the account confirmation as well
Since I am unable to access the inbox of the test@delivery.htb account, I won’t be able to verify it just like the support center by osTicket
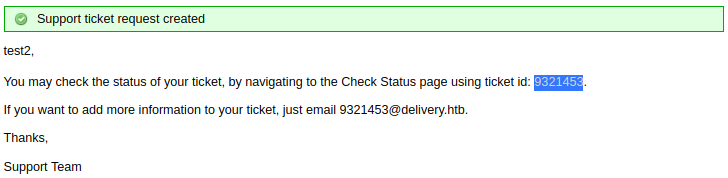 However, I remember that I was given a temporary email address for the ticket that I opened;
However, I remember that I was given a temporary email address for the ticket that I opened; 9321453@delivery.htb
I was then able to authenticate to the support center by osTicket as the “Guest User” account
 Then, I was presented to a communication platform where I tested for XSS. That just might be functioning as inbox. I should check that.
Then, I was presented to a communication platform where I tested for XSS. That just might be functioning as inbox. I should check that.
 For that, I signed-up to the Mattermost instance again, using the email address that I was assigned for opening a ticket;
For that, I signed-up to the Mattermost instance again, using the email address that I was assigned for opening a ticket; 9321453@delivery.htb
 Same thing here. It’s asking for email verification.
Same thing here. It’s asking for email verification.
 Back to the support center by osTicket.
Back to the support center by osTicket.
 In the communication platform or “inbox”, I can see that the verification email actually came through.
It contains the verification URL.
In the communication platform or “inbox”, I can see that the verification email actually came through.
It contains the verification URL.
 Navigating to the verification URL successfully verifies the email and completes the sign-up process
I should now be able to sign-in to the Mattermost instance
Navigating to the verification URL successfully verifies the email and completes the sign-up process
I should now be able to sign-in to the Mattermost instance
Sign-in
 Signing-in
Signing-in
 I am then presented with a prompt to join a team
There apparently is a team, Internal
I will jump right in
I am then presented with a prompt to join a team
There apparently is a team, Internal
I will jump right in
 This must be the chat for the Internal team
I see that the
This must be the chat for the Internal team
I see that the root user has sent 2 messages;
- while the first message contains a cleartext credential;
maildeliverer:Youve_G0t_Mail!, it also advises avoiding password reuse for those that are a variant ofPleaseSubscribe! - The second message points out that the password above isn’t present in the
rockyou.txtfile, but can be cracked through hashcat
That is some valuable information. I should test out the credential